
(Source – Shutterstock)
Chinese cyber espionage group SharpPanda targeting SEA governments
When it comes to cyber espionage, the world continues to experience an increasing number of events. From governments targeting each other and launching cyberattacks to businesses spying on rivals, espionage remains a threat in cybersecurity that can’t be solved easily.
Countries normally associated with cyber espionage include China, Iran, North Korea and Russia. These four countries have also accused the US and several other western countries of spying on them.
According to a report published by the Office of the Director of National Intelligence in the US, China represents the broadest, most active and most persistent cyber espionage threat to U.S. government and private-sector networks. The Pentagon continues to monitor activities by Chinese brands in the US, including social media apps like TikTok which could be banned in the country due to security reasons.
But aside from the US having espionage concerns, Check Point Research (CPR) reports that espionage campaigns are also expanding to the ASEAN region. Specifically, CPR sees the expansion of an ongoing cyber espionage campaign to target Southeast Asian governments, including Vietnam, Thailand, and Indonesia.
In fact, CPR identified a Chinese APT group named SharpPanda in June 2021. SharpPanda uses spear-phishing and Microsoft vulnerabilities to gain access to target networks. CPR continued to track SharpPanda’s activity since then, learning of a cyber attack on a high-profile government entity in late 2022.
The payload in this specific attack leverages what’s known as the Soul modular framework, a previously unattributed modular malware framework. While the Soul framework has been in use since at least 2017, the threat actors behind it have been constantly updating and refining its architecture and capabilities.
CPR explained that the attack begins as a phishing attack with a malicious document containing a remote template with an exploit. The exploit runs a built-in downloader, which helps run the Soul backdoor. Although the Soul malware framework was previously seen by Semantic in an espionage campaign targeting the defense, healthcare, and ICT sectors in South East Asia, it was never previously attributed or connected to any known cluster of malicious activity. Currently, it is uncertain whether the Soul framework is solely utilized by a single threat actor.
And this is where there’s a connection between the tools of Sharp Panda and the previously mentioned attacks in the region. This serves as yet another example of key characteristics inherent to China-based APT operations, such as sharing of custom tooling between the groups or task specialization of threat actors, where one entity is responsible for the initial infection and another one is for actual intelligence gathering.
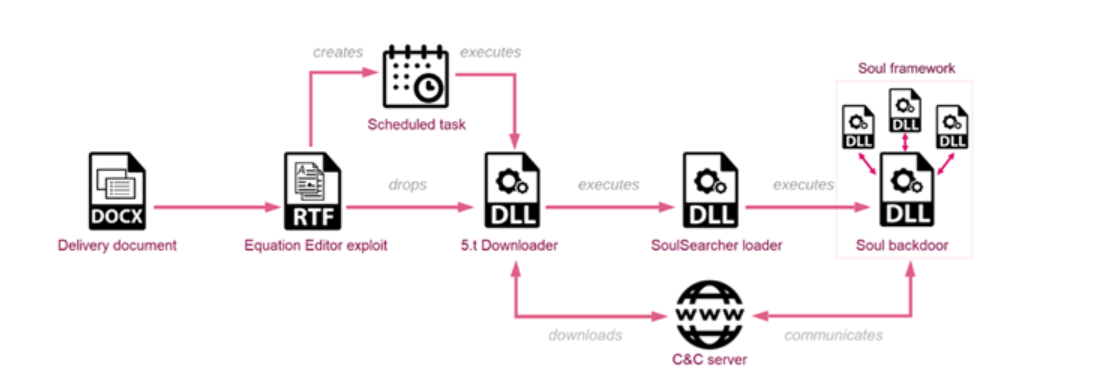
Infection chain. (Source – Check Point Research)
Looking at who is responsible, CPR attributed the cyber espionage campaign to an APT group with Chinese origins, whose motive is to steal data and spy on government entities. Last year, another cybersecurity vendor also identified a Chinese-based cyber espionage campaign that posed as an Australian news website targeted Southeast Asia. Another cybersecurity vendor has also published findings on Dark Pink, an ongoing APT campaign launched against high-profile targets in Cambodia, Indonesia, Malaysia, Philippines, Vietnam, and Bosnia and Herzegovina.
For Eli Smadja, Research Group Manager at Check Point Software, these are long-running Chinese cyber-espionage operations targeting South East Asian government entities, including Vietnam, Thailand and Indonesia. He believes there’s an interesting connection between two attack tools set for the first time.
“Based on the technical findings presented in this research, we believe this campaign is staged by advanced Chinese-backed threat actors, whose other tools, capabilities and position within the broader network of espionage activities are yet to be explored,” commented Smadia.
Smadia also pointed out that while Sharp Panda’s previous campaigns delivered a custom and unique backdoor called VictoryDll, the payload in this specific attack is a new version of SoulSearcher loader, which eventually loads the Soul modular framework.
“Usually, the attack starts as a phishing attack with a malicious document containing a remote template with a Royalroad exploit. The exploit runs a built-in downloader and then downloads the second stage of the Soul framework, which runs the Soul backdoor. Although the samples of this framework from 2017-2021 were analyzed before, this is the most extensive infection chain of the Soul malware family to be documented, including the full technical analysis of the latest version, compiled in late 2022,” added Smadia.
READ MORE
- Ethical AI: The renewed importance of safeguarding data and customer privacy in Generative AI applications
- How Japan balances AI-driven opportunities with cybersecurity needs
- Deploying SASE: Benchmarking your approach
- Insurance everywhere all at once: the digital transformation of the APAC insurance industry
- Google parent Alphabet eyes HubSpot: A potential acquisition shaping the future of CRM


