
Bitdefender Labs exposes deepfake videos in high-profile YouTube scams. (Generated with AI).
How deepfake videos are transforming YouTube crypto-scams
- Bitdefender Labs uncovers the rise of deepfake videos in YouTube crypto-scams.
- Bitdefender Labs reports significant subscriber and view count impacts on hijacked channels.
- Attackers are using real events to deceive and profit.
In recent months, stream-jacking attacks have become increasingly prevalent on major streaming platforms. Cybercriminals are focusing their efforts on compromising high-profile accounts, particularly those with substantial follower counts, to disseminate their deceptive messages to a broad audience.
As of October 2023, Bitdefender Labs researchers have been actively monitoring steam-jacking attacks targeting high-profile YouTube accounts, used to conduct various crypto-doubling scams.
In 2024, further investigation into these fraudulent takeovers and the use of YouTube accounts has unveiled new developments. Financially motivated threat actors are meticulously evolving their tactics to enhance the reach and efficiency of their actions, using carefully engineered content that closely mimics legitimate cryptocurrency-related news or announcements.
The deception of fake livestreams
Recent months have seen a steady evolution in these stream-jacking attacks. Bitdefender’s research highlights the advancement of cybercriminals in refining their methods to maximize impact, leveraging popular crypto events to potentially monetize fraudulent livestreams. These scams often disguise themselves under popular titles featured in mainstream media.
For example, during the “SpaceX Starship integrated flight test 2” event, attackers launched fake livestreams under names like “SpaceX Launch Starship Flight Test! Elon Musk gives update on Starship!” on compromised ‘verified’ channels, adding credibility to their deception. Analysis shows that many of these livestreams exhibited signs of artificially boosting viewers to increase trust among potential real viewers.
As previously noted, scammers often modify the names of impersonated entities on compromised accounts (e.g., using @spacex1[..] instead of @SpaceX).

SpaceX being used for stream-jacking attacks (Source – Bitdefender).
Bitdefender Labs has identified other premeditated scams based on widely known events.
Around November 30, a significant date for the SEC-XRP trial in the crypto world, multiple fake livestreams emerged with titles such as “Ripple XRP Case Reaching A HAPPY End – SEC Lose? Brad Garlinghouse LIVE,” “Ripple XRP BOOM! Case Reaching A HAPPY End – SEC Lose? Brad Garlinghouse LIVE,” and “Tomorrow Swell will send XRP? Brad Garlinghouse LIVE!”
Similarly, for the USSF-52 flight, titles like “SpaceX USSF-52 Mission Launch! Elon Musk gives update on Starship!” and “USSF-52 Mission Launch SpaceX! Elon Musk gives update on Starship!” were used.
It is evident that any high-profile news headline can be exploited for malicious activities. Over time, the scams have evolved from using famous names to coordinating elaborate campaigns based on real, interest-generating events.
Importantly, Bitdefender Labs notes that many compromised channels used in these scams have a large number of subscribers, some with more than 1 million and one with as many as 12.5 million. This makes them ideal vectors for threat actors to spread their fraudulent schemes.
Deepfake videos: the new frontier in cyber-scams
Scams reported in October 2023 initially involved looped videos from popular conference talks or other recordings. However, fraudsters have recently begun using deepfake technology to create convincing videos of prominent figures in cryptocurrency, adding an extra layer of credibility to their scams.
These skillfully engineered videos typically entice viewers to scan a QR code and send cryptocurrency, promising to double the amount. Some of these deepfakes are of decent quality and could easily deceive an untrained eye. To prevent detection by vigilant community members or victims, live chat on these videos is often disabled, except for selected channel members or long-time subscribers.
A new trend with these deepfakes is their use in YouTube advertisements, giving cybercriminals more flexibility to spread their scams (fraudsters can pay for these fake ads until they’re banned by YouTube).
While the videos are clearly crafted using deep generative models, the support chats on malicious websites do not seem to employ any advanced Large Language Model for responses.
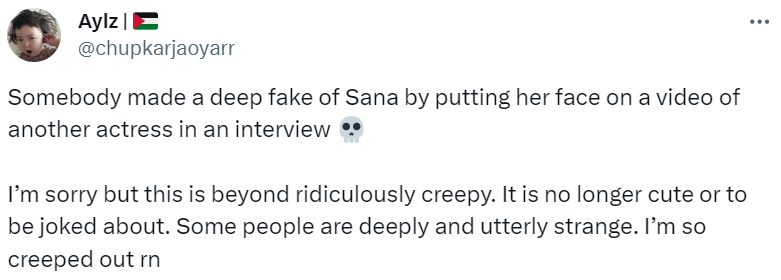
How someone can be tricked into thinking deepfakes are real? (source – X).
Understanding YouTube account takeovers
These takeovers typically begin with the compromise of YouTube access tokens through various methods. Once access is gained, attackers quickly revamp the channel to impersonate their chosen entity.
This automated process often includes modifying the channel name and handle, setting all existing videos to private, replacing the channel avatar and banner with images representing the impersonated entity, and removing or altering the channel’s description, links, and featured channels, sometimes redirecting to a malicious website promoting the crypto-doubling scam.
Live observations of these takeovers show a systematic approach. Initially, the name, handle, and avatar change, leaving existing content visible. Soon after, videos become private, and the banner changes, but the channel description and special videos remain. Within minutes, the channel is stripped of original content, leaving little resemblance to its original state, as seen in a takeover mimicking the official SpaceX channel.
However, these transformations are sometimes delayed or incomplete, resulting in the channel being banned before full changes can be implemented.
Exploiting current events for scams, including deepfake videos
Recent scams have capitalized on the Bitcoin ETF news coverage. Since late December 2023, fraudulent broadcasts featuring MicroStrategy and its former CEO, Michael Saylor, have surged, exploiting titles related to the Bitcoin ETF’s potential success.
These broadcasts often feature looped deepfakes of Michael Saylor encouraging participation in fake giveaways. The compromised channels adopt official MicroStrategy logos and banners, sometimes even linking to the official channel’s playlists to enhance credibility. The thumbnails of these videos are consistent across different instances. Variations of the channel name post-takeover include MicroStrategy US, Microstrategy Live, Micro Strategy, among others, often with subtle alterations like trailing spaces or parentheses.

YouTube stream-jacking involving Michael Saylor (Source – Bitdefender).
The associated fake websites mimic legitimate domains, featuring animations that create an illusion of ongoing transactions. However, these are randomly generated and not indicative of real activity.
In these deepfake videos, a faux Michael Saylor outlines the scam: viewers are prompted to watch for a QR code during the broadcast and scan it with their phone, without needing to register on any website. Deposits of Bitcoin are encouraged, with promises of an automated system doubling the amount sent back. The scam is positioned as user-friendly and hassle-free, even for those new to cryptocurrencies, with technical support available during the broadcast.
Unlike typical giveaways based on chance, this scam claims to guarantee double the Bitcoin deposited. Urgency is created by suggesting the offer is time-sensitive and dependent on limited funds.
Significant impact and scope of the scams
The scope and impact of these steam-jacking attacks are further highlighted by the significant metrics associated with the hijacked YouTube accounts. Bitdefender Labs reports some staggering figures that demonstrate the extent of the problem. These metrics include:
- The largest subscriber count of a hijacked account is approximately 12.5 million for one account.
- The highest view count for a hijacked account stands at around 3.87 billion views in total for one channel.
- The median subscriber count for these accounts is about 3,955, and the median view count is roughly 449,159.
- The top 10 hijacked channels alone have nearly 62.93 million subscribers and about 17.45 billion total views.
- The geographical spread of targeted accounts is vast, including the US (96 accounts), Brazil (75), India (74), Indonesia (49), Mexico (21), Turkey (15), Peru (14), Vietnam (13), Columbia (12), the UK (11), France (9), Spain (8), and more. This count excludes accounts already banned by YouTube.
These figures, which have shown a marked increase since the last report, indicate that the problem of steam-jacking and related crypto-scams is far from being resolved. The widespread nature and high-profile targets of these attacks underscore the urgency of addressing this growing cyber threat.
Profitability of crypto-doubling scams
An important question arises: how lucrative are these crypto-scams? The main source of income appears to be the cryptocurrencies received in the promoted wallets. An analysis of transactions associated with these wallets has revealed the following:
- Over 10 ETH and 12 BTC have been sent to these malicious wallets since January 2024.
- Most wallets show no transactions, possibly due to their recent creation, suggesting potential growth in activity.
- Cybercriminals employ methods to pass tokens through multiple wallets to hinder tracking.
- The largest amounts received in individual wallets are nearly 6 BTC and 2 ETH.
Potential earnings are estimated between approximately US$528,200 and US$600,500, depending on valuation dates. While it’s unclear if these transactions are from actual victims or part of the scam, the figures highlight the alarming profitability of these fraudulent operations, underscoring the urgent need for awareness.
READ MORE
- Safer Automation: How Sophic and Firmus Succeeded in Malaysia with MDEC’s Support
- Privilege granted, not gained: Intelligent authorization for enhanced infrastructure productivity
- Low-Code produces the Proof-of-Possibilities
- New Wearables Enable Staff to Work Faster and Safer
- Experts weigh in on Oracle’s departure from adland


