
Microsegmentation at a massive scale: the Illumio cybersec platform

The role of IT in the enterprise, and especially that of IT Security personnel, is often misconstrued as being obstructive, rather than enabling.
Historically the IT function’s purpose was to establish “normal practice” and then enforce that locally (to prevent ingress at the level of the end-user or single server instance) and at the perimeter, with intrusion detection, firewalls, and packet inspection technologies.
Recently, the availability of cloud compute and storage has meant the IT picture, especially with regards protecting the enterprise’s assets, is a great deal more complicated. Establishing a practical protective strategy that allows the type of technological agility that today’s businesses dictate can be done, of course, but implementing any policies at scale is a massive drain on resources. Datacentre firewalls are expensive, slow to modify and manage at scale, and — let’s be frank — difficult to configure properly in a coherent, structured manner that’s fully concordant right across complex hybrid networks.
There remains still a certain lag in intention to deploy, and the realization of the resources that are needed; that’s often down to having to manually re-architect security policies which at a practical level are represented by thousands of instances of many hundreds of lines of deny and permit rules. The nature of that reality is that if a production service fails or falters, re-tasking resources from, for instance, QA and testing, is not as quick as is usually desired. Or, if it is as fast, the danger is that the deployment may be unsafe.
In fact, the most common security stance remains “permit and pray”: fingers crossed that a) apps don’t break, somewhere, somehow, and b) there are no doors left wide open.
Software-defined networking, compute and storage have enabled enterprises to use their technology resources according to business need, removing the barriers that existed between differently-hosted services and apps: cloud-based, on-premise, distributed or centralized, abstraction offers enterprises a theoretical lack of limits on speed and deployment combinations.
Convergency-based technologies are powerful, but aren’t designed as security measures, although many are used as such. In general, though, security, safety, reliability and (increasingly) compliance tend to throw the brake lever firmly “on” when the business wants to roll out new apps and services, or make changes to topology.
Despite a natural and (quite correctly) conservative approach to maintaining a secure environment in the enterprise, bad actors still succeed in establishing themselves, moving laterally, often in-memory and after long dwell times. That puts information security at risk and threatens to remove compliant status with extant legislation.
The Adaptive Security Platform (ASP) from Illumio is changing the security picture to one where micro-managed control can be wielded over individual networked server instances, for example, by means of host-based segmentation. Illumio terms what’s often referred to as microsegmentation, as security segmentation. For the enterprise, security segmentation means several things:
- Bad actors are contained in much smaller network segments where they can be more quickly remediated, with fewer consequences across the enterprise WAN.
- The ASP platform allows real-time network mapping and exposes
- The same platform can co-ordinate and distribute tested security policy measures that are as close to the applications they protect as is possible to be: on the same host.
- There are massive savings in resources freed up by having no need to micro-manage security measures on the many hundreds of security devices across the network.
- A few dozen Illumio rules effectively replace many thousands of firewall rules.
- Changes to security measures caused by topology changes are in place in seconds, not days.
The underlying model of the Illumio solution was what first attracted Brian Chess of Oracle NetSuite:
“Illumio has a brilliant fundamental insight: The software that all of these servers need to protect themselves is mostly already there — it comes with the operating system. The Illumio Adaptive Security Platform activates and intelligently controls the stateful firewall available in the compute layer: iptables for Linux or the Windows Firewall Platform.”
In large enterprises whose IT networks cross continents, CTOs and other IT professionals are using Illumio’s ASP to help protect in a way that is application- and service-centric. Whether critical systems are in the cloud, in-house, or in data centers anywhere in the world, the single solution covers every instance. Illumio’s Virtual Enforcement Nodes provide granular metrics to the central Policy Compute Engine, and according to policies distributed by the PCE, enact measures on each host in seconds.
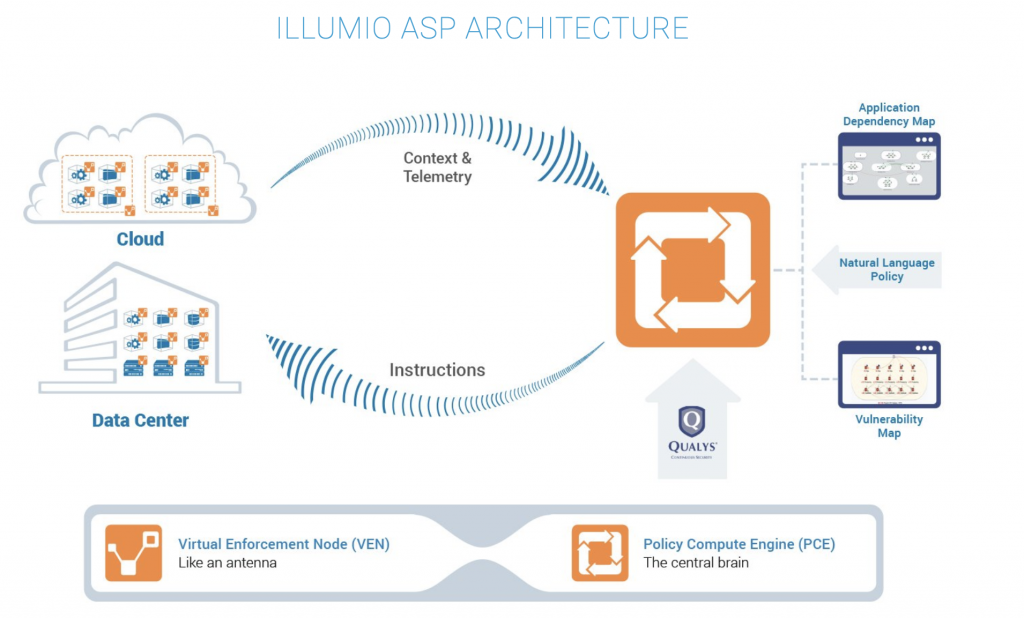
Source: Illumio
The Illumio stack lets cyber security staff model and test policy too, before any deployment. Any change can be trialed so no apps break, no services falter, and no new threat surfaces get exposed.
The central control unit that is the PCE can be hosted by Illumio, or installed in-house on bare metal or hypervisor, or hosted in public cloud(s) — at any scale, in any combination. Customers deploying ASP across mixed topologies are delighted with the platform’s power, scalability, and level of granularity the framework offers. Joe Burton of Plantronics went on record to say:
“Illumio represents a transformational approach to providing security for the cloud. When we became familiar with Illumio’s solution we got quite excited, because of its ability to set the right profile and then as more machines come and go within our cloud, Illumio grows with them and eliminates all of that static configuration time—all the while providing even more protection than we were seeing with other solutions.”
Creative Artist Agency’s Jeff Blair was able to put his finger on the concept behind the Illumio platform, which he summed up as: “The thing that really sold us on Illumio was the ability to separate out the control of security from the enforcement of security […]”
Without the type of granular approach to cybersecurity that microsegmentation offers, the outliers and the edge-cases are the ones that will cause enterprises not protected this way problems that can quickly spread right across the enterprise WAN. With powerful, broad-sweeping security policy implementation managed centrally, yet protection on a granular, per-machine basis, issues can be isolated to tiny network segments and remediated quickly, with little impact on the business.
Learn how Illumio can help your large enterprise WAN get the type of data security and compliance that will let business-focused IT work as quickly and thoroughly as it should: download this whitepaper for more details.
READ MORE
- Ethical AI: The renewed importance of safeguarding data and customer privacy in Generative AI applications
- How Japan balances AI-driven opportunities with cybersecurity needs
- Deploying SASE: Benchmarking your approach
- Insurance everywhere all at once: the digital transformation of the APAC insurance industry
- Google parent Alphabet eyes HubSpot: A potential acquisition shaping the future of CRM
