Malware exploits Microsoft’s e-Signature verification
Malware campaigns continue to be a big problem for businesses around the world. Despite some malware issues being solved, they tend to make a comeback after some time as well. In Southeast Asia, cybercriminals have been using malware campaigns to exploit organizations through various methods.
According to Check Point Research, the Zloader malware has now made a comeback. First spotted in 2015, the malware campaign is now reported to be exploiting Microsoft’s digital signature verification to steal sensitive information from victims. The ZLoader malware is a banking trojan that uses web injection to steal cookies, passwords, and any sensitive information.
In September 2021, ZLoader fell under the radar of the Cybersecurity and Infrastructure Security Agency (CISA) as a threat in the distribution of Conti ransomware. Most Conti ransomware is laid directly by a hacker that has accessed an unprotected RDP port, utilized email phishing to remote into a network via an employee’s computer, or utilized malicious attachments, downloads, application patch exploits, or vulnerabilities to gain access to a network.
During the same month, Microsoft said ZLoader operators were buying Google keyword ads to distribute various malware strains, including Ryuk ransomware.
While analyzing ZLoader campaigns in early September, we observed a notable shift in delivery method: from the traditional email campaigns to the abuse of online ad platforms. Attackers purchased ads pointing to websites that host malware posing as legitimate installers. pic.twitter.com/8HkR4kmyO6
— Microsoft Security Intelligence (@MsftSecIntel) September 23, 2021
Check Point Research published a report that details the resurgence of ZLoader in a campaign that has taken over 2,000 victims in 111 countries. Check Point Research attributes the campaign to the cybercriminal group MalSmoke.
Check Point Research shared the infection chain of Zloader. First, the attack begins with the installation of a legitimate remote management program pretending to be a Java installation. After this installation, the attacker has full access to the system and is able to upload and download files and also run scripts. The attacker uploads and runs a few scripts that download more scripts that run mshta.exe with file appContast.dll as the parameter.
Not sensing any anomaly, the file appContast.dll is signed by Microsoft, even though more information has been added to the end of the file. From there, the added information downloads and runs the final Zloader payload, stealing user credentials and private information from victims.
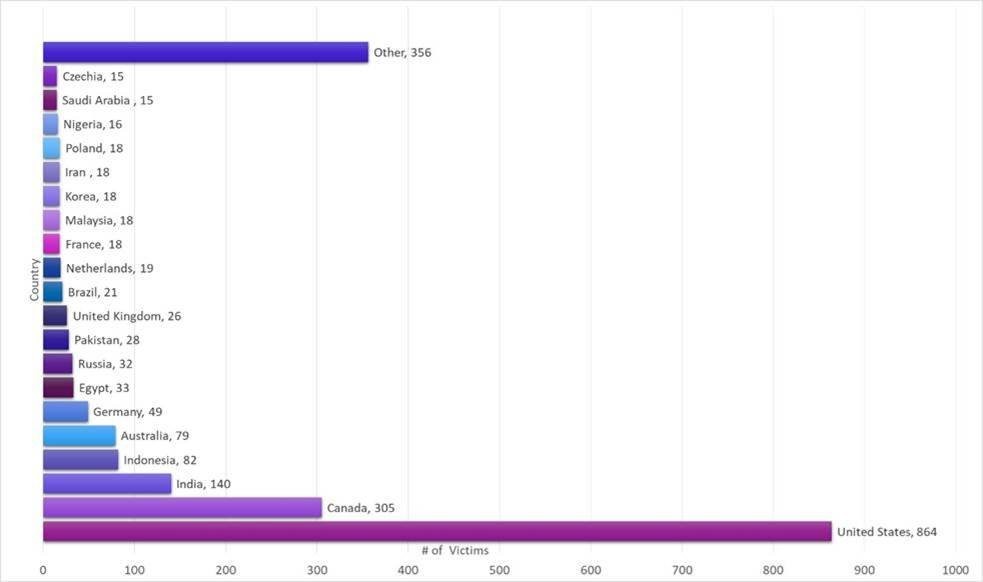
The number of victims affected. (Source – Check Point Research)
Specifically, Check Point Research has since documented 2170 unique victims. While most victims reside in the United States, followed by Canada and India, Check Point Research also saw some victims in Southeast Asia, with 18 victims in Malaysia and 82 in Indonesia.
“People need to know that they can’t immediately trust a file’s digital signature. What we found was a new ZLoader campaign exploiting Microsoft’s digital signature verification to steal sensitive information from users. We first began seeing evidence of the new campaign around November 2021. The attackers, whom we attribute to MalSmoke, are after the theft of user credentials and private information from victims,” said Kobi Eisenkraft, Malware Researcher at Check Point Software.
Eisenkraft added that they counted north of 2,000 victims in 111 countries and still counting. All in all, it seems like the Zloader campaign authors put great effort into defense evasion and are still updating their methods on a weekly basis. He strongly urges users to apply Microsoft’s update for strict Authenticode verification as it is not applied by default.
Microsoft has known about this security gap since 2012 and has attempted to fix it by releasing increasingly stricter file verification policies. However, for some reason, these remain disabled by default.
As such, Check Point Research has suggested the following safety tips to be practiced. Firstly, users should apply Microsoft’s update for strict Authenticode verification. Again, this is not applied by default. Secondly, avoid installing programs from unknown sources and sites. Lastly, avoid opening links or unfamiliar attachments received through email.
READ MORE
- The criticality of endpoint management in cybersecurity and operations
- Ethical AI: The renewed importance of safeguarding data and customer privacy in Generative AI applications
- How Japan balances AI-driven opportunities with cybersecurity needs
- Deploying SASE: Benchmarking your approach
- Insurance everywhere all at once: the digital transformation of the APAC insurance industry


