
Why cybersecurity isn’t a static art form
WITH all the will in the world, no organization can be 100 percent protected from cybersecurity threats. Even given the most tightened-down network and stringent of security policies, no enterprise can ever be perfectly safe.
The oft-repeated cybersecurity adage is true: it’s not if you’ll be compromised, it’s when.
The role of a good IT department is a balancing act between empowerment and prevention: too much leeway given to staff and end-users, and security is too lax. Screw down the organization’s security too tight and staff can’t do their work effectively.
The weakest link in any security chain is, unfortunately, the lifeblood of any business – the people. Human beings have a terrible habit of causing problems for IT security teams. Fortunately, they have the mitigating factor on their side of keeping the business going, and if lucky, helping to make a profit.

Staff in the workplace today are tech-savvy to the extent that the previous generation could only dream of. And the reason for this is the ubiquity of technology in people’s lives, as epitomized in the enterprise by BYOD (bring your own device).
In order to help businesses ensure their security provisions are up to scratch, governments and quasi-governmental organizations provide guidelines and steps that can be taken to help ensure a safe-as-possible working tech environment.
For example, anywhere in the world, companies holding payment information need to be PCI compliant. The Australian Signals Directorate (ASD) gives guidelines for native Aussie companies, while in Europe and the US, people turn to well-respected organizations like SANS.org and CIS.org for guidance.
In some cases compliance is mandatory, and organizations need to prove that their activities fit the guidelines. But even if this is not the case, guidelines of this kind should be regarded as an absolute minimum in order that the enterprise does not suffer the impact of a serious breach.
In terms of the human beings in the workplace, the way in which staff interacts with technology is changing. While users but a few years ago would be limited to just using a company desktop or laptop provided for them, users today are not only bringing their own devices to work, but are expecting to use them in the same way as they might either at home or even during their commutes.

More alarmingly, technology’s ubiquity (exhibit one: the presence of how-to videos online) means that events like users setting up their own open wireless access points, bit torrent repositories or cryptocurrency mining operations are now no longer rare.
The challenge, therefore to the endpoint security team is much more complicated than it has been, but like the ASD Top 4, SANS Top 5 and any CIS guideline, there are standard steps which can be taken to ameliorate the potentially serious situation which many enterprises find themselves in.
Because of the widespread nature of technology (remote offices, home workers, extra-LAN access, VPN-like tunnels etc.), specialist software can hold the key to maintaining a grip on security.
To paraphrase the advice and stipulations from the bodies noted above, the steps to be taken are:
- Find out the extent of the network, and what hardware is on it (this changes over time as new devices present themselves)
- Find out what software is on the hardware discovered above, and determine whether it’s authorized
- Prevent unauthorized hardware and software access
- Make sure all authorized devices and their software is kept up to date and as secure as it can be
- Prevent this situation from being changed by unauthorized personnel
- Return to step one, ad infinitum
Here are three companies which Tech Wire Asia has direct experience of, who can provide security for the ever-shifting sands of endpoint security. To read more about them, click the company’s title.
IVANTI
The US-based security giant has a truly global reach, with presence and expertise in 23 countries, including China, India, Japan, Singapore, Australia, and New Zealand.
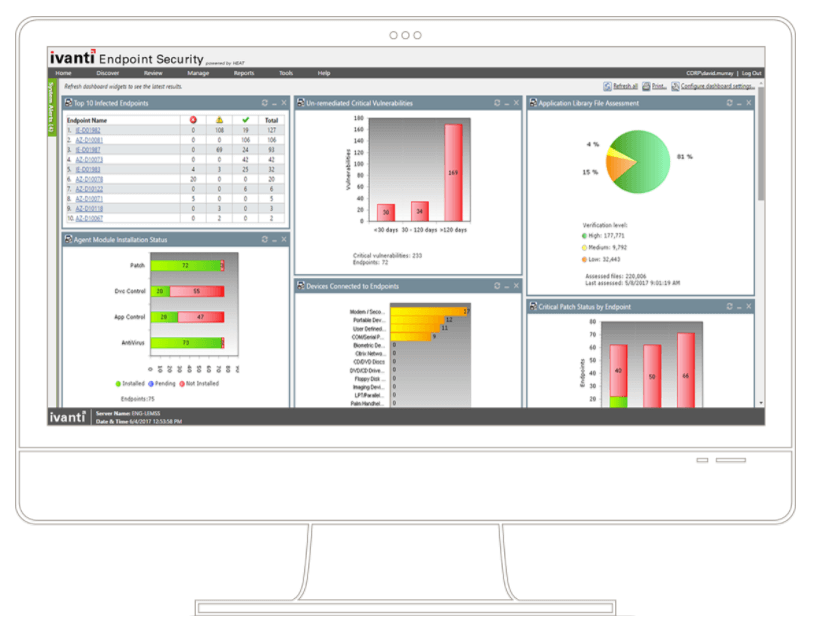
The company’s endpoint security systems can automate to whatever degree the organization requires: those with internal cybersecurity teams can drill down and control endpoint assets granularly, while automation from a single console makes hands-free operation an option for those that just need to get on with business.
Ivanti also combines second-by-second asset and network scanning/auditing with preventative systems based on privilege. Patches and updates can be pushed from a central console to OSes and third-party apps alike.
As the number and type of endpoints grow and change almost by the day (the new reality of cybersecurity), it’s reassuring to know that endpoints as disparate as embedded systems in IoT, Windows Mobile, Linux, and Mac are protected, as are the more run-of-the-mill Windows desktops, iOS, and Android instances. Even the most liberal BYOD policies can be handled with certainty, as can disparate networks comprising branch offices, remote workers, and various types of virtual dial-in, and network traffic types. Ivanti’s software aggregates the ever-shifting flavor of a modern network and makes managing, protecting, and healing it all, centrally, a breeze.
To read more about Ivanti’s offerings in particular, see this article.
SYMANTEC
Symantec is well known throughout the world, for all the right reasons (unlike one of its direct competitors, Kaspersky). As one of the key protectors of domestic IT, its name and logo are familiar to billions of users across the globe.
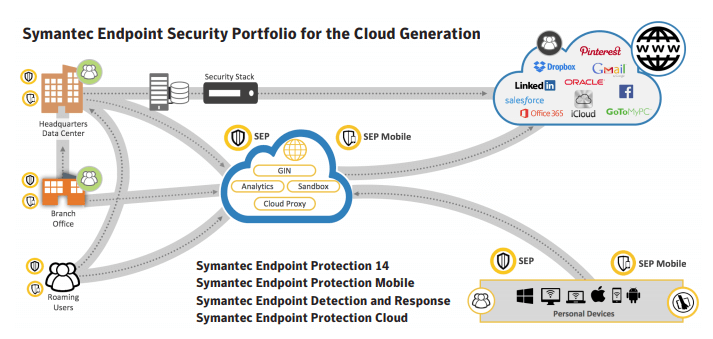
Symantec is also known as the world’s most trusted security certificate provider, ensuring that web clients’ traffic is safely encrypted and exchanged with protected sites.
The US-based company offers endpoint security as part of a wider range of security options which encompass most areas of technology in the enterprise. Its cybersecurity offerings protect PCs, Macs, Linux distros of most common flavors, virtual machines and even embedded OSes, such as those found in network devices like routers and switches.
Symantec’s marketing materials neatly invoke this year’s buzz phrase of machine-learning. Suspect files are referred to a platform which will run a virtual install of files, to ascertain whether or not they represent a threat. The release of a malware payload, for instance, triggers red flags before dissemination of threats takes place.
Symantec’s intelligence network is described as “the world’s largest civilian threat network”, and currently oversees 175 million endpoints across 157 countries.
The company keeps endpoint clients lightweight, and network chatter is kept minimal by, as an example, distribution of only the latest threat information. This reduces the size of signature file traffic by up to 70 percent.
FIREEYE
FireEye, like many providers, offers a broader service than just endpoint protection. The company offers a fully-hosted service, a bespoke, consultative service or a physical hardware installation of its security systems in its clients’ sites.
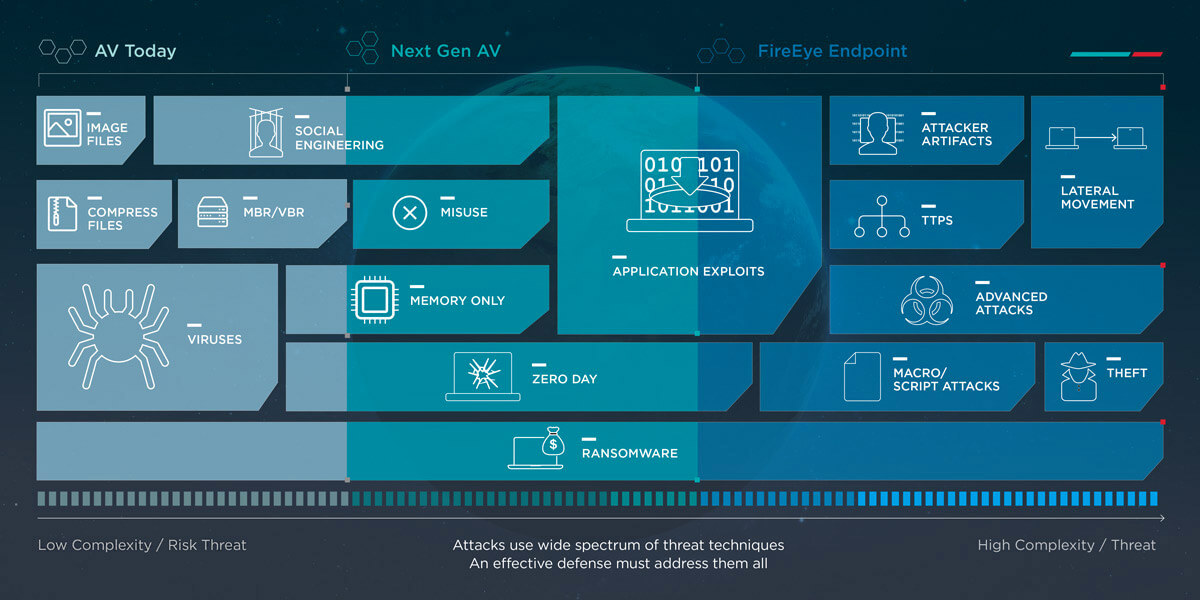
FireEye is one of the world’s largest cybersecurity providers and currently protects nearly 6,000 customers in 67 countries, including 40 percent of the Forbes Global 2000.
The safety in numbers of large providers works when one single endpoint is compromised, with FireEye’s service immediately updating all other endpoints across its network to the threat.
Anomalous activity is detected by the company’s audit and triage viewers, which act as the initial line of defense.
Once problems are identified, systems administrators in an organization’s cybersecurity team are alerted, who can either take manual action, or rely on FireEye’s automated remediation service.
FireEye uses the data gleaned from all its clients to update each other – security data is then shared by default with the rest of the world’s cybersecurity community.
READ MORE
- Ethical AI: The renewed importance of safeguarding data and customer privacy in Generative AI applications
- How Japan balances AI-driven opportunities with cybersecurity needs
- Deploying SASE: Benchmarking your approach
- Insurance everywhere all at once: the digital transformation of the APAC insurance industry
- Google parent Alphabet eyes HubSpot: A potential acquisition shaping the future of CRM
