(Photo by Saeed KHAN / AFP)
Malaysian banking customers are being targeted by malicious Android apps
Malaysian banking apps have been facing some serious challenges lately. Over the past few weeks, there have been reports of several major Malaysian banking apps not responding fast enough and customers having funds missing from their accounts.
While the banking apps are created to be secured, with built-in extra security features, and are regulated by governing financial bodies, the reality is, that banking apps are also vulnerable. In most cases, banking apps are targeted through third-party malicious apps.
In fact, ESET researchers have analyzed three malicious Android applications targeting customers of eight Malaysian banks. The researchers discovered that the ongoing campaign had begun in late 2021 with cyber attackers setting up fake websites that look legitimate to entice shoppers into downloading malicious applications.
From there, the threat actors steal banking credentials. Some of the fake websites even mirror the original site as they use similar domain names to the services they are impersonating.
According to ESET researcher Lukáš Štefanko, “to make the already couch-friendly approach of online shopping even more convenient, people are increasingly using their smartphones to shop. Smartphone purchases make up the majority of online shopping orders – most of them from vendor-specific applications.”
Distributed through Facebook ads, the campaign impersonated legitimate cleaning service Maid4u and tempted potential victims to download Android malware from a malicious website. Other impersonated services that are only available in Malaysia include Grabmaid, Maria’s Cleaning, YourMaid, Maideasy and MaidACall, offer cleaning services, and a pet store named PetsMore.
In January 2022, the MalwareHunterTeam identified three more malicious websites and Android trojans attributed to this campaign. Recently, ESET researchers also found four additional fake websites. All seven websites impersonated services that are only available in Malaysia.
The copycat websites do not provide an option to shop directly through them. Instead, they include buttons that claim to download apps from Google Play. However, clicking these buttons does not actually lead to the Google Play store, but to servers under the threat actors’ control. To succeed, this attack requires the intended victims to enable the non-default “Install unknown apps” option on their devices.
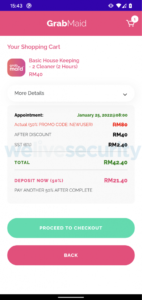
The shopping cart in a malicious application. (Source – ESET)
The modus operandi targets victims when they make payment for an order. The victims are presented with payment options, such as credit cards or transferring the required amount from their bank accounts.
After picking the direct transfer option, victims are presented with a fake FPX payment page and asked to choose their bank out of the eight Malaysian banks provided, and then enter their credentials. The targeted banks are Maybank, Affin Bank, Public Bank Berhad, CIMB Bank, BSN, RHB, Bank Islam Malaysia, and Hong Leong Bank.
The victims will then receive an error message informing them that the user ID or password they provided was invalid after submitting their banking credentials. At this point, the entered credentials have been sent to the malware operators. To make sure the threat actors can get into their victims’ bank accounts, the fake e-shop applications also forward all SMS messages received by the victim to the operators in case they contain Two-Factor Authentication (2FA) codes sent by the bank.
“While the campaign targets Malaysia exclusively, for now, it might expand to other countries and banks later on. At this time, the attackers are after banking credentials, but they may also enable the theft of credit card information in the future,” added Štefanko.
ESET Research has found the same malicious code in all three analyzed applications, leading them to conclude that they can all be attributed to the same threat actor. As such, users are advised to be extra vigilant when making payments through banking apps.
READ MORE
- Safer Automation: How Sophic and Firmus Succeeded in Malaysia with MDEC’s Support
- Privilege granted, not gained: Intelligent authorization for enhanced infrastructure productivity
- Low-Code produces the Proof-of-Possibilities
- New Wearables Enable Staff to Work Faster and Safer
- Experts weigh in on Oracle’s departure from adland