
How to manage and protect your business’s endpoints from ransomware attacks, with FireEye

Cybercriminals, of whatever motive, are in the business of exploitation. Usually, there’s money in it, and sometimes, though it’s less sought after, prestige and power.
But whatever the motives, the methods used by cybercriminals are sophisticated, intelligent, developing and ever-shifting. Gains from a single instance of ransomware may be small, but scaled up and automated, the spoils are enormously profitable.
Today’s cybercriminals and nation-state attackers can bypass the traditional endpoint defenses that enterprise and governmental bodies have relied on since the internet’s rise to being commonplace back in the 1990s. Firewalls, antivirus software, and more recently, anti-malware software and anti-phishing browser extensions are still useful and relevant, but even when a traditional means of defense stops a threat, it can’t determine what the malicious code was attempting to achieve.
FireEye Endpoint Security (HX Series, currently) can be deployed on- and off-premises for endpoint security in the safe confines of the organization, or at large. The solution helps security teams detect and contain threats, but also understand their purpose, be that extraction of a ransom payable in bitcoin, or other ends.
Modern threats are technologically advanced, so to counteract this, FireEye Dynamic Threat Intelligence (DTI) can be deployed from the core network to all endpoints.
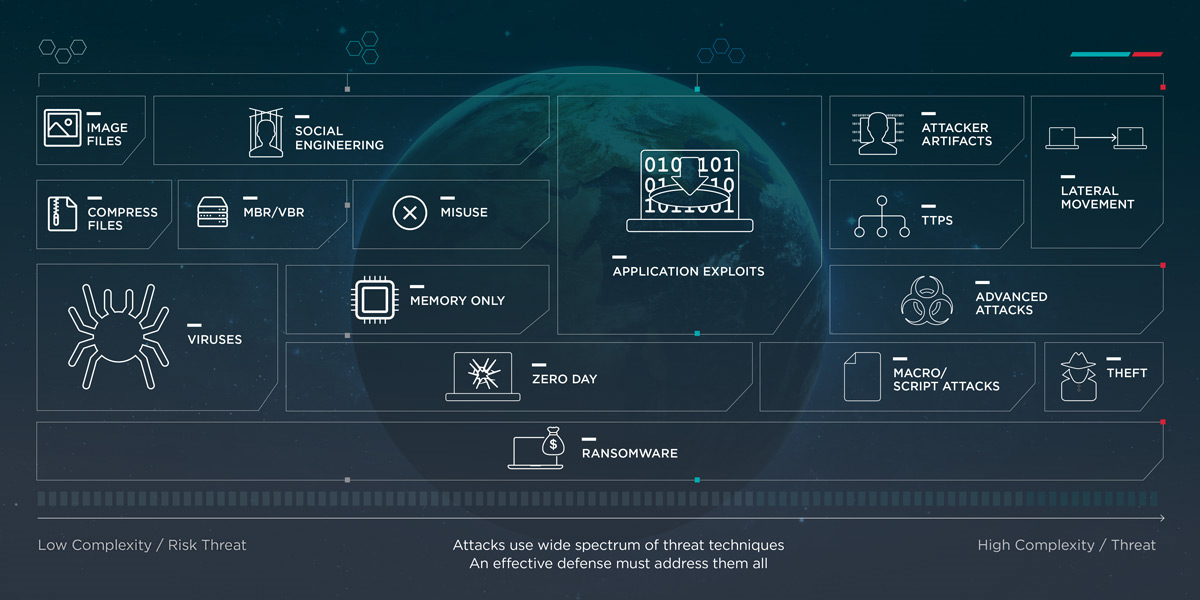
To be effective, the intelligence about threats must be present at the point of attack. FireEye’s security suite uses HX Endpoint Detection and Response (EDR) to extend the combined threat intelligence capabilities of the company’s offering directly to the endpoints.
If any of the FireEye products detects malicious activity anywhere across any part of the network, all endpoints are automatically updated and can be inspected. FireEye’s software allows tens of thousands of endpoints to be searched (whether connected or not) in mere minutes.
SEE ALSO: How passive endpoint protection can secure your digital assets
But key though the speed of deployment is in tech security, it requires an uncomplicated method of deployment. FireEye offers an assessment of all endpoint activities from a single interface to identify exploits, analyze them and either contain or negate them.
The ability of the software to push intelligence remotely lowers the overall data burden and requires no extra overheads caused by needing additional VPN connections.
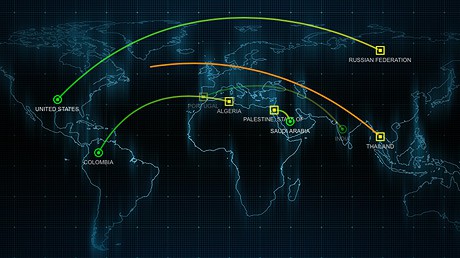
Of course, data on threats is shared across a network, but also to FireEye’s other clients. This process is reciprocated, making any installation much larger in terms of its data gathering than the organization it covers. The sum of all the parts forms a formidable barrier to any attacker, and will prevent the maximum number of system users being presented with a dread screen demanding cyber cash.
When a problem is identified and isolated or negated, the security systems from FireEye examine the problem to determine how the incursion was allowed, down to the detail of what an individual user was doing to cause the compromise. This data is shared and acted upon, in order to ascertain:
- how long an endpoint has been compromised
- if intellectual property has been lost
- what systems may have been affected, and how
Traditional endpoint protection systems have integral limits as they compare activity signatures against a relatively static database. However, FireEye’s solution gathers detailed information on areas that traditional methods may miss, by using FireEye-exclusive information to correlate multiple, discrete activities and in that way, uncover hidden exploits.
In order to benefit from FireEye’s advanced expertise and world-leading solutions, get in contact with a representative today.
READ MORE
- Ethical AI: The renewed importance of safeguarding data and customer privacy in Generative AI applications
- How Japan balances AI-driven opportunities with cybersecurity needs
- Deploying SASE: Benchmarking your approach
- Insurance everywhere all at once: the digital transformation of the APAC insurance industry
- Google parent Alphabet eyes HubSpot: A potential acquisition shaping the future of CRM
