
IMG/Shutterstock
New Log4J vulnerability ‘most serious ever’, Chinese hackers already exploiting it
- Hundreds of millions of devices around the world are at risk of a newly revealed software vulnerability — the Log4j
- Attackers had over a week’s headstart on exploiting the software flaw before it was publicly disclosed, and the fallout could continue for days and weeks as organizations race to address the issue
- Tech giants like Amazon Web Services and IBM have addressed the bug so far
A critical new vulnerability called Log4j (or, Log4Shell) was disclosed last week — and at risk are hundreds of millions of devices around the world. The Log4j flaw was found to be on an open-source library used by millions of web servers. The bug leaves them all vulnerable to attack so organizations around the world are left scrambling to patch affected systems before hackers can exploit them.
The US Cybersecurity and Infrastructure Security Agency’s (CISA) director Jen Easterly told CNN that “the vulnerability is one of the most serious that I have seen in my entire career, if not the most serious.” CNN was briefed after the US officials held a call with industry executives, warning that hackers are actively exploiting the vulnerability.
According to researchers from Cisco and Cloudflare, hackers have been exploiting the bug since the beginning of the month. However, attacks ramped up dramatically following Apache’s disclosure last Thursday. Jen also emphasized that the security flaw poses a “severe risk” to the internet. “This vulnerability, which is being widely exploited by a growing set of threat actors, presents an urgent challenge to network defenders given its broad use,” she added.
What is Log4j and why is it so severe?
The news on the software flaw broke last week, with an initial alert by CERT New Zealand. Followed by the CISA and the UK’s National Cyber Security Center. For context, the vulnerability is in Java-based software known as “Log4j” and large organizations including some of the world’s biggest tech firms use it to log information in their applications.
In short, the flaw affects millions of pieces of software, running on a large number of machines that many systems interact with. So far, there have been various hacker orgs including Chinese state-backed groups, per the Financial Times, that have launched more than 1.2 million attacks on companies globally since last Friday. Quoting cybersecurity group Check Point, FT said the attacks relating to the vulnerability had accelerated since then and that at some points researchers were seeing more than 100 attacks a minute.
In fact, the Dutch National Cyber Security Center released a lengthy list of software that is affected by the vulnerability. A map showing where Log4j exploitation attempts have been made was released by international security company ESET. It indicates the highest volumes occurring in the US, UK, Turkey, Germany, and the Netherlands.
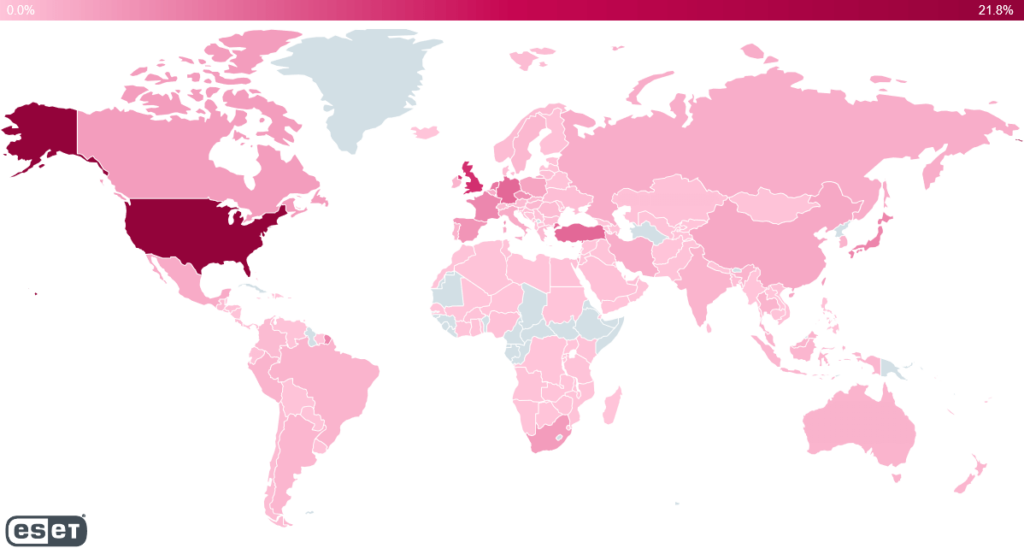
Log4j exploitation attempts. Source: ESET
Not too long after the flaw was detected, Apache gave the vulnerability a “critical” ranking and rushed to develop a solution. IT teams will have to update Log4j to version 2.15.0, which was released before the vulnerability was made public and it mostly fixes the issue. At the time of writing, tech giants like Amazon Web Services and IBM have addressed the bug in their products.
Even Microsoft, Cisco, and Google Cloud, have all found that at least some of their services were vulnerable and have been rushing to issue fixes and advise customers about how best to proceed. Unfortunately, a Wired article stated that the Log4Shell will continue to wreak havoc across the internet for years to come, as many organizations won’t even realize that they have systems at risk. In the meantime, attackers will continue to look for creative new ways to discover and continue exploiting as many vulnerable systems as possible.
READ MORE
- Ethical AI: The renewed importance of safeguarding data and customer privacy in Generative AI applications
- How Japan balances AI-driven opportunities with cybersecurity needs
- Deploying SASE: Benchmarking your approach
- Insurance everywhere all at once: the digital transformation of the APAC insurance industry
- Google parent Alphabet eyes HubSpot: A potential acquisition shaping the future of CRM


