
(Source – Shutterstock)
Could nation-state hackers be behind the largest data leak in China?
It’s been almost a week since reports of a large data leak in China made headlines around the world. While there has still yet to be any official word from the government or enforcement agencies addressing this particular incident, the rumor mill has been at play, with speculations continuing to raise concerns among many.
Reports by major publications around the world have confirmed that the data leak, which involves around 70% of China’s population is real. Some news agencies have even reached out to individuals whose particulars have been leaked online.
Bloomberg has also reported that China’s cabinet has stressed the need to bolster information security, following the data leak, but not directly addressing it. Quoting Xinhua News Agency, the report stated that a State Council meeting led by Premier Li Keqiang emphasized the need “to improve security management provisions, raise protection abilities, protect personal information, privacy and commercial confidentiality in accordance with the law.” The report didn’t directly reference the hack, and other state media agencies have so far been silent about the incident.
But there is one question that is also going through the minds of everyone, could China’s data leak have been carried out by state-sponsored hackers? Was it an act of espionage by another country? Or was it just simply caused by human error?
According to Candid Wuest, VP of Cyber Protection Research at Acronis, while it is not impossible, it is very unlikely that this data breach was the work of a nation-state attacker. Wuest explained that human error was more likely the reason behind it. This error was then discovered by a semi-automated scraping script of some cybercriminals.

Candid Wuest, VP of Cyber Protection Research at Acronis
At the same time, the monetization route chosen for the data leak is far more common with traditional cybercriminals instead of nation-state hackers. However, there is no denying that the data can now be purchased by almost anyone willing to pay for it, which is where the real concern is.
Echoing Wuest’s views is Stas Protassov, co-founder & Technology President of Acronis. Protassov pointed out that there was indeed a blog post by a developer on CSDN which contained access credentials – this might have been the entry point for the attacker.
“It’s not possible to confirm the attack vector without access to the organization’s logfiles, but it is a very likely scenario. Based on ID format, we can say with some confidence that it looks like ElasticSearch dump – again, it’s unclear whether it was due to the leaked credentials, or if it was badly configured, to begin with. Most commonly, this kind of leak happens when someone leaves an unauthenticated Elastic instance available from the Internet,” explained Protassov.
At the same time, Wuest highlighted that access to any valuable data should be guarded and protected with proper authentication. This includes strong credentials, proper rights management, as well as auditing and monitoring. It also means that old or exposed accounts and API keys need to be discarded as quickly as possible.
Additionally, solutions like Data Loss Prevention (DLP) and User Entity Behavior Analytics (UEBA) can be used to detect anomalies of data access patterns before the data is exfiltrated. Periodical user awareness training and revisiting

Stas Protassov, co-founder & Technology President of Acronis
For Protassov, news of such leaks is quite common, but this one is unique – because it’s big and because it proves that no one, not even IT administrators in China, is immune to making mistakes.
On whether the data leak could have a greater impact on China, Protassov said it is fairly unlikely that the data on its own is enough to take over the identification services, but it could lead to phone swapping or other identity fraud activity which could then lead to negative scoring in social media platforms.
“This information could be used to personalize future attacks, such as spear phishing, or to commit fraud in the name of the victims. Organizations and individuals should be vigilant of malicious emails or text messages in the near future and monitor for any fraud activity,” added Protassov.
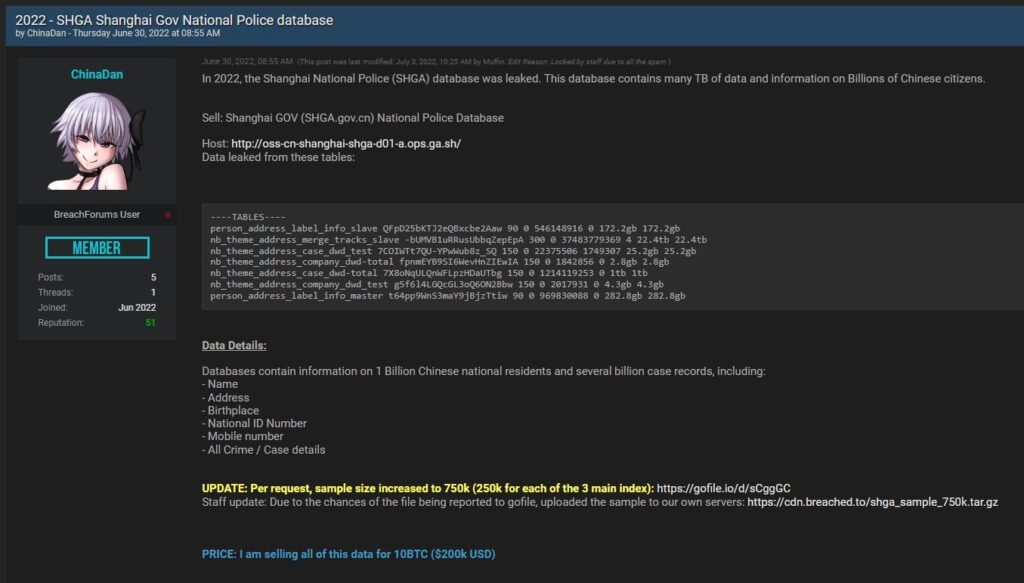
Screenshot of the data leak. (Source – Acronis)
China’s largest data leak saw cybercriminals offering a full dump of the database containing 24TB of personal information, with the asking price at 10 Bitcoins which currently is around US$200,000. Among the type of data leaked included personal info files, phone location data (or owner’s address) along with phone numbers, and what seems like a police incident or criminal case registry – with location and short incident description.
Protassov added that the majority of what is being told to be criminal case information are minor incidents bordering on public offense. This included phrases like, “Police were called to a scene of “There was a fight at the gate of the (redacted by Acronis) Zhujing Town, Jinshan District. Disputes to be mediated by the agency”, or “Water meter has been stolen. Police made a record”, or “The person who called the police was driving a car accidentally scratched the left side of the vehicle”. Protassov felt that as these records do refer to people involved, it could be damaging to some of those people.
“Unfortunately, with the growing complexity of IT infrastructure, we are seeing more and more of these large data breaches – cases where access control was not managed adequately, especially with large cloud databases and data buckets. This case will not remain the largest data leak in history for long,” he said.
READ MORE
- The criticality of endpoint management in cybersecurity and operations
- Ethical AI: The renewed importance of safeguarding data and customer privacy in Generative AI applications
- How Japan balances AI-driven opportunities with cybersecurity needs
- Deploying SASE: Benchmarking your approach
- Insurance everywhere all at once: the digital transformation of the APAC insurance industry


