
Addressing historical complacency in people-centric cybersecurity
As age-old as the existence of brands, businesses, and data is the array of threats that these entities face. The techniques and technicalities of such attacks are always evolving, but still primarily probe people’s vulnerabilities. Cybercriminals recognize that it is in the workforce that inconsistencies and poor security awareness can be exploited. Security and compliance tools – as well as robust staff training – are central to the management of the issue. While industries respond en masse (with Cybersecurity Ventures reporting that global spending on cybersecurity products and services is set to top $1tn by 2021), the majority of this spend is defending against the minority of attacks.
Until recently, the prevalent cybersecurity model has been to prevent or stymie attacks using an array of programs (you know the likes: firewalls, intrusion detection and prevention systems (IDS/IPS), network defenses, endpoint antivirus software). If something slips through these, organizations lock down the perimeter and deal with threats after the fact.
People over perimeters: a shift of focus in the Cloud era
The fact is the threat landscape is now markedly more people-centric. It requires a fresh mindset and a new strategy that focuses on protecting people rather than the things that plug in. A significant aspect of this is awareness and prevention. As Bruce Schneier – cryptographer, security and privacy specialist puts it – “only amateurs attack machines, professionals target people.”
More of what matters is moving to the cloud, meaning there’s less of a perimeter to defend. Attackers are even more in the ether – and thus more elusive – than they have been historically. In an increasingly partnered and outsourced world, work takes place on infrastructure that organizations don’t manage and channels they don’t own. The relative detachment of cloud-based operations renders workers more vulnerable to attackers who know the tech more intimately. Cloud infrastructure is highly secure, but the people who use it are vulnerable.
Here’s an alarming statistic for you: More than 99 percent of today’s cyberattacks are human-activated. No wonder the return of investment on infrastructural security is starting to wane. When attacks bypass a security system or a safeguard, humans are seemingly all too prone to opening a weaponized document, clicking an unsafe link, revealing credentials, or even carrying out the attacker’s commands directly (wiring/re-directing money or sending sensitive files). Spear phishing and phishing are not fun sports for the human victim.
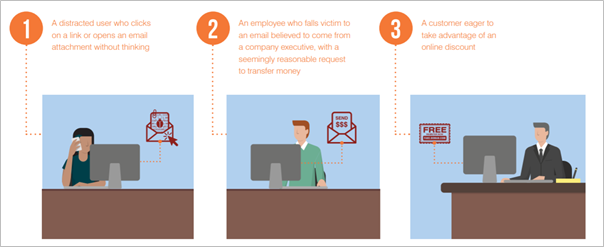
In the cloud era credential phishing can lead to the mistaken release of an organizational master key, email correspondence, sensitive data, private appointments, or critical corporate partnerships’ details. Credential phishing is one of the book’s old tricks, but it’s continually being revamped and made more believable.
Industries are aware of the changing landscape, and there are some standard solutions applied to the problem of people-centric cybersecurity. Be they ineffective or disruptive to employee productivity – or both – such solutions are not always adequate.
The existing state of play
- Placing restrictions on employees’ access to specific systems and sensitive data. Doing so – always on a role-based and carefully cultivated ‘need to know’ basis – can help ensure a breach is not possible.
- Rule-based technology. The continuation of vetting systems and malware blockers will stop some phishing emails landing in inboxes. That said, hackers are constantly finding little circumnavigations and manipulation tactics. Always responding by updating rules based on new threats takes time and lags behind the pace of threat evolution. Other blanket rules may prevent some breaches, but may also impede staff in carrying out their duties.
- Policies and algorithms that restrict certain human behaviors and offer training to raise awareness of the latest threats. Needless to say, perhaps, but not always a failsafe – human error can still occur if that particular employee forgets the section of the training, or (and this is more common) the stress of their workload lowers their inhibitions.
Going further: assessing digital behaviors
Now I’d envisage that you – sat there reading this, like me, sat here writing it – are thinking, nope, I am not prone to such foolery. We are diligent and wary and smart. But cybersecurity attacks have become as sophisticated as the technologies they seek to exploit, and it’s infrequent that attacks use the broad brushstroke of yesteryear. Each of us has distinct digital habits and weak spots, and targeters are perpetually equipping themselves to hit these.
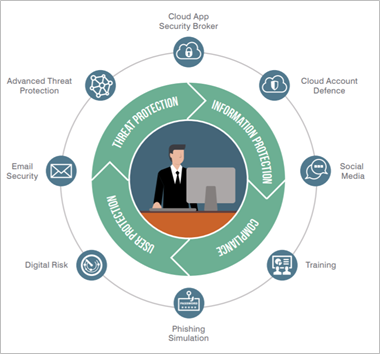
Regardless of our working environments, systems, or devices, each of us has unique professional contacts and privileged access to network data and business knowledge. Assessing digital behaviors and processes is key to understanding vulnerability, and even more so in the remote working world. Protecting all factors of user risk are central to equipping your business for the new age of cybersecurity concerns. Here are some pointers on where to start:
- Reducing users’ vulnerability: Training and awareness, but in a hands-on, almost visceral way, based on active, real-world (and even likely) attacks. This will make it easier for users to recall specifics should they come face-to-face with an issue in their daily operations. Such training is not a once a year kind of exercise; it’s a continuous process. That or the sophistication of threats will undoubtedly outpace your organization’s ability to negate them.
- Stopping the threats that target them: Putting the systems in place to prevent malware threats, non-malware threats, and web-based threats. Securing all three to an exemplary standard is extremely difficult, if not impossible, but there are nigh-on comprehensive security tools out there that can give you a solid shot.
- Applying adaptive controls to highly privileged or attacked users to better protect them: Fine-tuning access is the first step to managing privilege and is just as important as acknowledging if/when a privileged account has been compromised – some spear-phishing / phishing exercises will impersonate senior organizational staff – and recognizing a breach is a vital stimulus for communicating this breach before further person-centric incidents occur.
Addressing the vulnerabilities of home working
Sensitive business data and communications have been brought into homes, which are often less secure (technologically speaking) than a corporate office. This, combined with the heightened stress, anxieties, and distractions that have defined 2020, make us arguably more vulnerable than ever to phishing and social engineering schemes. Employees are in control of more business-critical data than before. There’s less proximal and infrastructural oversight. Some behavioral monitoring tools became virtually useless overnight, as employee behavior changed drastically, and model effectiveness was usurped.
The aforementioned stress – be it fear of getting sick, the potential impact on employment, or concern over financial stability – may also prompt workers/insiders to act maliciously themselves.
Thankfully, again, there is a range of existing and emerging solutions that can detect person-centric security incidents and swiftly block them, without disrupting workflows, nor necessitating reboots. As threats rise, rich threat intelligence levels increase with them, and timely insight is central to quantifying – and mitigating – individual risk.
Key players in people-centric cybersecurity:
PROOFPOINT
Proofpoint is a leading cybersecurity company that protects organizations’ most significant assets and biggest risks: their people. With an integrated suite of cloud-based solutions, Proofpoint helps companies around the world stop targeted threats, safeguard its data, and make its users more resilient against cyber-attacks. Its clients includes leading organizations of all sizes, including more than half the Fortune 1000, each of which is serviced by some of the most bespoke and scalable people-centric security solutions on the market. Proofpoint’s compliance solutions mitigate businesses’ most critical risks across email, the cloud, social media, and the web.
Worth attention is Proofpoint’s model for considering individual cyber risk: it calls it a VAP index, accounting for Vulnerability, Attacks, and Privilege. To assess ‘Vulnerability,’ you need to think about your users’ digital behavior — how they work and what they click. Some employees (more than some at the moment) may work remotely or access company email through their personal devices. They may use cloud-based file storage and install third-party add-ons to their cloud apps. Or they may be especially receptive to attackers’ email phishing tactics. For ‘Attacks,’ Proofpoint’s solutions consider (and cover) numerous threat types, the level of sophistication, the spread and focus of attacks, and the overall attack volume. ‘Privilege’ refers to the measurement of risk. Proofpoint acknowledges that attackers have a broad sweep of intentions, and anyone can be targeted. Usually, though, risk can be broken down on a role-by-role level by mapping the vulnerabilities, judging how a user’s position in your enterprise’s structure translates to their exposure.
There’s a much deeper look at the way this effective collection of strategies works in concord. Click here to read more on the pages of Tech Wire Asia.
BARRACUDA
As well as providing its customers with a range of backup services (bare metal and cloud-based) and email filtering technology, this cybersecurity provider also protects networks right from the point where the LAN meets the edge. The company’s Load Balancing ADC (Application Delivery Controller) can be hardware or software-based, or is available as a cloud service, and allows larger enterprises to use clusters of technology to scale in real-time according to loads placed on their systems – especially important when running web applications. The company’s modern web application firewall also serves to protect public-facing cloud-based apps from infiltration or attack. Barracuda’s solutions’ are such that, as situations change (for instance, at times of increased threat), additional layers of protection can be added seamlessly to all installations of the company’s solutions worldwide, with no installation of new hardware or application of security patches necessary by internal IT staff. All of Barracuda’s clients, however big or small, can benefit from real-time updates that have germinated, potentially, in a single attack on the other side of the globe.
PALO ALTO
Palo Alto’s next-generation firewalls come from the stance of letting the business’s needs dictate the security response, not security measures limiting the company. By identifying network traffic as belonging to a particular application, a classification map becomes apparent.
With this defining the ideal, security policies can then be intelligently deployed, allowing necessary traffic and preventing all else. From a single iOS user to globally virtualized networks, Palo Alto Networks’s extensive range of hardware enables protection of both physical and virtual machines. Suspicious activity can be sandboxed and payloads allowed to deploy safely, to learn their methods. This keeps potentially harmful traffic away from the organization’s network and creates an intelligent picture of acceptable or suspect activities.
The company also operates a broad network of its customers’ devices, so a malicious event taking place to one customer will, in time, inform the whole PAN customer base. Sharing of intelligence is, of course, something that has always underpinned the cybersecurity community. Still, by letting its entire customer base pool data, greater reliance is developed for all who deploy the company’s solutions.
F5 NETWORKS
Since their beginnings as load-balancing specialists (and the success of its BIG IP platform), F5 has been known for its provision of complete application development and deployment solutions. Its technology is ideally suited to hybrid deployments. By logically scaling up its capabilities to cover the entire IT stack by acquiring the company behind the open-source project NGINX, F5 now has access to the majority of the world’s web servers, which means it can protect, load-balance, and provide proxy services.
There are no specific platform limitations or stipulations anywhere in the entire application/service development and deployment environment. That means almost limitless interoperability and portability, irrespective of hardware or topology.
API Gateway, part of the NGINX Plus application delivery platform, and the API Management Console (a module of the NGINX Controller) can be deployed anywhere, from any public or private cloud environments to on-premises, to a private data center, or spread across hybrid and multi-cloud setups. Learn more about NGINX on the pages of Tech Wire Asia here.
*Some of the companies featured on this article are commercial partners of Tech Wire Asia
READ MORE
- Ethical AI: The renewed importance of safeguarding data and customer privacy in Generative AI applications
- How Japan balances AI-driven opportunities with cybersecurity needs
- Deploying SASE: Benchmarking your approach
- Insurance everywhere all at once: the digital transformation of the APAC insurance industry
- Google parent Alphabet eyes HubSpot: A potential acquisition shaping the future of CRM
