
Source – Shutterstock
Diamonds are forever: Iranian APT Agrius group deploys new wiper malware on girls’ best friend
- Agrius attacked the diamond industry’s supply chain by abusing Israeli software.
- Agrius is a more recent APT group with Iranian support that only engages in destructive activities.
Wiper malware is one of the nastiest cyber threats in the world of cybersecurity. Once wiper malware enters a company’s environment, it quickly spreads, deletes everything in its path, and destroys any data it touches.
In contrast to its “friend,” ransomware only encrypts its victim’s files, temporarily blocking access until the ransom is paid. The simplest method to remove data from a system is overwriting the data at a particular physical area with different data. While this approach requires cybercriminals to write several gigabytes or terabytes of data, it is incredibly effective.
NotPetya is an example of the destructive potential of self-replicating wiper malware. Researchers first became aware of this self-replicating wiper malware entering Ukrainian organizations’ networks in 2017. NotPetya pretended to be ransomware while it lacked a ransom recovery mechanism by seeking “ransom” fees from users.
NotPetya soon extended beyond its initial targets thanks to its ability to worm across several systems via a vulnerability in the Windows operating system, crippling some of the biggest companies in the world, including international shipping companies Maersk and FedEx. SingCERT reported that NotPetya caused US$ 10 billion in cumulative damages in 2017, making it the most financially devastating cyberattack in history.
ESET researchers recently found a new wiper and the tool used to execute it, both ascribed to the Agrius APT group, which has ties to Iran. The malware operators used a supply-chain attack against an Israeli software developer to spread their new wiper, Fantasy, and new lateral movement and Fantasy execution tool, Sandals. In February 2022, Agrius started targeting an Israeli HR company, a diamond distributor, and an IT consulting firm since these organizations use the same Israeli software suite used in the diamond sector.
Who is the Agrius APT group?
Agrius is an organization with ties to Iran that has been targeting Israel and the United Arab Emirates victims since 2020. The group initially used Apostle, a wiper disguised as ransomware, but eventually modified it to become a full-fledged ransomware. Agrius installs webshells using known vulnerabilities in internet-facing programs, then performs internal research before moving laterally and releasing its malicious payloads.
How the wiper malware is being executed
Adam Burgher, Senior Threat Intelligence Analyst at ESET, said the campaign lasted less than three hours. By the end of that time, ESET customers were already protected by detections that identified Fantasy as a wiper and prevented its execution.
“We observed the software developer pushing out clean updates within a matter of hours of the attack,” says Burgher. “ESET contacted the software developer to notify them about a potential compromise, but the inquiries went unanswered.”
Burgher explained that on February 20, 2022, Agrius implemented credential harvesting tools at a company in the diamond sector in South Africa, perhaps in preparation for this campaign. The wiping attack was then carried out by Agrius on March 12, 2022, by sending Fantasy and Sandals to three different victims: one in South Africa, one in Israel, and one in Hong Kong.
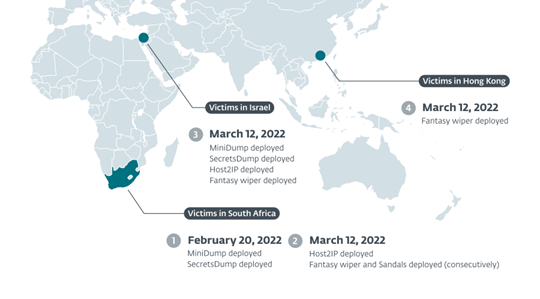
Victim timeline and locations. (Source – ESET)
The fantasy wiper either deletes all files on the hard drive or deletes all files with one of 682 different extensions, including filename extensions for Microsoft 365 applications like Word, PowerPoint, and Excel, as well as for popular video, audio, and image file formats. The Windows operating system disc may be recoverable even though the malware takes measures to make a recovery and forensic analysis more challenging. Victims were seen to be operating normally again in a matter of hours.
Since its discovery in 2021, Agrius has only engaged in harmful operations. In many ways, Fantasy resembles Apostle, the earlier Agrius wiper. Fantasy, however, does not attempt to disguise itself as ransomware. Many of the Apostle’s original functions have been implemented in Fantasy with only a few minor changes.
READ MORE
- The criticality of endpoint management in cybersecurity and operations
- Ethical AI: The renewed importance of safeguarding data and customer privacy in Generative AI applications
- How Japan balances AI-driven opportunities with cybersecurity needs
- Deploying SASE: Benchmarking your approach
- Insurance everywhere all at once: the digital transformation of the APAC insurance industry


