
The First Step to Holistic Cybersecurity: Managing and Mitigating Risk
Assured Enterprises is a cutting-edge leader in holistic cybersecurity solutions. Their unique protective capabilities and risk management programs allow enterprises to measure and drive continuous cybersecurity improvements based on ROI.
Current Challenges
How does an organization identify and address risks inherent in its operating environment Reality:
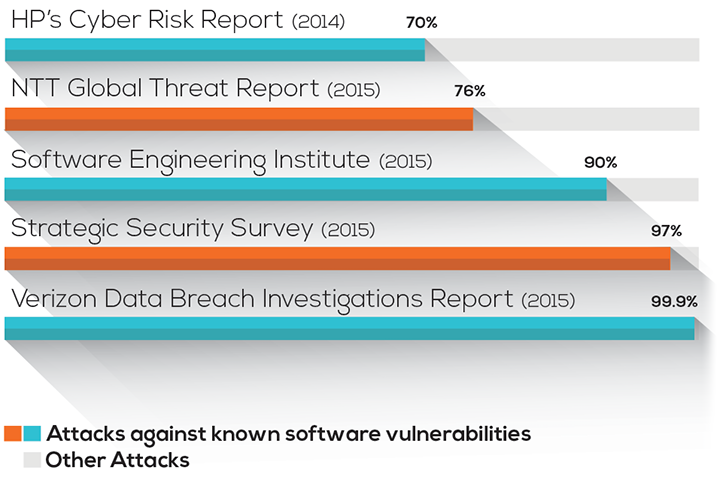
Some 80% of successful cyber-attacks exploit known software vulnerabilities, which were not easy to detect until now. Assured addresses these challenges with TripleHelixSM, its comprehensive cyber risk assessment system and with AssuredScanDKV®, the only tool on the market capable of detecting known software vulnerabilities buried within packed executables or the libraries and DLLs resident in software.
Holistic Risk Assessment and Detection Requirements
Holistic risk assessments start with a thorough understanding of:
- insight into the full scope of hardware and software issues, insider threats, network configuration gaps and known vulnerabilities;
- identification and analysis of external threats, impact planning and incident response;
- selection of cost-effective, ROI-driven risk-mitigation solutions;
- prioritized recommendations that allow self-corrective action at each level of the organization
— all within a framework which provides a reliable measurement and benchmarking that compares current cyber preparedness to improvement costs.
TripleHelixSM —all that and more
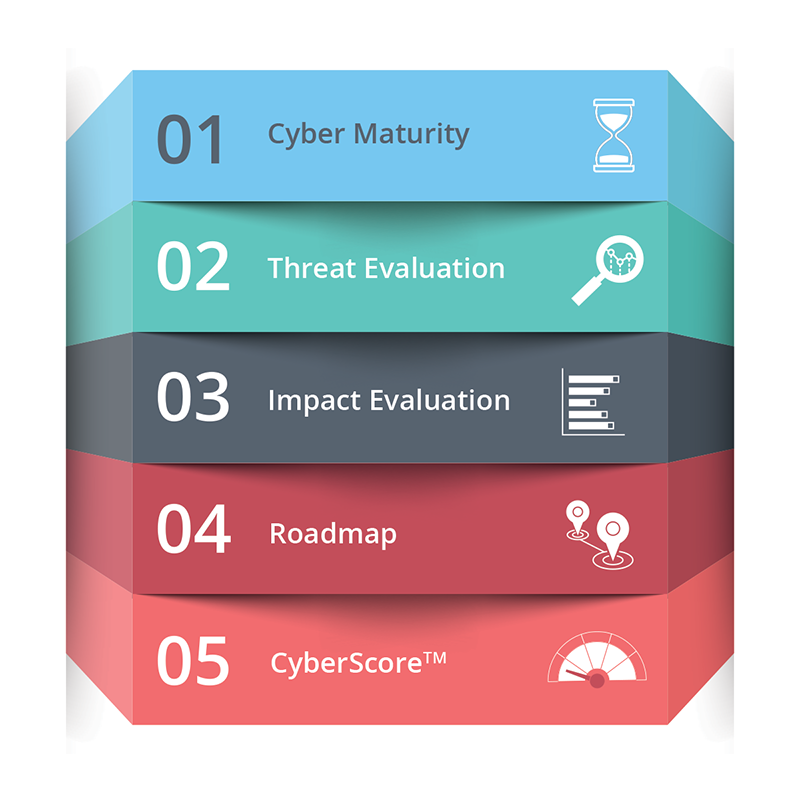
With granular detail, TripleHelixSM assesses cyber maturity, threats and impacts. Armed with these data points—many times more than others on the market, including the Big 4 accounting firms—Assured delivers a CyberScore™: a risk benchmark which measures the impact of changes to your environment and allows detailed comparison across organizations and operating units, not vague statistics about your industry.
Dealing with Noise in the System
What about all the regulatory, industry and good practices certifications, guidelines and compliance programs which already address cybersecurity wellness—systems like ISO 27001/02, PCI, ISF 2016 and so on?
Many of these requirements are limited, focused only on a narrow subset of information, designed to tick-the-box with the goal of completion, but with no better insight into the two essential questions: How do we cost-efficiently improve? And, how do we measure improvement over time and understand the value propositions associated with cybersecurity?
To deal with the noise, TripleHelixSM includes every certification, guideline and compliance program it can. Today, Assured has 18 such programs integrated into TripleHelixSM. These reports are available at the touch of a button along with a detailed improvement roadmap and a CyberScore™. Country- and industry-specific compliance certifications can also be easily added.
Known Software Vulnerabilities at the Gate
We know that most cyber-attacks are successful against known software vulnerabilities. Is it possible to detect and remediate known vulnerabilities lurking within software?
More Information here
Today, yes. Before AssuredScanDKV® you had to either be hacked and have the known vulnerability discovered during post-breach forensics, or hope that the original software developer discovered the known vulnerability in its source code and issued a patch before you are hacked.
With AssuredScanDKV® you can Detect Known Vulnerabilities within both proprietary and COTS software, obtain comparative risk levels for each detected vulnerability and receive remediation recommendations. AssuredScanDKV® is straightforward to install and doesn’t require access to source code or user data, lengthy training or configuration management. As with most scanning tools, the length of a scan depends on the number of files involved.
AssuredScanDKV® is available as a one-time run included in the TripleHelixSM assessment or as a subscription which allows frequent updating on either a single workstation or across an enterprise. Because hundreds of new vulnerabilities are discovered each week, the barbarian attacks at the gate are not going to be controlled without serious, holistic intervention.
Next Steps
For more on Assured’s solutions, contact them at www.assured.enterprises or schedule a demo today.
READ MORE
- Ethical AI: The renewed importance of safeguarding data and customer privacy in Generative AI applications
- How Japan balances AI-driven opportunities with cybersecurity needs
- Deploying SASE: Benchmarking your approach
- Insurance everywhere all at once: the digital transformation of the APAC insurance industry
- Google parent Alphabet eyes HubSpot: A potential acquisition shaping the future of CRM
