
Preventing malware dwelling on the details: Endpoint protection with Carbon Black

WHETHER or not you’ve had any direct negative experience with them, it has to be admitted that malicious hackers are, on the whole, a pretty smart bunch.
It’s eminently possible to go online and purchase a few malicious scripts and see if there are any pickings to be had – the latest malware-as-a-service sites are springing up daily on the dark web, offering just that type of thing.
Most advanced adversaries will turn their noses up, however, at such simple techniques. There’s a certain credibility to be gained online by hacking well, for whatever reasons: political, social, or economic.
As a result, today’s cyberattacks, authored by people who have at least some degree of talent (albeit misused), can often bypass even the best cyber defenses.
And so, the enterprise wishing not to be affected negatively too often (successful attacks are an unfortunate inevitability) needs the means to detect malware and breaches rapidly and most importantly, be able to respond quickly.

There’s a great deal of noise on today’s networks (Set to get louder as more devices come online) and so identifying, isolating and remediating threats have become much tougher than before. And if your internal cybersecurity teams, or ones employed as third parties, don’t have the right tools or the appropriate procedures, then problems will loom large.
Those not versed in internet knowledge often imagine hacking to consist of frontal attacks on an organization’s internet point of presence, with something like a firewall facility as being the guardian of the gateway.
In many cases, it’s the devices with which we all interact every day which are the weak point in cybersecurity. Or, more accurately, we the users of these devices are the actual weak points!
Daily we are all phished, speared, coerced and conned, and while the reader of this site will be a lot less naive than most, who reading this article has never clicked on something which was a cybersecurity trap?
Endpoints in today’s enterprise range from low-end workstations and laptops (the older the OS, the more of a threat it poses, on the whole) right up to the highly secure cloud-based cluster. Not only are these endpoints growing in number, but they are becoming much more capable.
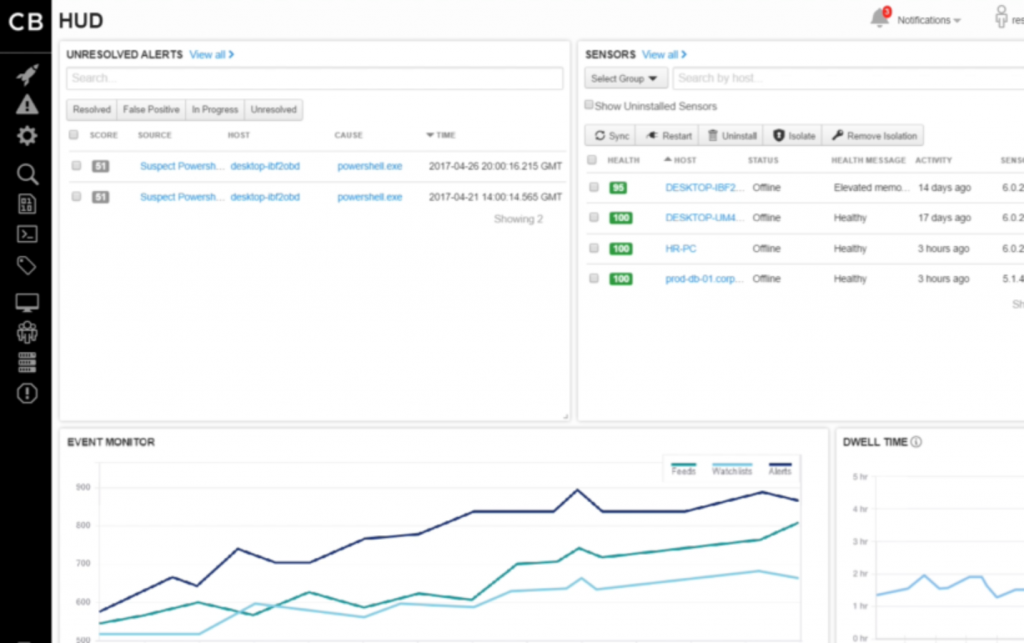
Cb Response from Carbon Black protects endpoints in use in the modern enterprise, and that includes laptops, tablets, desktops, used either on-premises, as part of a remote worker’s toolkit, or even carried onsite by external attendees to meetings.
Without adequate visibility for the variety of devices, the first line of security fails, and the network faces compromise and potentially massive data breach.
Carbon Black’s endpoint solution allows pro-active detection, investigation, and response to security issues, and provides a management structure which unites its own power with that of the rest of the security stack.
In any business connected to the internet, mere perimeter-based methods of protecting the network simply don’t offer enough. On average, most malware goes un-noticed for months, not minutes – the average “dwell time” for a piece of malicious code is an unbelievable 77 days.
While detection can take time, the traditional back-and-forth between general IT functions and security personnel doesn’t provide the speed of mitigation needed for malware stopping finding its most lucrative targets. Rather than the reactive nature of the incident helpline and its ticketing system, the modern enterprise needs pro-active hunting and immediate amelioration.

Cb Response lowers time between incursion to negation by up to 77 percent, and its lightweight sensors, available on every endpoint, protect each one from all manner of attack vectors: registry attacks, file-carried malware, process and network incursions.
All the while, the solution continuously collates and centrally stores data, so even if the source of a problem is identified but then is not available or goes offline (taken offsite or powered off), the data remains, allowing the SOC team to quickly prevent the problem spreading and causing more damage.
The incident response and security teams using Carbon Black Response benefit from aggregated info sec feeds, attack pattern detection, and if any other party in the Carbon Black customer base is attacked, the whole community learns the new incursion method in seconds.
With a range of APIs, the solution from Carbon Black can integrate smoothly with the rest of existing cybersecurity methods, making endpoints – the most dynamic threat source – as safe as “traditional targets” such as sensitive databases or e-commerce facilities.
Security officers can avoid being held “to blame” for data breaches by taking proper precautions, and the latest generation of endpoint protection systems from Carbon Black goes a long way to ensuring that is the case.
For more information on Cb Response and how it can help protect your organization, get in touch with a Carbon Black representative local to you.
READ MORE
- The criticality of endpoint management in cybersecurity and operations
- Ethical AI: The renewed importance of safeguarding data and customer privacy in Generative AI applications
- How Japan balances AI-driven opportunities with cybersecurity needs
- Deploying SASE: Benchmarking your approach
- Insurance everywhere all at once: the digital transformation of the APAC insurance industry
