
A DDoS attack is a type of cyberattack that tries to make a website or online service unavailable by sending a lot of fake traffic to it. (Image generated by AI)
APAC records 38% increase in DDoS attacks in 2023
- DDoS attacks underwent a 38% surge in Asia Pacific in 2023.
- In 2023, there was a dramatic 118% increase in multi-vector attacks.
- Singapore experienced the strongest DDoS attack in the region.
DDoS attacks remain a major problem for organizations around the world. While ransomware and data breaches are still the primary concern, DDoS attacks are capable of wreaking havoc on organizations as well.
A DDoS (Distributed Denial of Service) attack is a type of cyberattack that tries to make a website or online service unavailable by sending a lot of fake traffic to it. The attacker uses many different devices, such as computers or smartphones, that are infected with malware and controlled remotely. These devices are called bots, and together they form a botnet. The botnet sends requests to the target website or service, overwhelming its capacity and preventing legitimate users from accessing it.
In Asia Pacific, a report from StormWall showed that DDoS attacks in 2023 experienced a 38% surge in the region, year-over-year. China, India, and Hong Kong were the top targets for DDoS attacks in their region, facing 26%, 18%, and 14% of the attacks respectively. These three nations suffered almost half of all regional attacks. As large and quickly developing economies, these countries represent appealing targets for hackers.
“In 2023, the Asia-Pacific region attracted both profit-seeking hackers and hacktivists, who were majorly influenced by the political affiliation of many Asian countries with Russia and ongoing armed conflicts. Towards the year’s end, APT and hacktivism-related attacks spiked majorly across all business sectors — both numerically and in terms of attack power. This trend coincided with the ongoing Israel-Hamas war, which began in October 2023,” the report read.
In Southeast Asia, Singapore experienced the strongest DDoS attack. The attack, which occurred in the last quarter of 2023, hit 1.4 Tbit/s and lasted 7 minutes. This indicates that by the end of the year, attackers could launch very powerful attacks.
Looking at the industries targeted, the telecommunications sector was hit the hardest, accounting for 31% of all DDoS attacks in APAC. This sector saw a 64% increase in attacks from the previous year. The finance and retail sectors followed with 18% and 16% of total attacks, respectively. In terms of the biggest YoY growth, the retail sector was in the lead with an 81% spike in attacks.
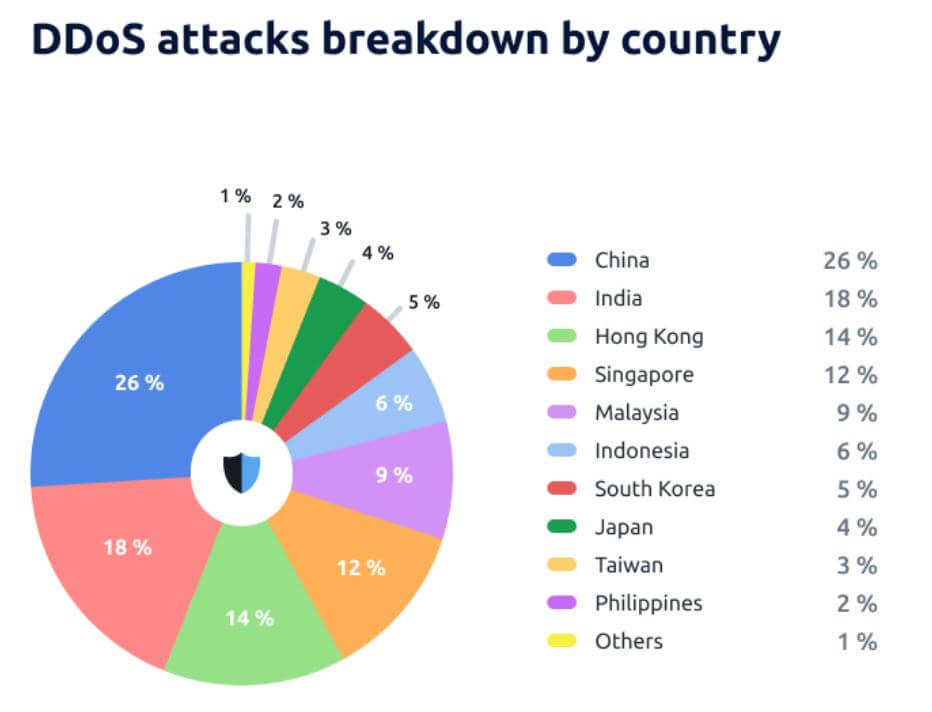
China had the most DDoS attacks in 2023. (Source – StormWall)
Multi-vector attacks up 118%
In 2023, there was a dramatic 118% increase in multi-vector attacks. This clearly highlights a shift towards more complex attack strategies. Multi-vector attacks target several infrastructure elements simultaneously and often combine DDoS and non-DDoS attack methods, which makes them particularly destructive.
StormWall’s data also showed that DNS attacks account for 6% of all DDoS incidents tracked in the APAC region. In contrast, around the world, only 3% of attacks target DNS.
“This difference really stood out in the last half of 2023, especially in the third and fourth quarters, when we saw a major spike in DNS attacks against companies in APAC. The most common types of DNS attacks were ‘Carpet Bombing’ DNS water-torture attacks, and the ‘Bits and Pieces’ method, which involves sending small bursts of junk traffic across many IP addresses simultaneously,” the report explained.
The rise in hacktivism is one of the factors that played a role in the popularity of multi-vector attacks. Throughout 2023, global politics shaped the threat of DDoS attacks. As more and more state-supported hacker groups got involved in cyber-warfare linked to worldwide conflicts, they created advanced tools and complex attack methods. Some of their techniques leaked into the public domain, making DDoS attacks more sophisticated overall.
DDoS attacks with bandwidth below 10 Gbit/s constituted 24% of the total DDoS traffic, typically directed at smaller or less-protected companies. The majority of attacks, accounting for 41%, fell within the 10 Gbit/s to 100 Gbit/s range. These attacks can be considered moderately strong, as they generate enough traffic to disrupt services. Notably, attacks in the 100 – 500 Gbit/s range made up 28% of the total, and attacks exceeding 500 Gbit/s — 7% of the total. The StormWall report categorizes them as “very strong,” posing a significant threat of clogging to enterprise-level networks.
Another interesting point from the report showed that 83% of DDoS attacks that targeted HTTP/HTTPS, were frequently executed by mixed and VM botnets. Notably, HTTP/HTTPS attacks were up 62% in 2023 compared to the previous year. Following this protocol, TCP accounted for 9% and DNS for 6%, which is twice the global average. Other protocols constituted the remaining 2%.
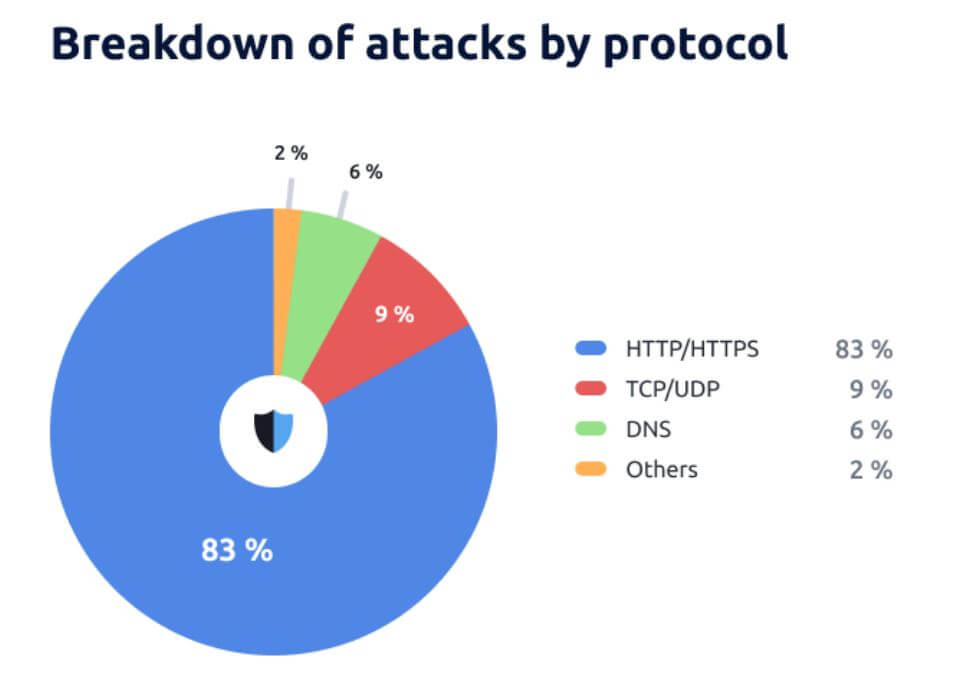
HTTPS attacks in the APAC region saw a significant rise in 2023, with a 62% increase
compared to 2022. (Source – StormWall).
Dealing with DDoS attacks
Given the increase in DDoS attacks in the region, businesses need to realize that such attacks can have various motives, such as revenge, blackmail, hacktivism, or cyberwarfare. These attacks can and will cause serious damage to the target, such as loss of revenue, reputation, or data.
As such, to prevent and mitigate DDoS attacks, some possible strategies are:
- Blackhole routing: This is a technique that discards all the traffic to the target, effectively isolating it from the Internet. This can stop the attack but also block legitimate traffic.
- Rate limiting: By limiting the number of requests or packets that the target will accept over a certain time window, businesses can reduce the impact of the attack. However, this may affect the quality of service for the legitimate users.
- Web application firewall (WAF): An application that monitors and filters the incoming traffic to the target, based on predefined rules or signatures. This can block malicious requests or packets but also requires constant updates and maintenance.
- DDoS protection service: The most commonly used by organizations, this service provides specialized solutions for detecting and mitigating DDoS attacks, such as distributed networks, traffic analysis, or scrubbing centers. While it can be costly to some businesses, it offers a high level of protection.
“We recommend implementing DDoS protection services from reliable providers. Key features to look out for are automation, the presence of local scrubbing centers and intelligent traffic filtering. These aspects ensure that junk traffic can be identified and neutralized without creating noticeable latency for real users,” the report concluded.
READ MORE
- Safer Automation: How Sophic and Firmus Succeeded in Malaysia with MDEC’s Support
- Privilege granted, not gained: Intelligent authorization for enhanced infrastructure productivity
- Low-Code produces the Proof-of-Possibilities
- New Wearables Enable Staff to Work Faster and Safer
- Experts weigh in on Oracle’s departure from adland




