
Today on “Triumphs of the FBI…”
FBI and UK crime agency finally disrupt Lockbit cyber-gang
- LockBit is one of the most notorious ransomware groups in the world
- Law enforcement agencies from 11 countries take down the LockBit group.
- The ransomware gang was, however, still operating on other platforms.
The LockBit cybercriminal group is one of the most notorious ransomware groups in the world. Known for its ransomware attacks, the LockBit group is also responsible for popularizing its Ransomware-as-a-Service model, in which it sells its ransomware to other operators for a cut of the profits of future attacks.
Active since 2019, the LockBit group has developed several variants of its ransomware, each causing more havoc than the last. The variants include .abcd, LockBit 1.0, LockBit 2.0, LockBit 3.0, and LockBit Green. The group has targeted various industries and countries, but especially the healthcare and education sectors in the United States, India, and Brazil.
According to the Cybersecurity and Infrastructure Security Agency (CISA), the gang extorted around US$91 million since 2020 in close to 1,700 attacks against various organizations in the country. The group is known for its fast and efficient encryption capabilities, its use of a tool called StealBit to automate the exfiltration of data, and its recruitment of insiders and network access brokers to help them breach their targets.
In November 2023, CISA, Federal Bureau of Investigation (FBI), Multi-State Information Sharing & Analysis Center (MS-ISAC), and Australian Signals Directorate’s Australian Cyber Security Centre (ASD’s ACSC) released a joint Cybersecurity Advisory (CSA) to disseminate IOCs, TTPs, and detection methods associated with LockBit 3.0 ransomware exploiting CVE-2023-4966, labeled Citrix Bleed, affecting Citrix NetScaler web application delivery control (ADC) and NetScaler Gateway appliances.
This was after the LockBit ransomware group leaked more than 43GB of files from Boeing after the company refused to pay a ransom. Other notable victims are Continental automotive giant, the UK Royal Mail, the Italian Internal Revenue Service, and the City of Oakland.
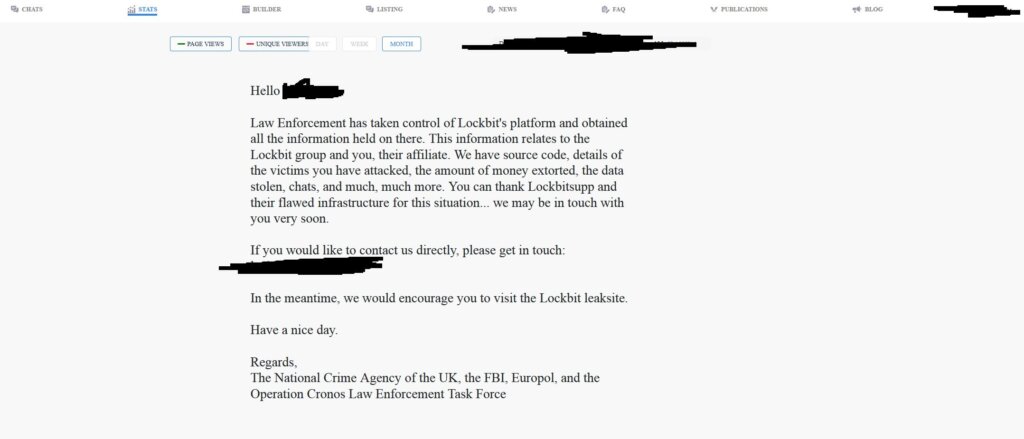
When a Lockbit affiliate tries to log into the Lockbit panel this is what they see. (Source – VX-Underground).
Disrupting the LockBit ransomware group
Law enforcement agencies have been trying their best to take down the LockBit ransomware group. Over the years, there have been several attempts at disrupting and derailing the gang’s modus operandi. Yet, the ransomware gang continues to evade law enforcement agencies.
In the end, law enforcement agencies came together to share intel and investigations which eventually led to the crippling of the ransomware gang’s operations. Operation Cronos is a joint operation between law enforcement agencies from 11 countries that was focused on taking down the LockBit group.
In a report by Bleeping Computer, there is now a banner displayed on LockBit’s data leak website which states that the site is now under the control of the National Crime Agency of the United Kingdom.
“The site is now under the control of law enforcement. This site is now under the control of The National Crime Agency of the UK, working in close cooperation with the FBI and the international law enforcement task force, ‘Operation Cronos,'” the banner states.
BleepingComputer also reported an NCA spokesperson confirming the disruption and that the operation is still ongoing and developing.
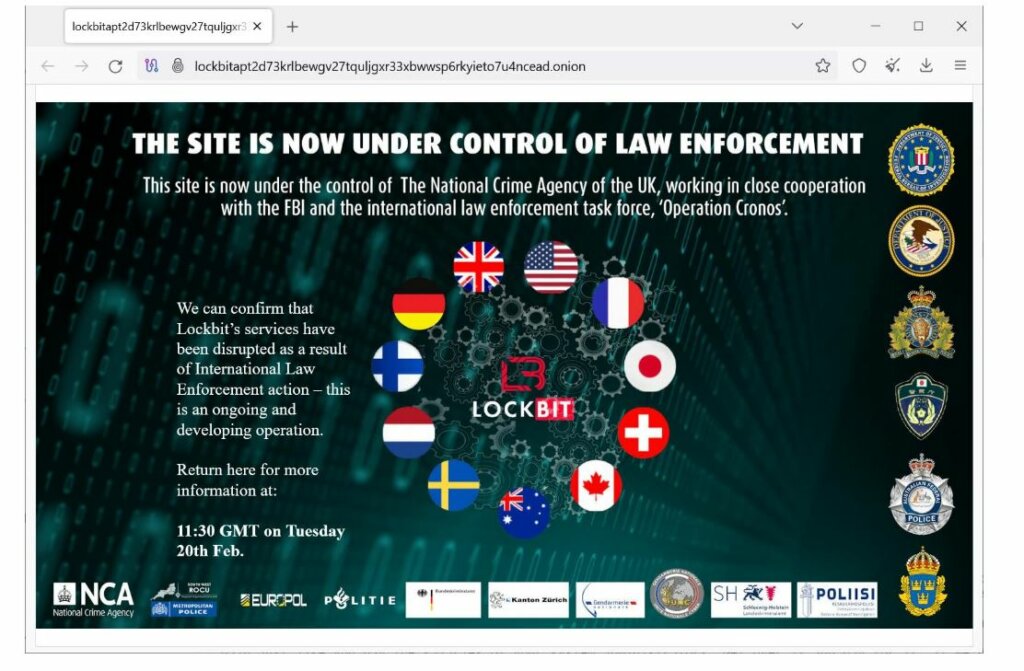
Lockbit’s leak site is no longer accessible. (Source – Bleeping Computer).
“The NCA can confirm that LockBit services have been disrupted as a result of international law enforcement action. This is an ongoing and developing operation,” said the spokesperson.
“We have hacked the hackers,” Graeme Biggar, director general of the National Crime Agency, told journalists. “We have taken control of their infrastructure, seized their source code and obtained keys that will help victims decrypt their systems.”
Apart from the data leak site, law enforcement agencies also took down LockBit’s affiliate panel and added a message saying LockBit source code, chats, and victim information were also seized.
“Law enforcement has taken control of Lockbit’s platform and obtained all the information held on there. This information relates to the Lockbit group and you, their affiliate. We have source code, details of the victims you have attacked, the amount of money extorted, the data stolen, chats, and much, much more,” the message displayed on the LockBit panel reads.
“You can thank Lockbitsupp and their flawed infrastructure for this situation… we may be in touch with you very soon. Have a nice day. Regards, The National Crime Agency of the UK, the FBI, Europol, and the Operation Cronos Law Enforcement Task Force.”
Meanwhile, CNN reported analysts saying that LockBit has members or criminal partners in Eastern Europe, Russia and China. Like other cash-flush ransomware groups, LockBit rents out its ransomware to “affiliates,” who use the malicious code in attacks, and then takes a cut of the ransom paid out by victims.
“It is highly unlikely core members of the LockBit group will be arrested as part of this operation since they are based in Russia,” Allan Liska, a ransomware expert with cybersecurity firm Recorded Future, told CNN.
Nonetheless, he said, the law enforcement seizure of LockBit’s website “means there will be a significant, if short-lived, impact on the ransomware ecosystem and a slow-down in attacks,” Liska said.
Reuters reported that the United States has charged two Russian nationals with deploying Lockbit ransomware against companies and groups around the world. Police in Poland and Ukraine made two arrests.
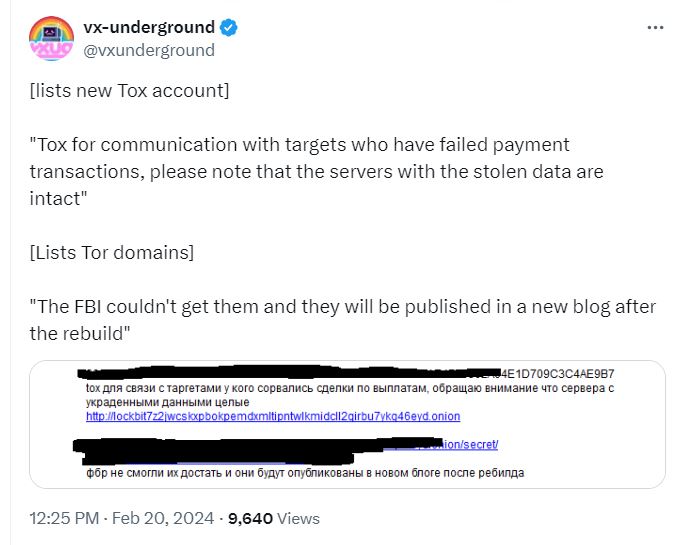
A Tweet showing activities of the group.
It’s not over yet
Despite law enforcement agencies taking control of several sites belonging to the LockBit group, the ransomware gang was still operating on other platforms. In fact, some reports show some of the gang’s other dark websites are still up. This includes sites used to host data and send private messages to the gang.
In a Tweet by VX-Underground, the LockBit group said it will now use Tox (a chat application) for communication “with targets who have failed payment transactions, please note that the servers with the stolen data are intact.” The group also stated that “the FBI couldn’t get them and they will be published in a new blog after the rebuild.”
The actions by law enforcement agencies could also challenge the ransomware gang to regroup and launch more severe ransomware attacks in the future. This is because the main culprits responsible for running these sites have yet to be arrested.
Chester Wisniewski, Director, Global Field CTO, Sophos commented, “We shouldn’t celebrate too soon though. Much of its infrastructure is still online, which likely means it is outside the grasp of the police and the criminals have not been reported to have been apprehended. Even if we don’t always get a complete victory, like has happened with Qakbot, imposing disruption, fueling their fear of getting caught and increasing the friction of operating their criminal syndicate is still a win. We must continue to band together to raise their costs ever higher until we can put all of them where they belong – in jail.”
As the end of the day though, this is still a big win as it is a rare and significant achievement in the fight against ransomware.
READ MORE
- Safer Automation: How Sophic and Firmus Succeeded in Malaysia with MDEC’s Support
- Privilege granted, not gained: Intelligent authorization for enhanced infrastructure productivity
- Low-Code produces the Proof-of-Possibilities
- New Wearables Enable Staff to Work Faster and Safer
- Experts weigh in on Oracle’s departure from adland




