A ‘bored’ hacker breached Swiss cybersecurity firm Acronis. Here’s what we know so far.Source: Shutterstock
Acronis customer compromised by ‘bored’ hacker. Here’s what we know
- According to a dark-web claim shared on social media by a threat watcher, hackers breached Acronis and leaked stolen data on a dark-web forum.
- The data includes certificate files, command logs, system configurations, and file system archives.
- Acronis’ CISO denies the company data was breached but says it only involved a customer whose “password was stolen.”
Acronis, a global leader in cyber protection, as it claims on its website, has fallen victim to a password compromise. The Swiss firm, founded in Singapore, with over 2,000 employees in 45 locations, has been compromised by an unspecified hacker who leaked the stolen data on a dark-web forum.
A threat watcher by the name FalconFeedsio first unveiled the incident on Twitter. A Thursday post [PDF] to the notorious Breached Forums leak-mart brought Falcon to the news of the breach. In that post, an attacker named Kernelware – who also cracked Acer – claimed they leaked certificate files, command logs, system configurations, and file system archives.
A user in the hacker's forum claims to have leaked data from a #Switzerland cybersecurity company. The leaked data includes various certificate files, command logs, system configurations, system information logs, archives of their filesystem, python scripts for their maria.db… https://t.co/GoDdozmtx5 pic.twitter.com/DMf5tr1BJB
— FalconFeedsio (@FalconFeedsio) March 9, 2023
Kernelware also stated that although the US$120 million company is in the data protection and infosec business, it had “dogshit security,” and the reason for the breach was that the hacker was bored, so they decided to “humiliate” them. Kernelware, in fact, posted an archive that held 12.2 GB of files.
For context, according to the company’s website, its cyber protection solutions are “trusted by over 20,000 service providers, 750,000 businesses, and services organizations in more than 150 countries”. In September 2022, the Swiss company claimed that Acronis Cyber Protect had prevented over one million attacks and protected over 2.66 million workloads.
“Today, I’m leaking details of a cybersecurity company called Acronis,” the hacker said. Reacting to that, Falcon tweeted, “The leaked data includes various certificate files, command logs, system configurations, system information logs, archives of their file system, Python scripts for their maria.db database, backup configuration stuff, and many screenshots of their backup operations.”
Not a data breach, Acronis reckons
In an e-mail to Tech Wire Asia, Acronis’ spokesperson said the cybersecurity firm only acknowledged the compromise of a single customer password. “The incident only impacted a single customer, and all other data remains safe,” the e-mail reads. The spokesperson also shared that Acronis is still investigating the situation. “However, we don’t see any evidence of Acronis systems compromise, and the incident affected only a single customer, so we at this moment don’t believe the password was stolen from our systems,” the person added.
Acronis also shared an official statement: “On March 9, a post on BreachedForums mentioned Acronis. We immediately started the investigation. The investigation confirmed that no Acronis products were affected. However, based on our information, the credentials used by a specific customer to upload diagnostic data to Acronis Support have been compromised.”
When the news on the compromise started to make rounds, Acronis’ Chief Information Security Officer (CISO), Kevin Reed, took to his LinkedIn to share what the company knew about the situation. Reed clarified the incident only impacted a single customer and that all other data remains safe.
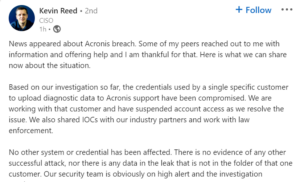
Acronis CISO Kevin Reed’s dispute on details of the hack. Source: LinkedIn
“Based on our investigation so far, the credentials used by a single specific customer to upload diagnostic data to Acronis support have been compromised. We are working with that customer and have suspended account access as we resolve the issue. We also shared IOCs with our industry partners and worked with law enforcement,” he said. Adding to his statement, the company’s spokesperson told Tech Wire Asia that they do not acknowledge claims that the attack was on the system. “The system remains stable and secure.”
Reed summed up the incident by concluding that no data leak or any other system or credential was affected. “There is no evidence of any other successful attack, nor is there any data in the leak that is not in the folder of that one customer. Our security team is obviously on high alert, and the investigation continues,” he added. Acronis appears quite sure the compromise is not from their end.
**The article has been updated with official clarification and a statement from Acronis.
READ MORE
- Ethical AI: The renewed importance of safeguarding data and customer privacy in Generative AI applications
- How Japan balances AI-driven opportunities with cybersecurity needs
- Deploying SASE: Benchmarking your approach
- Insurance everywhere all at once: the digital transformation of the APAC insurance industry
- Google parent Alphabet eyes HubSpot: A potential acquisition shaping the future of CRM