
Breaching the DAM: How transaction management systems let assets flow freely
Like several areas of note in the history of computing, Digital Asset Management (DAM) first found its foothold in the creative industry.
From the early days of digital video & audio editing and storage, via the print and media design agency, and post-production environments the world over, it became swiftly obvious that large numbers of large files needed very careful management.
In part that was due to the very high relative costs of digital storage. But today, although petabytes of storage come cheap, the high numbers of digital documents we are all expected to interact with daily mean that the need to manage data continues. How many times have we all ‘lost’ files to colleagues’ hard drives, or been unable to locate important information in the cloud because of imperfect naming conventions?
DAM is known to have many advantages, among them:
- faceted classification
- canonical file versioning
- live sharing and updating
- auto-archiving
- standardization of file & naming conventions
- content and meta data search
Every organization should, if it doesn’t already, have at least a DAM policy in place; better, a full DAM implementation.
SEE ALSO: 4 reasons to invest in a Document Management System
But when data leaves the organization’s control, the best-laid plans of IT professionals can often fall to pieces!
Data has always traveled between organizations, although we may not have always considered it data. Physical acknowledgment of a Purchase Order by a supplier, for instance, may once have been received on paper. Digital transfer today reflects basically the same interaction, albeit at higher speed.
In commerce, the route of any piece of data is typically quite complex. Data (née paper documents) usually travels along a varying path, marked by waypoints, as dictated by an organization’s business processes.
At every stage of the data’s travel, there is room for corruption (but not necessarily data corruption in the IT sense): a change of format, a missed signature, a wrong invoice reference pasted, or even (heavens forbid!) a party in the chain who insists on paper copies.

Additionally, in security terms, authenticating the validity of those receiving, interacting with, and processing data is incredibly important: an illegible handwritten scribble in place of a properly authenticated digital signature can spell security nightmares.
Out-of-the-ordinary occurrences, security lapses, data corruption, format changes: all cause delays, and increase costs.
Digital Transaction Management (DTM) solves many of the problems that are caused once data leaves the walled garden of the enterprise’s data centers.
- instantaneous notification that data’s reached waypoint(s)
- data remaining trackable on route
- automatic remedial action taken if expected processes are deviated from
- preservation of data format & content
- bulletproof authentication and security
- true mobile working
- scalability
- workflow automation (submission, approval, confirmation, etc.)
What’s stopping your organization considering a DTM solution? Alarmingly, this survey reveals that in a 46% of organizations, it’s felt that the IT department is putting up the most resistance! This may be due to a number of factors that are worth considering:
- once data leaves the company, it’s ‘external’ and therefore no longer falls under IT’s remit
- data sent out by HR (for instance) is HR’s responsibility
- DTM doesn’t fit with existing policy
- mobile working on own devices (BYOD) is not approved
On investigation, however, most of those particular fears can be allayed by a deeper investigation. With that in mind, here are three suppliers of DTM software and systems we think you should consider:
DocuSign is known in the digital asset arena as one of the key players in the establishment of the xDTM standard, which allows organizations and consumers to undertake secure interactions online, with particular emphasis on availability, security, and privacy.
xDTM is managed by a governing board that includes DocuSign, Intel, FedEx, Microsoft, the US Postal Service and network & security giants, Cisco.
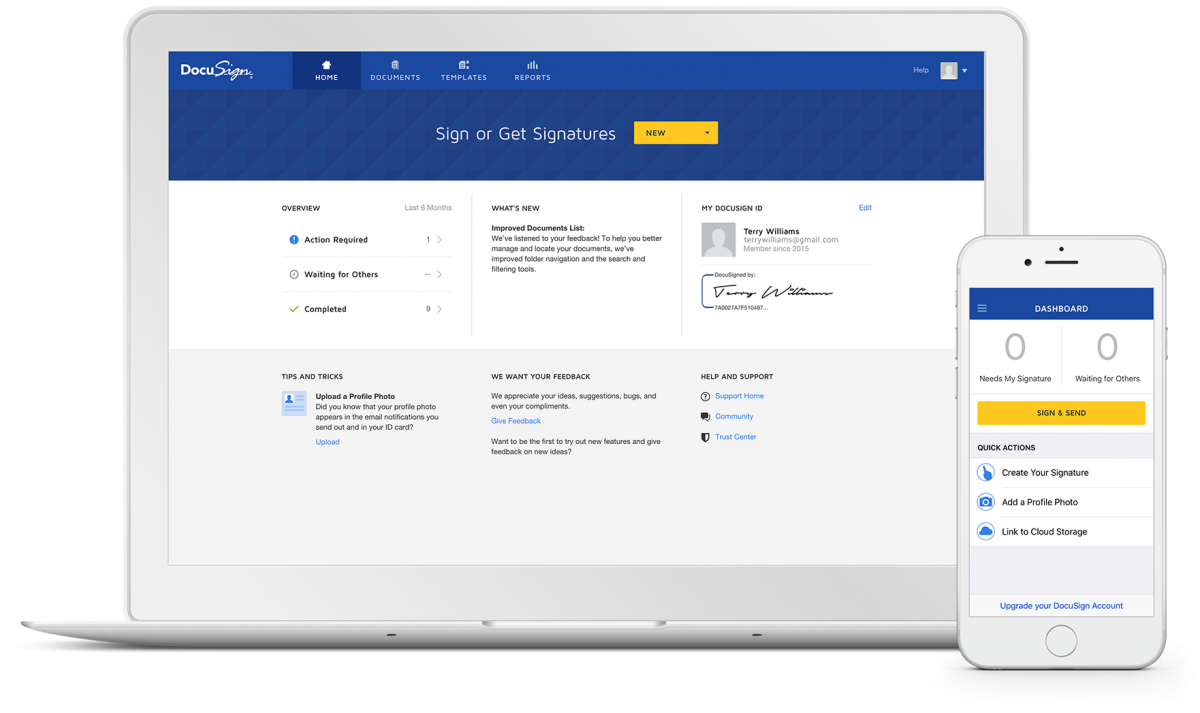
DocuSign products are therefore de facto reference points for many, and while its elevator pitch can be centered around electronic signature gathering, that facet is definitely a simplification of the cross-enterprise digitization that DocuSign solutions provide.
Their products offer a breadth of security, authentication methods, tracking, notification possibilities and system integration that give organizations a copper-bottomed method of total digital interaction. This extends to suppliers, partners, and customers (for the latter there are also payment options).
DocuSign supports most common file types and integrates with business apps like Salesforce, Netsuite, SharePoint, Google Drive, and Box, (plus there’s a full API) so upset to existing IT systems can be minimised and topologies simply extended to include the powerful digitization capabilities.
For the end-user in whatever part of the business process, actual interactions with digital documents are simple, quick and efficient. Documents can be sent from any device (office-based or mobile) to any number of recipients, with signature requirements embedded (and optional other information – phone number, for instance). This type of interaction conforms with what non-tech users are used to, yet hides underlying security and back-end activity that can power an entire organization.
Interested to see how DocuSign can help you accelerate your path to digital business? Sign up for a 30-day FREE trial.
Fluix is a cloud-based digital asset management system that is designed specifically for mobile teams. As well as storing files remotely, it also has elements of workflow automation, removing repetitive manual processes and freeing up staff time by the application of some IT ‘muscle’.
Functions include the ability to convert paper documents into digital files, which makes it ideal for systems integrators wishing to change working cultures in traditionally paper-based workplaces.
Compliance and security issues are addressed, with enterprise security and access control implemented. Data on route is encrypted, as you might expect.
SEE ALSO: Ensuring security in an application and network environment
Any file that’s digitally signed may be ‘sealed’ with a biometrically-encrypted key, which aids forgery prevention and allows security breaches to be easily tracked and weak points identified.

Fluix’s offering allows e-signatures’ use and these are taken by means of ‘signing’ with a finger or stylus. Once input, signatures can easily be reused in recurring places across documents.
As an additional security measure, the path taken by the finger/stylus is recorded as well as the relative speeds throughout the signing. This adds a further layer of security, minimizing forgeries which of course can only copy a signature’s style.
The platform also features form creation, PDF annotation and internal messaging.
Where in years past, you might send your operatives out onto the workshop floor or to clients’ premises with a series of forms attached to a clipboard, now you’d send the operative out with a mobile device and forms from Mi-Corporation.
The modular platform is available as either SaaS or in-house. There are several licensing and pricing models, with the price determined by numbers of users/total transactions; unlimited options are available at the higher costs.
The Mi-Corp client and the various Mi-Apps (running on iOS, Android, and Windows) allow easy form filling and data capture, including text, images, video, signatures, barcode contents and GPS information. Data can be stored locally (if the device is working offline) on an SQL Lite instance, and uploaded at a later time. Alternatively, data can actively sync with a remote host.
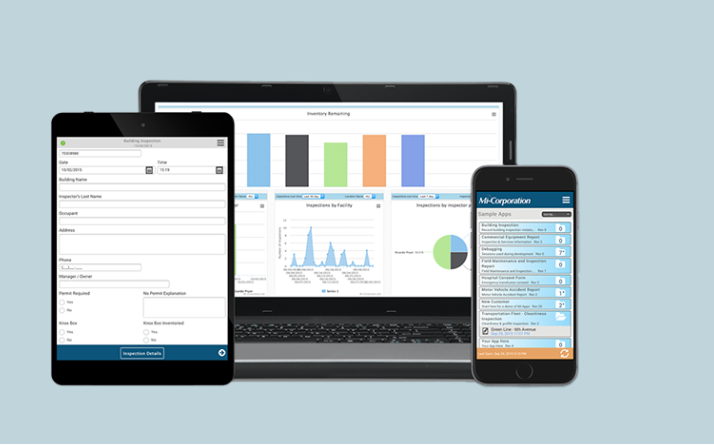
NextGen Designer allows custom form creation using a drag and drop GUI. It also offers creation of more complex forms, which can adapt according to given responses. This design application offers JS & VB.NET scripting for the code-capable who wish to extend the solution.
Back-end systems can be pre-existing or Mi-Corporation’s own server offering, and the API is available for integration with around 90 common systems. Administrative features include group management, granular permission settings, workflow planning, analytics, and password management.
READ MORE
- Ethical AI: The renewed importance of safeguarding data and customer privacy in Generative AI applications
- How Japan balances AI-driven opportunities with cybersecurity needs
- Deploying SASE: Benchmarking your approach
- Insurance everywhere all at once: the digital transformation of the APAC insurance industry
- Google parent Alphabet eyes HubSpot: A potential acquisition shaping the future of CRM
