
Ransomware dominated 2022, showing cybercrime is thriving
- The United States, at 29%, tops the list of the five countries most affected by ransomware groups in the final quarter of 2022.
- Cuba ranked first among the most prevalent ransomware families in Q4 2022 – compromising over 100 entities worldwide and demanding over US$145 million.
The ongoing conflict in Ukraine has witnessed the emergence of new forms of cyberattacks, while hacktivists have become savvier and more emboldened to deface sites, leak information, and execute DDoS attacks. Despite the rise of new types of cyberthreats, traditional attacks that involve deceiving and manipulating individuals to disclose personal or confidential data are still a widespread problem.
Trellix, a cybersecurity company, has recently published The Threat Report: February 2023, which examines the cybersecurity trends of the fourth quarter of 2022 (Q4 2022). According to the report, ransomware attacks continued and impacted numerous organizations globally as cybercriminals exploited the pandemic-induced shift to remote work or greater dependence on digital services. Trellix gathers telemetry data from its broad network of endpoint protection installations and XDR product line, and open and closed source intelligence reports to provide its report insights.
Ransomware takes center stage in Q4 2022 cybercrime landscape
According to the report, the United States (US) tops the list of the five countries most affected by ransomware groups in Q4 2022 with 29%. China placed second with 12%, followed by Qatar with 10%, Japan with 9%, and Indonesia with 8%.
The report provides evidence of malicious activities associated with ransomware and advanced persistent threat (APT) actors supported by nation-states. It examines several threats, such as the use of legitimate security tools and email. The following are the key findings of the report:
- Chinese nation-state activity: according to the report, 71% of detected nation-state backed activity in Q4 2022 was attributed to advanced persistent threat actors linked to China, such as Mustang Panda and UNC4191. North Korea, Russia, and Iran followed. The four countries were also identified as the most active APT actors in public reports.
- Critical infrastructure sectors most impacted: the report notes that 69% of detected malicious activity linked to nation-state backed APT actors was aimed at transportation and shipping, followed by energy, oil, and gas. Finance and healthcare were among the top sectors targeted by ransomware actors, while malicious emails were most frequently directed at telecom, government, and finance.
- Fake CEO emails resulted in business email compromise: in Q4 2022, 78% of business email compromise (BEC) involved fake CEO emails using common CEO phrases, resulting in a 64% increase from Q3. Threat actors used tactics such as voice-phishing and 82% of these emails were sent using free email services, making it easy for threat actors to execute their campaigns.
“Q4 saw malicious actors push the limits of attack vectors,” said John Fokker, Head of Threat Intelligence, Trellix Advanced Research Center. “Grey zone conflict and hacktivism have both led to an increase in cyber as statecraft as well as a rise in activity on threat actor leak sites. As the economic climate changes, organizations need to make the most effective security out of scarce resources.”
Who are the most prevalent ransomware families?
Based on Trellix’s global telemetry, their report identified several campaigns from various ransomware groups impacting different countries and sectors. The report analyzes the characteristics of these campaigns rather than the detections themselves. The most prevalent ransomware families, along with their tooling and techniques, were identified from the campaigns.
Cuba ranked first among the most prevalent ransomware families in Q4 2022, with 22%, according to Trellix. What makes them so dangerous?
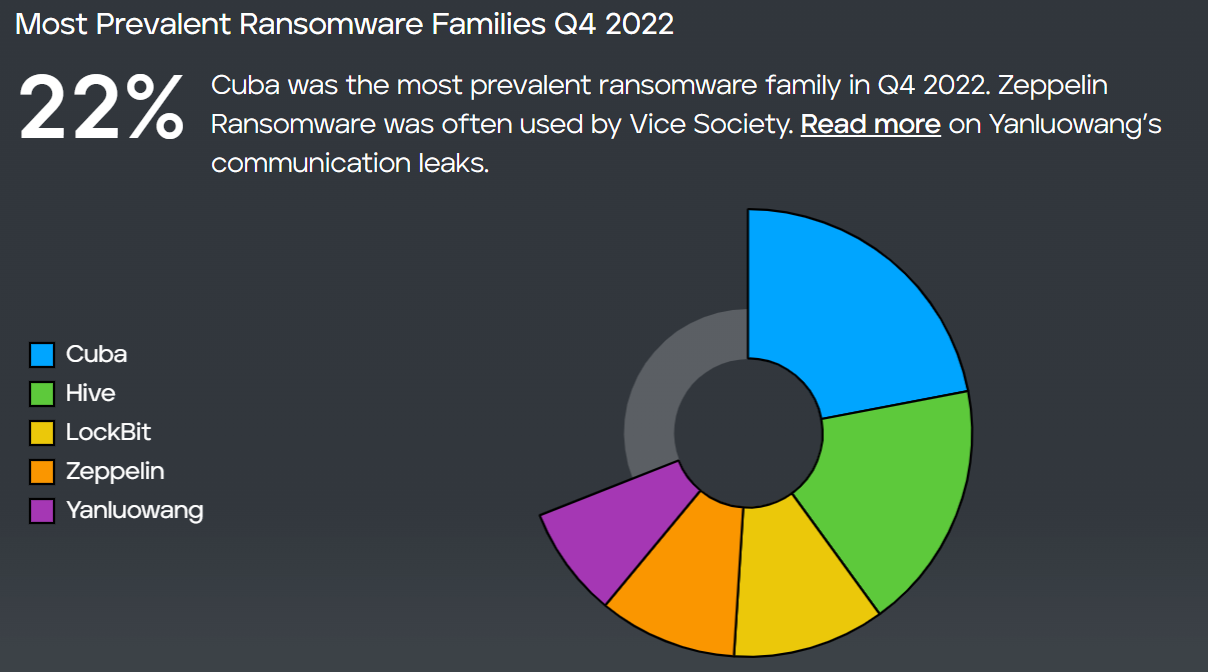
Most Prevalent Ransomware Families Q4 2022 (Source – Trellix)
The ransomware family gained notoriety in November 2021 after the FBI posted an official notice detailing its activities. Since then, Cuba ransomware actors have compromised over 100 entities worldwide and demanded over US$145 million. They have also received over US$60 million in ransom payments. Cuba ransomware uses the double extortion technique, which forces victims to pay the ransom demand. This ransomware family is considered a significant player in the threat landscape and is expected to remain due to its continued evolution.
In addition to Cuba, several other prevalent ransomware families existed in Q4 2022. Hive ranked second with 18%, followed by LockBit at 11%, Zeppelin at 10%, and Yanluowang at 8%.
The sectors most affected by the most prevalent ransomware families in Q4 2022 were not surprising, as indicated by Trellix telemetry. The outsourcing & hosting sector was the most affected by ransomware groups, with 29%. This finding was consistent with the average size of the victims listed on ransomware leak sites, as many organizations do not have their own IP block and rely on third-party hosting providers.
The banking/financial industry was the second most impacted, accounting for 17% of victims, followed by wealth management with 16%. Government ranked fourth with 12% of victims, while wholesale was the least impacted, accounting for only 9%.
The report identifies the top countries affected by ransomware and advanced persistent threat (APT) actors and the most prevalent ransomware families and their impact on different sectors. As organizations face malicious cyber activities, they must allocate their resources effectively to ensure their security.
READ MORE
- Ethical AI: The renewed importance of safeguarding data and customer privacy in Generative AI applications
- How Japan balances AI-driven opportunities with cybersecurity needs
- Deploying SASE: Benchmarking your approach
- Insurance everywhere all at once: the digital transformation of the APAC insurance industry
- Google parent Alphabet eyes HubSpot: A potential acquisition shaping the future of CRM


