
Group-IB researchers also discovered that the GoldFactory Trojans target the Asia-Pacific region. (Image generated by AI)
There’s an iOS Trojan stealing faces
- A new iOS Trojan designed to steal users’ facial recognition data & identity documents, and intercept SMSs.
- Group-IB researchers discovered the GoldFactory trojans target the Asia-Pacific region.
- Discovery also marks a rare instance of malware targeting Apple’s mobile operating system.
A trojan virus is a type of malicious software that pretends to be something useful or harmless but actually performs negative actions on your computer or network. Unlike a true virus, a trojan cannot replicate itself, but it can open a backdoor for other malware, usually part of its methodology.
Trojans can also attack mobile devices. Mobile Trojans can perform various malicious actions, such as stealing personal data, sending SMS messages to premium numbers, opening backdoors for remote access, or launching DDoS attacks. Mobile Trojans can infect devices through phishing emails, malicious apps, or compromised websites.
While iOS devices are often considered to be more secure, Trojans are capable of infiltrating these devices as well. However, they are very rare and usually require the device to be jailbroken or, as is nearly impossible on iOS, to install apps from untrusted sources. A Trojan virus on an iPhone can disguise itself as a legitimate app or file, but secretly perform harmful actions.
According to a report by Group-IB, a new iOS Trojan designed to steal users’ facial recognition data, and identity documents, and intercept SMSs has been found. The Trojan, dubbed GoldPickaxe.iOS by Group-IB’s Threat Intelligence unit, has been attributed to a Chinese-speaking threat actor codenamed GoldFactory.
GoldFactory is responsible for developing a suite of highly sophisticated banking Trojans that also includes the earlier discovered GoldDigger and newly identified GoldDiggerPlus, GoldKefu, and GoldPickaxe for Android.
What makes the GoldFactor a more dangerous Trojan is its capability to exploit stolen biometric data. The threat actor utilizes AI face-swapping services to create deepfakes by replacing their faces with those of the victims. This new fraud technique could be used by cybercriminals to gain unauthorized access to the victim’s bank account or other data protected by facial recognition acting as 2FA.
Group-IB researchers discovered that the GoldFactory Trojans target the Asia-Pacific region, specifically, Thailand and Vietnam, impersonating local banks and government organizations. The discovery also marks the rare occurrence of malware targeting iOS devices.
Group-IB’s discovery also marks a rare instance of malware targeting Apple’s mobile operating system. (Source – Group-IB)
The new age of the gold rush in the Asia-Pacific
In October 2023, Group-IB suggested that the expansion of GoldDigger would extend beyond Vietnam. In less than a month, a new iOS malware variant started targeting victims from Thailand, subsequently named GoldPickaxe.iOS. Along with the iOS Trojan, the Group-IB team also identified an Android version of GoldPickaxe, named GoldPickaxe.Android.
According to media reports, in February 2024, a Vietnamese citizen fell victim to the malware. The individual carried out the operations requested by the application, including a facial recognition scan. As a result, cybercriminals withdrew money equivalent to more than US$40,000.
Overall, Group-IB identified four Trojan families and maintained the naming convention by using the prefix Gold for the newly discovered malware as a symbolic representation that they have been developed by GoldFactory.
In Thailand, the GoldPickaxe.iOS is disguised as a Thai government service app. It requests users to create a comprehensive facial biometric profile and take a photo of their identity card. Additionally, the code requests the user’s phone number to get more details about the victims, specifically seeking information about bank accounts.
Interestingly, Group-IB researchers note that the threat actor does not exploit any vulnerabilities. Instead, GoldFactory employs a multi-stage social engineering scheme to manipulate victims into granting all the necessary permissions, enabling the installation of malware.
Victims were persuaded to install a Mobile Device Management (MDM) profile, granting the threat actor complete control over devices. MDM offers a wide range of features such as remote wipe, device tracking, and application management, which cybercriminals take advantage of to install malicious applications and gain the information they need.
GoldPickaxe.iOS is the first iOS Trojan observed by Group-IB that combines the functionalities mentioned above, plus acting as a proxy for traffic for attackers’ connections. Its Android sibling has even more functionalities than its iOS counterpart, due to the more restrictive operating system of iOS.
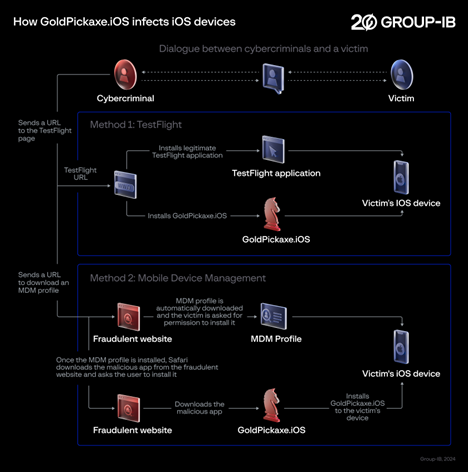
Group-IB researchers note that the threat actor does not exploit any vulnerabilities.
(Source – Group-IB)
A trojan targeting facial recognition in iOS and Android devices
GoldPickaxe doesn’t directly steal money from the victim’s phone. Instead, it collects all the necessary information from the victim to create video deepfakes and autonomously accesses the victim’s banking applications. During the research, Group-IB confirmed that the Trojan possesses the capability to prompt victims to scan their faces and submit ID photos.
Group-IB’s hypothesis suggests the cybercriminals use their own, allegedly Android, devices to log into victims’ bank accounts. The Thai police confirmed this assumption, stating that cybercriminals are installing banking applications on their Android devices and using captured face scans to bypass facial recognition checks and carry out unauthorized access to victims’ accounts.
“The surge in mobile trojans targeting the Asia-Pacific region can be attributed to GoldFactory,” said Andrey Polovinkin, Malware Analyst, Threat Intelligence team, Group-IB.
Debugging strings in Chinese were found throughout the malware variants and their C2 panels were also in Chinese. GoldFactory is a resourceful team skilled in various tactics, including impersonation, accessibility keylogging, fake banking website creation, fake bank alerts, fake call screens, identity, and facial recognition data collection. The team comprises separate development and operator groups dedicated to specific regions.
“The gang has well-defined processes and operational maturity and constantly enhances its toolset to align with the targeted environment showcasing a high proficiency in malware development. The discovery of a sophisticated iOS Trojan highlights the evolving nature of cyber threats targeting the Asia-Pacific region. In our assessment, it appears imminent that GoldPickaxe will soon reach Vietnam’s shores, while its techniques and functionality will be actively incorporated into malware targeting other regions,” Polovinkin explained.
For banks and financial organizations, Group-IB experts recommend implementing a user session monitoring system such as Group-IB’s Fraud Protection to detect the presence of malware and block anomalous sessions before the user enters any personal information.
Mobile device users should also use reputable antivirus apps to prevent and remove mobile Trojans. They should also avoid clicking on suspicious links or attachments, update the device and apps regularly, and only download apps from trusted sources. If there are any signs of infection, such as pop-up ads, battery drain, or unusual charges, users should scan their devices with a malware removal tool and delete any suspicious files or apps.
READ MORE
- Safer Automation: How Sophic and Firmus Succeeded in Malaysia with MDEC’s Support
- Privilege granted, not gained: Intelligent authorization for enhanced infrastructure productivity
- Low-Code produces the Proof-of-Possibilities
- New Wearables Enable Staff to Work Faster and Safer
- Experts weigh in on Oracle’s departure from adland




