
(Source – Sophos)
Criminal marketplaces designed to scam scammers unraveled
Scammers continue to make a fortune from their activities despite the numerous security, protection, and awareness campaigns about them. Almost every day, local media reports highlight a case of someone, or an organization being scammed. In many cases, the amount of money scammed by a company or individual can be high, making many wonder how can anyone fall so easily for scammers.
The essence of a scam is simple. Scammers pretend to be someone they are not selling a story that is often too good to be true. Yet, victims still fall for it. In fact, scammers have become so sophisticated in their approach that they are now even scamming other scammers.
According to a report by Sophos, it was able to track down a culprit behind more than 20 fake criminal marketplaces designed to con cyber scammers. In “The Scammers Who Scam Scammers on Cybercrime Forums report, after stumbling upon a surface website mimicking the real criminal underground site Genesis, Sophos researchers further uncovered the 20 fake marketplaces dating back to August 2021. All of the fake sites appeared to be run by a scammer who uses the handle “waltcranston,” likely a riff on the television show “Breaking Bad.”
“While investigating this huge sub-economy of scammers scamming other scammers, we examined about 600 scams of varying types. Out of all the scams investigated, this operation stood out for its sheer scope and intricacy. The scammer advertises the fake marketplaces on Reddit and replicates not just Genesis, which was the first scam site we ran across, but numerous other prominent or defunct marketplaces, such as Benumb, UniCC, and PoisOn. While at a technical level, these scam sites are not sophisticated, the scam operation has been highly successful. In fact, seven of these fake sites are still active, and, to date, the cryptocurrency wallets associated with the scams have received at least US$132,000,” said Matt Wixey, senior threat researcher at Sophos.
The 20 fake sites followed a similar scheme. Criminals were offered a chance to activate an account on the fraudulent version of a dark web marketplace with US$100. The criminals expected their US$100 would be deposited in either Bitcoin or Monero, and they would receive activation credentials. However, as part of the scam, once the criminals paid, their accounts would never activate.
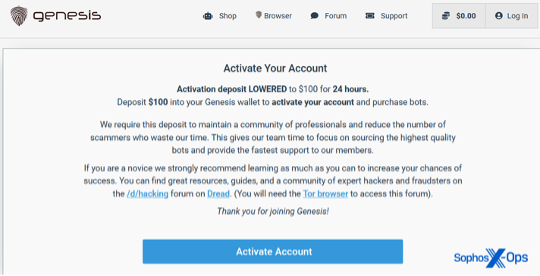
The deposit demand on the fake Genesis site. (Source – Sophos)
One common denominator among the 20 fake sites was a link to a website called darknet[.]markets—a site that lists dark web criminal marketplaces for visitors interested in drug sales, carding, and cryptocurrency exchanges. This site ultimately led Sophos to a criminal forum called Café Dread—and a user going by the name of waltcranston.
“We started searching Dread for any mentions of the marketplaces mentioned on the darknet[.]markets, and we found multiple posts by the handle waltcranston talking about dark web marketplaces, as well as discussing how to scam people and recommending other users set up phishing sites. His own website, which sells meth, also shared some similarities with the fake marketplaces. We even found posts by Dread users who fell for the scam websites and accusations by a Dread user that waltcranston was the culprit behind the scheme. While we can’t be 100% certain that those behind the handle waltcranston is indeed the culprit, there is strong circumstantial evidence. The entire operation and our investigation is an example of how much rich intelligence there is about cybercriminals hidden in these scams against other scammers, which the security community can leverage to help develop stronger defenses,” added Wixey.
Wixey also highlighted that scam reports like the one by Sophos are a rich yet often underexplored source of intelligence. Threat actors are aware that their criminal forums are monitored and often employ good operational security. However, Wixey said when they’re victims of crime themselves, there isn’t much as forum rules demand proof to support scam allegations. As such, wronged threat actors will often post screenshots of private conversations and source code, identifiers, transactions, chat logs, and blow-by-blow accounts of negotiations, sales, and troubleshooting.
READ MORE
- Ethical AI: The renewed importance of safeguarding data and customer privacy in Generative AI applications
- How Japan balances AI-driven opportunities with cybersecurity needs
- Deploying SASE: Benchmarking your approach
- Insurance everywhere all at once: the digital transformation of the APAC insurance industry
- Google parent Alphabet eyes HubSpot: A potential acquisition shaping the future of CRM


