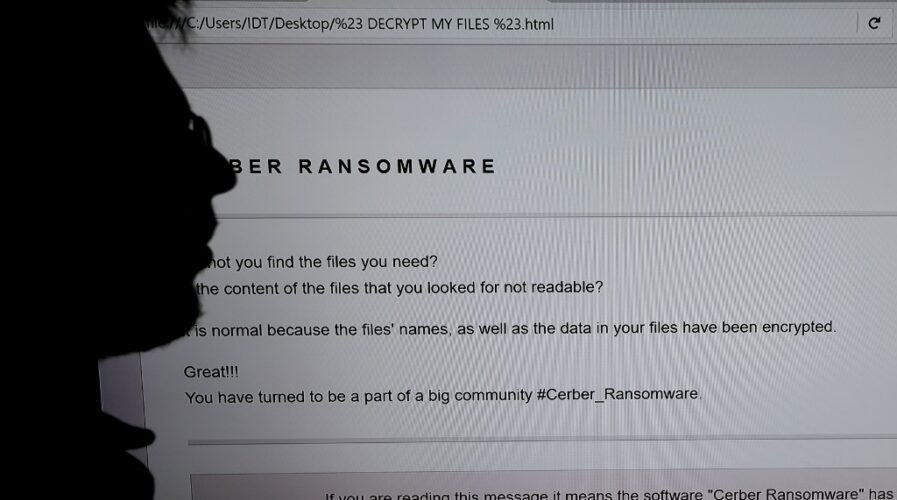
Ransomware attack on Scottish environmental agency shows no organization is too large or too small for cybercriminals. Source: AFP
Ransomware attacks increasingly exposing gaps in large firms
Since 2020, the threat of cyberattacks have risen exponentially all across the globe, and one of the most common archetypes is, unfortunately, turning out to be ransomware. Online criminals are increasingly targeting large entities for ransomware attempts including governmental systems, with the most recent being the Scottish Environment Protection Agency (SEPA) which was attacked last month – and the effects of the breach are still being felt across the organization.
Cyber bad actors have been profiteering off the illicit gains from ransomware attacks for many a year by this point, and the SEPA breach is the latest bold example of a national network being compromised. SEPA is Scotland’s governmental regulator for safeguarding the environment, and the agency says the attack which hit on Christmas Eve has affected its contact center operations, internal systems, processes, and internal communication.
The organization has also confirmed that 1.2GB of data has been stolen as part of the attack, including personal information relating to SEPA staff. Some of SEPA’s critical services are still operational, like its ability to provide flood forecasting and warning system, along with regulation and monitoring services, but SEPA’s latest update says that recovery from the ransomware attack will take a “significant period” and that a number of systems will “remain badly affected for some time” with entirely new systems required.
SEPA has blamed the ransomware attack on “serious and organized” cybercriminals. “Whilst having moved quickly to isolate our systems, cybersecurity specialists – working with SEPA, Scottish Government, Police Scotland and the National Cyber Security Centre – have now confirmed the significance of the ongoing incident,” said SEPA chief executive Terry A’Hearn.
The agency hasn’t yet detailed how cybercriminals were able to break into the network to deploy ransomware and the investigation into the incident is still ongoing.
How ransomware is affecting businesses
Stealing data has become an increasingly common tactic for ransomware gangs that target large organizations. Malicious actors now use the stolen data to double-down on attempts to extort funds from the company, by threatening to leak the information if the victim doesn’t give in to the ransom demand of hundreds of thousands, or even millions, of dollars.
Firms would have to pay these ransoms in virtually untraceable cryptocurrency transactions like bitcoin, in exchange for a decryption key to unlock their own stolen data. Ransomware can affect any organization, large or small, including businesses, schools and educational facilities, hospitals and healthcare providers, government agencies, and non-profit entities.
Cybercriminals who deploy a successful ransomware attack do so in phases, many of which require planning, stealth, and cunning. Targeting a large organization that has a lot to lose if its data is exposed, often works in the hackers’ favor as many victimized organizations don’t report a ransomware attack for fear of losing money, business, or private data. Victims often just quietly pay off their attackers without notifying anyone.
Due to this reason as well, it is difficult to quantify just how widespread a threat ransomware is, but of the 187.9 million ransomware attacks reported by Statista in 2019, 67% were initiated by spam and phishing emails, 36% occurred due to poor cybersecurity training, 30% because of weak passwords and ineffective asset management, 25% due to poor user practices, 16% originated from malicious websites, and 16% due to clickbait.
Based on this, it is vital that bigger corporations prioritize user training on common cybersecurity threats for staff, including security awareness and education about the threat of ransomware and the ways it can be delivered. Also, all connected company systems should be patched and updated to the latest versions, and this includes robust antivirus and anti-spam solutions to regularly scan devices for malware, which can be useful in preventing a ransomware attack.
Finally, an organization with the adequate IT infrastructure should also have an incident response or crisis management plan for dealing with ransomware events, that describes which employees to contact and what to do. To ensure a practical implementation, the plan should be rehearsed regularly so the right people know how to respond in a moment of crisis.
READ MORE
- Ethical AI: The renewed importance of safeguarding data and customer privacy in Generative AI applications
- How Japan balances AI-driven opportunities with cybersecurity needs
- Deploying SASE: Benchmarking your approach
- Insurance everywhere all at once: the digital transformation of the APAC insurance industry
- Google parent Alphabet eyes HubSpot: A potential acquisition shaping the future of CRM
