Apple is upgrading its iMessage platform to enhance protection against forthcoming encryption-breaking technologies. Photo: NEW YORK, NEW YORK – FEBRUARY 01: People walk by an Apple store in a shopping mall in lower Manhattan on February 01, 2024 in New York City. Apple will report earnings Thursday afternoon after the close of the Closing Bell. The iPhone maker, which is to release its Vision Pro mixed-reality headset on Friday, has seen revenue decline for each of its past four reported quarters. Spencer Platt/Getty Images/AFP (Photo by SPENCER PLATT / GETTY IMAGES NORTH AMERICA / Getty Images via AFP)
Apple adds PQ3 protocol into iMessage
- Apple is upgrading its iMessage platform to enhance protection against imminent encryption-breaking technologies.
- iMessage now achieves Level 3 security using the new PQ3 protocol, providing robust defense against quantum attacks, a unique feature among messaging services.
- Apple confirms state-of-the-art encryption algorithms; no successful attacks have been detected yet.
In an era where digital privacy is paramount, Apple is integrating PQ3 into iMessage. This announcement marks a watershed moment in messaging security, propelling iMessage to unprecedented heights of protection. As the first widely deployed messaging app to achieve Level 3 security, what does the announcement mean for iPhone users, and why should they care?
At the heart of Apple’s PQ3 integration lies a revolutionary cryptographic protocol designed to withstand the challenges posed by quantum computing. Unlike traditional encryption methods, which may be vulnerable to future quantum attacks, PQ3 provides robust protection against even the most sophisticated adversaries. Using advanced cryptographic techniques, PQ3 ensures that iMessage conversations remain secure and private, regardless of the evolving threat landscape.
“To our knowledge, PQ3 has the strongest security properties of any at-scale messaging protocol in the world,” Apple’s Security Engineering and Architecture (SEAR) team stated in a blog post a week ago.
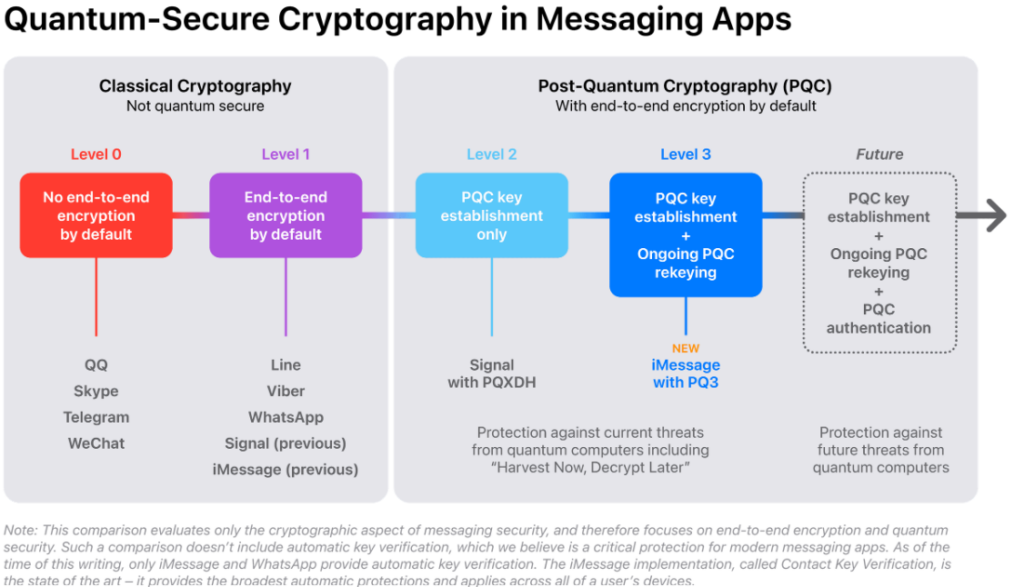
The new state of the art in quantum-secure messaging at scale. Source: Apple.
A quantum leap in messaging security
Traditionally, messaging platforms rely on classical public key cryptography like RSA, elliptic curve signatures, and Diffie-Hellman key exchange for secure end-to-end encryption. These algorithms are based on complex mathematical problems deemed computationally intensive for conventional computers, even with Moore’s law in play. However, the advent of quantum computing poses a new challenge.
A powerful enough quantum computer could solve these mathematical problems in novel ways, potentially jeopardizing the security of end-to-end encrypted communications. While quantum computers capable of decryption aren’t yet available, well-funded attackers can prepare by exploiting cheaper data storage. They accumulate encrypted data now, planning to decrypt it later with future quantum technology—a tactic termed “harvest now, decrypt later.”
When iMessage launched in 2011, it became the first widely available messaging app with default end-to-end encryption. Over the years, Apple has continually enhanced its security features. In 2019, the iPhone maker bolstered its cryptographic protocol by transitioning from RSA to elliptic curve cryptography (ECC) and safeguarding encryption keys within the secure enclave, increasing protection against sophisticated attacks.
“Additionally, we implemented a periodic rekey mechanism for cryptographic self-healing in case of key compromise. These advancements underwent rigorous formal verification, ensuring the robustness of our security measures,” the blog post reads. The cryptographic community has been developing post-quantum cryptography (PQC) to address the threat of future quantum computers. These new public key algorithms can run on today’s classical computers without requiring quantum technology.
Designing PQ3
Designing PQ3 involved rebuilding the iMessage cryptographic protocol to enhance end-to-end encryption, meeting specific goals:
- Post-quantum cryptography: PQ3 protects all communication from current and future adversaries by introducing post-quantum cryptography from the start of a conversation.
- Mitigating key compromises: It limits the impact of critical compromises by restricting the decryption of past and future messages with a single compromised key.
- Hybrid design: PQ3 combines new post-quantum algorithms with current elliptic curve algorithms, ensuring increased security without compromising protocol safety.
- Amortized message size: To minimize additional overhead, PQ3 spreads message size evenly, avoiding excessive burdens from added security.
- Formal verification: PQ3 undergoes standard verification methods to ensure robust security assurances.
According to Apple, PQ3 introduces a new post-quantum encryption key during iMessage registration, using Kyber post-quantum public keys. These keys facilitate the initial critical establishment, enabling sender devices to generate post-quantum encryption keys for the first message, even if the receiver is offline.
Furthermore, PQ3 implements a periodic post-quantum rekeying mechanism within conversations to self-heal from crucial compromise and protect future messages. This mechanism creates fresh message encryption keys, preventing adversaries from computing them from past keys.
The protocol utilizes a hybrid design, combining elliptic curve cryptography with post-quantum encryption during initial critical establishment and rekeying. Rekeying involves transmitting fresh public key material in line with encrypted messages, with the frequency of rekeying balanced to preserve user experience and server infrastructure capacity.
PQ3 continues to rely on classical cryptographic algorithms for sender authentication and essential verification to thwart potential quantum computer attacks. These attacks require contemporaneous access to a quantum computer and cannot be performed retroactively. But Apple noted that future assessments will evaluate the need for post-quantum authentication as quantum computing threats evolve.

A man uses an Apple iPhone in Beijing on September 12, 2023. (Photo by Pedro PARDO/AFP).
Why PQ3 on iMessage matters for iPhone Users
Integrating PQ3 into iMessage signifies a huge leap forward in privacy and security for iPhone users. With the exponential growth of data and the looming specter of quantum computing, traditional encryption methods face unprecedented challenges. PQ3 mitigates these risks by providing quantum-resistant protection, ensuring that your conversations remain shielded from future threats.
PQ3’s implementation in iMessage demonstrates Apple’s interest in safeguarding user privacy and staying ahead of emerging security threats. Beyond its robust encryption capabilities, PQ3 introduces a host of additional security features designed to enhance the overall integrity of iMessage. These include secure fundamental establishment mechanisms, cryptographic self-healing protocols, and real-time threat detection capabilities.
By incorporating these advanced security measures, Apple hopes to ensure that iMessage remains a bastion of privacy in an increasingly interconnected world.
When can iPhone users expect the update?
Support for PQ3 will begin with the public releases of iOS 17.4, iPadOS 17.4, macOS 14.4, and watchOS 10.4. Already available in developer previews and beta releases, PQ3 will automatically elevate the security of iMessage conversations between devices that support the protocol. As Apple gains operational experience with PQ3 globally, it will gradually replace the existing protocol within all sustained conversations throughout the year.
READ MORE
- Safer Automation: How Sophic and Firmus Succeeded in Malaysia with MDEC’s Support
- Privilege granted, not gained: Intelligent authorization for enhanced infrastructure productivity
- Low-Code produces the Proof-of-Possibilities
- New Wearables Enable Staff to Work Faster and Safer
- Experts weigh in on Oracle’s departure from adland