
Until people stop making mistakes, there’s DNSWatchGo from WatchGuard

For cybercriminals, hacking is a numbers game. Like most people, hackers want results from their “work” with the least possible effort.
Instead of carefully constructing original code that gets round your company’s barriers on the perimeter of the network (like firewalls, intrusion detection systems, packet sniffers, and the like), it’s quicker, easier and proven to be more effective to target the people that work for the business.
Hackers rely on people making mistakes, and one that’s very, very common is “happy clicking” — tapping or clicking a link in an email that looks like it’s from a friend, colleague, or the boss. Even seasoned veterans of the cybersecurity world have to honestly admit [here, this author raises his hand, coughing apologetically] that they too have clicked on a link or two before thinking.
In some ways, happy clicking is the new “failure to engage brain before opening mouth”, that all of us suffer from.
But instead of our mistakes causing a bit of embarrassment, human errors like downloading a file from a “trusted source”, or entering a password on a rogue website by accident can have disastrous consequences for the organisation. And hackers know these tactics work, which is why they use emails and messages in these phishing attacks.
It’s the real (and remote) world we’re in
A few years ago, every endpoint stayed safely inside the organisation’s network. It was relatively easy to protect each one, with anti-malware agents installed and updated by centralised push. However, with the massive popularity of remote working (both employees and employers appreciate the benefits) and the fact that everyone uses their own, private smart devices to access the internet as well as the company’s hardware, simple endpoint protection measures simply aren’t effective.
How do you protect your workers, therefore, if they’re able and willing to work anywhere by whatever means are at their disposal, at any time?
Facts, figures and statistics
More than 90 percent of IT administrators surveyed* have stated they’re concerned about infections starting via users’ endpoints. And nearly as many said the picture got complicated — and more worrying — when unauthorised individuals were able to access the work-EQUIPPED hardware, like a laptop or tablet.
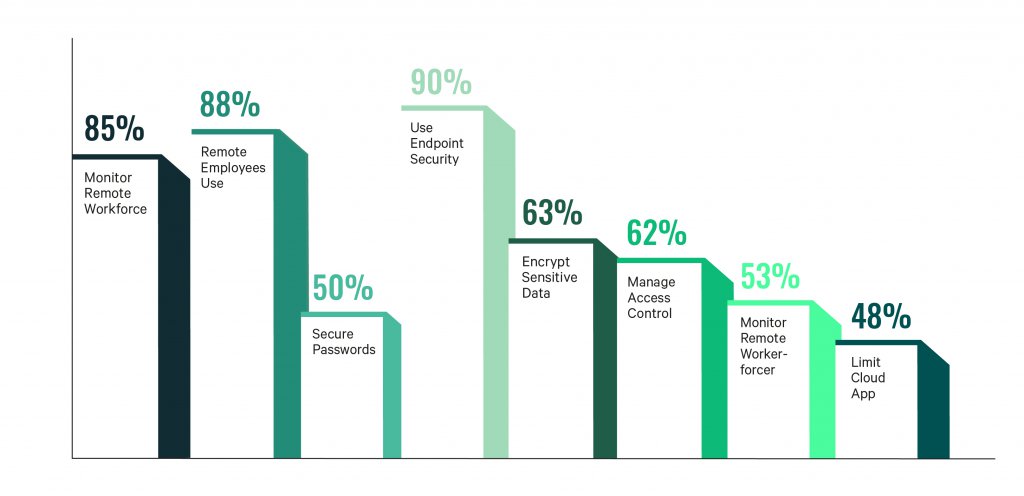
There is a good deal of confidence among IT admins, however, with 88 percent believing that employees working remotely used VPNs, and 85 percent also believing colleagues were trained to spot phishing and identity theft attempts.
However, a majority also stated that a remote worker had fallen victim to a successful cyberattack on their watch.
It would be easy to say that this a case of overconfidence on the part of IT professionals, but the truth is more mundane: even well-seasoned pros, who should know better, make mistakes and click a link or two before engaging brain, and so does every remote worker [author’s hand still raised, BTW].
*a survey of IT Administrators conducted by Site Research on behalf of WatchGuard.
What to do
There are three prerequisites every business, regardless of size, need to be doing continually to help mitigate against cyber risk in a working environment that involves remote working, mobile working and a BYOD-positive policy. The first two are the deployment of multifactor authentication for every business-related account. The second is the cybersecurity awareness training that’s given to staff.
If neither or one of these measures is in place already, then take immediate steps to address the situation. In fact, stop what you’re doing right now (reading this, for example), pick up the phone, and make a few calls to fix the situation.
But assuming your attention was drawn to this article because of the title and overall content, let’s concentrate on what you can do to protect every one of the workers in your organisation, from the highest CEO to the lowliest intern.
Protecting every endpoint in the organisation means deploying tools that accept — and that were built to expect — the fact that people make mistakes; that happy clicking incidents can and will take place.
What we at Tech Wire Asia recommend is software called DNSWatchGo from WatchGuard that runs on every endpoint that cross-checks every link followed, clicked or tapped by every worker against a by-the-second, up-to-date database of malware addresses.
That means any messaged request from the boss from which you download an attached document, or email from a colleague containing a PDF menu for the departmental Spring dinner is checked. And if the destination that the happy clicker asks for is a suspect site, the link (or “attached document”, or “menu”) is blocked.
But the user’s education isn’t ignored. If the link is known to be malicious, then they can be taken to a built-in game that helps press the message about phishing attempts home. That way, it’s two-fold protection, with each incident that’s avoided actively encouraging more responsible behaviour online.
Speaking of responsible behaviour, it’s worth noting too that the same mechanism can also be used to block inappropriate content or social media sites — or however the administrators set up policy. Company laptops are therefore protected, and there’s a potential “guide” to keep remote workers whose attention strays back onto a more productive path!
With a database of threats and potential trouble spots that’s kept up to date by the collective intelligence of WatchGuard and its users (every incident’s details help improve the knowledge base)— this is the best endpoint protection for remote workers we’ve seen for a long time.
Until the perfect human that doesn’t make mistakes comes along, keeping the user and the organisation safe needs a multi-pronged approach. Learn more from WatchGuard about what you can do between now and when evolution does its work.
READ MORE
- Ethical AI: The renewed importance of safeguarding data and customer privacy in Generative AI applications
- How Japan balances AI-driven opportunities with cybersecurity needs
- Deploying SASE: Benchmarking your approach
- Insurance everywhere all at once: the digital transformation of the APAC insurance industry
- Google parent Alphabet eyes HubSpot: A potential acquisition shaping the future of CRM
