
(Source – Shutterstock)
Stolen credentials causes Cisco breach
Data breaches are becoming increasingly common despite the increased adoption of cybersecurity solutions. For organizations, one of the biggest reasons for breaches is their employees themselves.
Stolen credentials continue to be the main cause of most data breaches around the world. Cybercriminals use these credential-based attacks to gain access and bypass organization security measures to steal critical data.
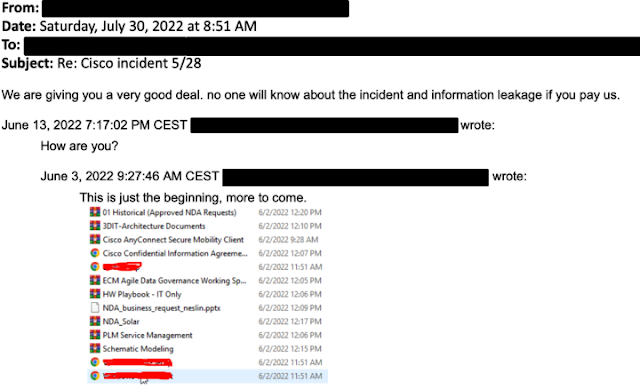
And this was exactly how cybercriminals were able to breach the corporate network of Cisco and stole up to 2.8GB of data in late May.
According to a report by Bleeping Computer, the breach at Cisco saw cybercriminals trying to extort the company under the threat of leaking the stolen files online. While Cisco did confirm a breach had occurred, they also revealed that the cybercriminals could only harvest and steal non-sensitive data from a Box folder.
The folder was linked to an employee whose credentials had been stolen and compromised. The threat actors were able to get access to the stolen credential after hijacking the employee’s personal Google account which contained credentials synced from their browser.
Cisco also stated that the attacker conducted a series of sophisticated voice phishing attacks under the guidance of various trusted organizations attempting to convince the victim to accept multi-factor authentication (MFA) push notifications initiated by the cyber attacker. The cyber attacker ultimately succeeded in achieving an MFA push acceptance, granting them access to VPN in the context of the targeted user.
(Source – Cisco)
Cisco added that the cyber attacker then escalated to administrative privileges. This allowed them to log in to multiple systems, which alerted the Cisco Security Incident Response Team. Despite this, the cyber attacker had dropped a variety of tools including remote access tools, and added their own backdoor accounts and persistence mechanisms.
Cisco also confirmed that the Yanluowang ransomware group was responsible for the breach on their corporate network.
“Based upon artifacts obtained, tactics, techniques, and procedures (TTPs) identified, the infrastructure used, and a thorough analysis of the backdoor utilized in this attack, we assess with moderate to high confidence that this attack was conducted by an adversary that has been previously identified as an initial access broker (IAB) with ties to both UNC2447 and Lapsus$.
IABs typically attempt to obtain privileged access to corporate network environments and then monetize that access by selling it to other threat actors who can then leverage it for a variety of purposes. We have also observed previous activity linking this threat actor to the Yanluowang ransomware gang, including the use of Yanlouwang data leak site for posting data stolen from compromised organizations,” stated Cisco.
While Cisco implemented a company-wide password reset immediately upon learning of the incident, the reality is that stolen credentials continue to be a method that cybercriminals are making the most of simply because employees are not careful enough on how and where they store and keep their passwords.
What happened at Cisco is just an example of how serious a cyberattack through social credentials can be. For companies that are not able to notice such changes in user patterns, the cyber attacker could use the stolen credential to get a lot more information and even cause a lot more damage to the organization.
As such, employees need to be vigilant while using their credentials and companies also need to have visibility on access to their data.
READ MORE
- Ethical AI: The renewed importance of safeguarding data and customer privacy in Generative AI applications
- How Japan balances AI-driven opportunities with cybersecurity needs
- Deploying SASE: Benchmarking your approach
- Insurance everywhere all at once: the digital transformation of the APAC insurance industry
- Google parent Alphabet eyes HubSpot: A potential acquisition shaping the future of CRM


