
Best cybersecurity solutions for keeping threats at bay
GLOBALLY, businesses have been upping their cybersecurity games in an effort to keep up with the evolving cyber landscape, as digital threats and risks become imminent. However, it might not be enough – cybercriminals are growing and evolving at an unprecedented rate through ransom tactics. According to Forbes, innovative malware is one of the top cybersecurity risks that Asia Pacific faces in 2017, along with website ransoms and DDoS attacks.
The Southeast Asian region is particularly susceptible to vulnerabilities, being a region that is vast and varied in terms of country status, economy, and development. Bloomberg BNA reported in January that gaping cybersecurity vulnerabilities in the region could even affect businesses all over the world. Analysts say region’s poor adoption of cybersecurity best practices and data protection laws are lagging far too far behind its citizens’ affinity to new mobile technologies.
Only three of 10 states that make up the ASEAN trade bloc have full data protection frameworks in place, according to a report on the digital economy of ASEAN by Deloitte – namely, Malaysia, Singapore, and the Philippines. The rest of the region has plenty of catching up to do.
Lyon Poh, KPMG’s cybersecurity partner in Singapore, told The Diplomat that Southeast Asia “still has weak governance in handling sensitive information”, making it a large target. “Regardless of what type of business, without investment in information security, can be a target of an attack. Delaying cybersecurity measures could cost businesses to lose US$3 trillion by 2020,” he added.
In light of such vulnerabilities, it is important for businesses both big and small to implement a comprehensive, well-rounded cybersecurity solution to protect their data in an increasingly boundary-less world. There is a great need for companies to stay on top of threats, and that requires a product that can help pre-empt and prepare for future cyber threats.
Read on to find out what our top picks for the most thorough cybersecurity solution providers that will help your business stay ahead.
CYBERARK
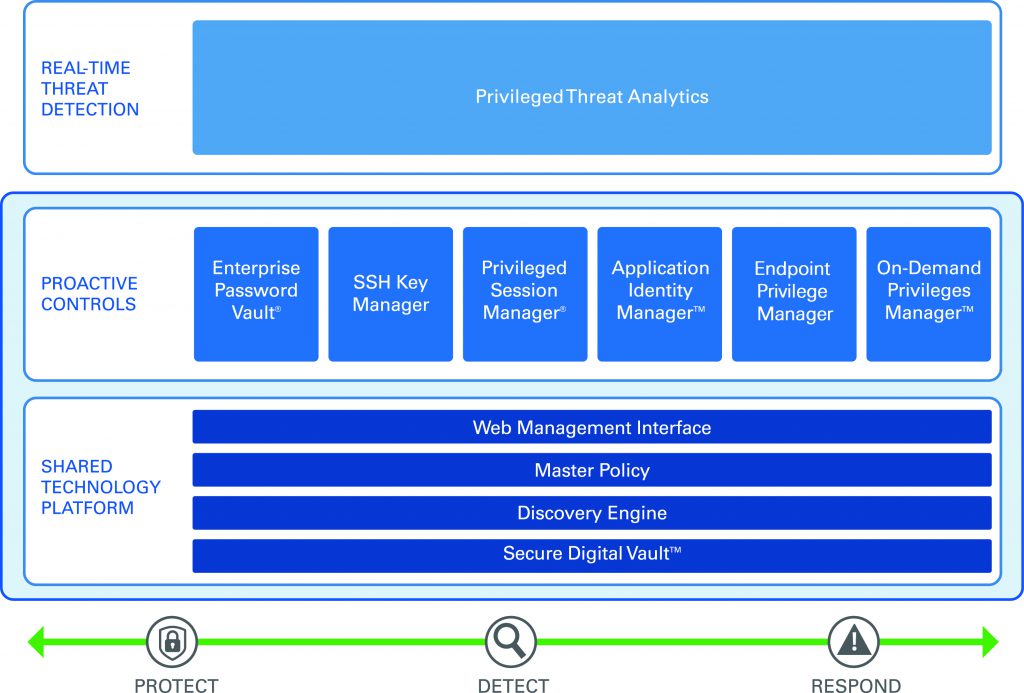
Image via CyberArk
The importance of having a cybersecurity framework in place is essential is these modern times, and organizations are beginning to understand that and seek providers that can offer them the best solution. CyberArk is one of these solutions – it is dedicated to striking down targeted cyber threats that “make their way inside to attack the heart of the enterprise”, so that enterprises can focus on running smoothly.
CyberArk’s main products are aimed at focusing on a company’s vulnerabilities and potential risks, and working to safeguard them against future attacks. Products include the Privileged Account Security Solution.
Privileged accounts include any accounts that enable access to an organization’s network, and can be found in the form of admin, root, SYS, or any other credentials that provide administrative access – and these accounts represent the largest security vulnerability any organization faces today, says CyberArk. Their security solution is therefore based on their Shared Technology Platform, which is a unified policy engine that provides scalability, reliability, and “unmatched” security for accounts of this nature.
Find out more about CyberArk here.
TENABLE

Image via Tenable
The Tenable platform offers specific technologies that are tailored to discover the presence of and assess the risk associated with emerging IT trends such as the use of containerization and the various cloud deployment models. These technologies allow Tenable to fully grasp the security implications of these trends and mitigate the risks accordingly.
Given that infrastructures are essentially organic in that they are in a constant state of change, monitoring must be performed on a continuous basis so that any changes to risk exposure are quickly detected and managed early on. Tenable does this by constantly and vigilantly monitoring an organization’s infrastructure so that a company is always one step ahead of attackers.
Tenable’s Technical Director for APAC, Richard Bussiere, said: “Tenable’s multi-faceted architecture and commitment to being both an on-premise and cloud-based solution offers a flexible and unique tool that helps clients manage risk.” The platform also enables visualization, which is the only way to effectively understand and mitigate risks in today’s complex hybrid network environments.
Tenable offers protection of up to more than 10,240 hosts, on any device including servers, laptops, and mobile devices. Products include Tenable.io, SecurityCenter, and Nessus, all of which are available on both the cloud and on-premise.
Find out more about Tenable here.
ORACLE
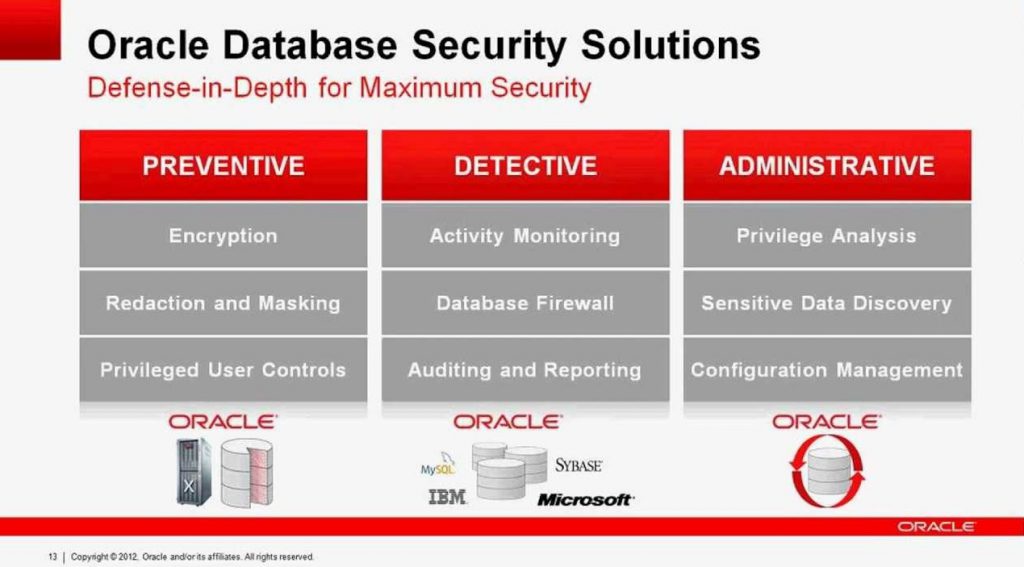
Image via Oracle
Oracle, the one of the world’s largest software providers, introduced its latest cybersecurity offering last November. Their new Identity-centric Security Operations Center (SOC) is an “identity and context-aware intelligence and automation solution” aimed at detecting and responding to threats and attacks on a company’s network. It also adapts and evolves together with the company and its needs, and works to protect users, applications/APIs, content, data, and workloads.
The company’s Identity SOC is the first of its kind in the world, and became a priority investment after Oracle identified a shift in customers’ needs alongside the security landscape that required more preventative actions to defend against current and future attacks. In a blog, Oracle’s Product Marketing Director Greg Jensen said: “Today’s threats now leverage multiple vectors, and breaking apart the attack sequence awareness of the attack chain is critical… Early detection is the key to containment, as today’s attacks no longer go on for just hours, they are persistent as networks, applications, and services can be probed for days, weeks, or months.”
The result is three new security cloud services: Oracle Security Monitoring and Analytics (SMA) Cloud Service, Oracle Identity Cloud Service, and Oracle Cloud Security Service. Together, the new systems and their integrations offer comprehensive security and actionable intelligence to ensure your business stays ahead of potential cyber attackers.
PANDA SECURITY
Image via Panda Security
As one of the 500 fastest growing companies in Europe since 1997 and part of Gartner’s Magic Quadrant Endpoint Protection Platforms, Panda Security’s award-winning technology has been integral to many companies’ networks for many years. Their Collective Intelligence tech is used by over 30 million customers in over 180 countries, and allows them to stay on top of cyber threats through community knowledge.
The technology involves users sharing malware-related information across all computers in a business’ network. Doing this allows Panda Security to provide real-time protection by identifying patterns of malicious behaviour and generating defensive strategies to counter known and unknown threats, says the company. All data obtained is routinely analysed, categorised, and correlated to make sure businesses are always prepared.
Panda Security claims to have blocked over two million security breaches in 2016 alone for over 12,000 corporate customers. The software goes through more than one terabyte of data every day that gets thoroughly scrutinized to identify all types of cyber threats, and covers more than a million endpoints and servers.
*Some of the companies featured in this article are commercial partners of Tech Wire Asia
READ MORE
- The criticality of endpoint management in cybersecurity and operations
- Ethical AI: The renewed importance of safeguarding data and customer privacy in Generative AI applications
- How Japan balances AI-driven opportunities with cybersecurity needs
- Deploying SASE: Benchmarking your approach
- Insurance everywhere all at once: the digital transformation of the APAC insurance industry
