
The aftermath of China’s largest data leak.Source – Shutterstock
Chinese state APT hacking group targets South China Sea energy industry as tensions rise
- Recent targeted phishing attacks that distribute the ScanBox reconnaissance framework using URLs imitating Australian media entities
- This campaign refers to threat behavior that used RTF template insertion and started in June 2021.
Most people imagine a cyber-attack as a one-time transfer when they think of them. A hacker gains access to a system, begins downloading crucial files and data, and then leaves. It’s not always so simple, though, when a hacking could have an impact on a country like China, to be ranked third in the world for being the victim of cyber-attacks.
Even when the first attempt at a cyberattack is unsuccessful, the threat does not always end there. It can require time and money to carry out a cyberattack against a well-organized system. Typically, APT groups—collectives of cybercriminals—are responsible for organizing them.
According to ComputerWeekly.com, advanced persistent threat (APT) groups targeted the Asia-Pacific (APAC) region as their main target between June 2019 and June 2020. A total of 34 campaigns were launched in the APAC region during the review period.
Malware and APT hackers are more common and advanced than ever. With that said, Proofpoint and PwC Threat Intelligence have jointly identified a cyber espionage campaign, active from April 2022 through June, delivering the ScanBox exploitation framework to targets who visit a malicious domain posing as an Australian news website.
The combined efforts of Proofpoint and PwC researchers offer a moderate confidence evaluation that recent campaigns aimed at the international manufacturing, energy, and federal government sectors may be an indication of TA423 / Red Ladon’s most recent activities.
TA423/Red Ladon is a China-based, espionage-motivated threat actor that has been active since 2013, targeting political events in the Asia-Pacific region, with an emphasis on the South China Sea.
The hacking on the Australian government and wind turbine fleets in the South China Sea
Based on the information provided by PwC Threat Intelligence regarding current ScanBox activity, Proofpoint discovered three waves of a phishing campaign that started on April 12 and continued through mid-June 2022. This information was offered by PwC Threat Intelligence. In the phishing campaign, malicious websites masquerading as Australian news outlets were linked to phishing emails that were sent to victims.
Selected targets received a JavaScript ScanBox malware payload from the website’s landing page. ScanBox has historically been distributed from websites that were the target of strategic web compromise (SWC) attacks, in which legitimate websites were compromised by the injection of malicious JavaScript code. Here, the threat actor is in charge of the malicious website and distributes malicious code to unwary users.
A ScanBox Primer: ScanBox is a JavaScript-based web reconnaissance and exploitation platform that allows threat actors to profile victims and deliver further malware to chosen targets of interest. It was first described in open source as early as 2014 by AlienVault. According to PwC Threat Intelligence, it is very possible that ScanBox is shared secretly by a number of threat actors based in China.
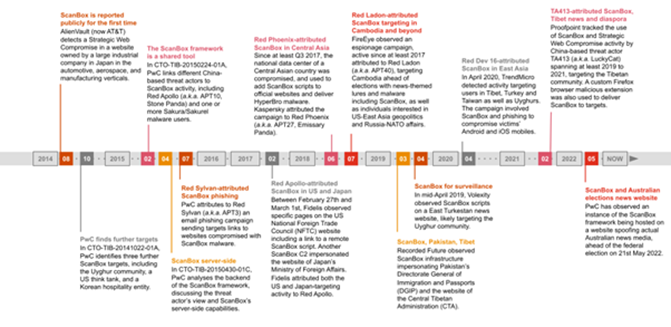
Source – Proofpoint (A timeline of activity involving ScanBox since 2014 to May 2022.)
The 2022 ScanBox campaign
The ScanBox campaign’s primary targets between April 2022 and June 2022 were:
- Australian local and federal government organizations;
- Australian news organizations; and
- International heavy industry manufacturers who maintain wind turbine fleets in the South China Sea.
This illustrated the blending of South China Sea offshore energy production ambitions with Australian government affairs. By injecting a downloader in DLL format using an RTF template, TA423/Red Ladon targeted users in a manner similar to what Proofpoint had previously seen in June 2021. The campaign, which lasted for thirteen months and integrated a variety of phishing tactics, techniques, and procedures, demonstrated the consistency of victimology (TTPs).
According to Sherrod DeGrippo, Vice President of Threat Research and Detection at Proofpoint, “TA423 is one of the most consistent APT actors in the threat landscape. They support the Chinese government in matters related to the South China Sea, including during the recent tensions in Taiwan. This group specifically wants to know who is active in the region and, while we can’t say for certain, their focus on naval issues is likely to remain a constant priority in places like Malaysia, Singapore, Taiwan, and Australia.”
READ MORE
- The criticality of endpoint management in cybersecurity and operations
- Ethical AI: The renewed importance of safeguarding data and customer privacy in Generative AI applications
- How Japan balances AI-driven opportunities with cybersecurity needs
- Deploying SASE: Benchmarking your approach
- Insurance everywhere all at once: the digital transformation of the APAC insurance industry


