
The comeback of the infamous botnet Emotet, targeting mainly Japan and South Europe. (Source – ESET)
Emotet’s resurrection alarms cyber warfare
|
Getting your Trinity Audio player ready... |
- Post-2021 takedown, Emotet has led numerous spam campaigns.
- Mealybug, Emotet’s handler, continually upgrades and creates new modules.
- Emotet’s team works hard to dodge botnet tracking since their return.
Emotet, a crafty and formidable force in the realm of cyber threats, is recognized for its mercurial tactics, defining a new breed of cyber warfare. This sophisticated malware intermittently suspends operations, only to return with strategies of escalating concern, ensuring that global organizations remain in a state of constant vigilance.
Like a cockroach, the malware never goes away. Despite numerous campaigns to wipe out Emotet, it keeps getting resurrected, making a vengeful comeback on organizations all over the world.
ESET Research offers a thorough overview of Emotet’s behavior since its resurgence following a partial takedown. Launched in 2014 by the cybercriminal group known as Mealybug or TA542, Emotet has evolved from a banking trojan into a pervasive botnet menace.
In January 2021, an international operation involving eight countries, coordinated by Eurojust and Europol, managed to partially dismantle Emotet. However, by November 2021, Emotet was back in action, launching multiple spam campaigns before an unexpected cessation in April 2023.
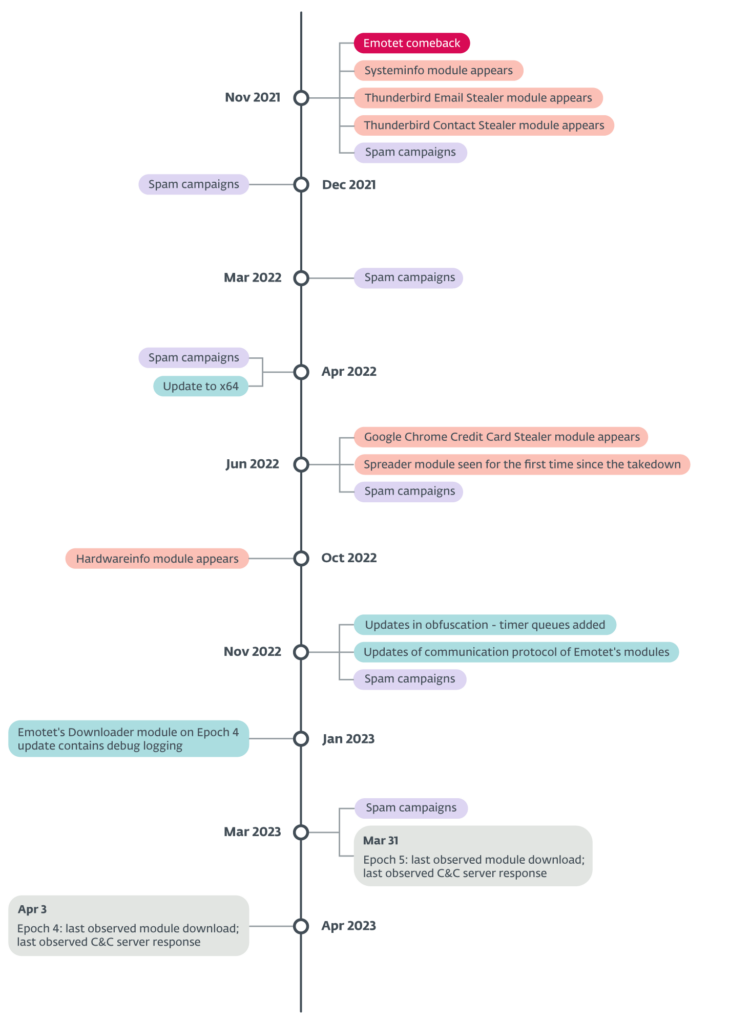
Cyber warfare in question: Timeline of interesting Emotet events since its return. (Source – ESET)
Emotet’s innovative malware dissemination
ESET’s findings reveal that the majority of attacks from Emotet’s 2022-2023 campaigns were directed at countries such as Japan, Italy, Spain, Mexico, and South Africa.
According to ESET researcher Jakub Kaloč, Emotet primarily spreads through spam emails. It has the ability to extract data from compromised computers and introduce third-party malware. Emotet’s operators target a wide demographic, compromising systems belonging to individuals, companies, and larger organizations.
From late 2021 to mid-2022, Emotet chiefly propagated its malware via malicious MS Word and MS Excel documents containing embedded VBA macros. However, a policy change by Microsoft in July 2022 to disable VBA macros in documents downloaded from the Internet forced malware groups like Emotet and Qbot to revise their strategies.
Kaloč explains that the loss of Emotet’s main attack vector pushed its operators to explore alternative methods of compromising their targets. “Mealybug started experimenting with malicious LNK and XLL files. However, by the time 2022 was ending, Emotet’s operators struggled to find a new attack vector that would be as effective as VBA macros. In 2023, they ran three distinctive malspam campaigns, each testing a slightly different intrusion avenue and social engineering technique,” says Kaloč. “However, the shrinking size of the attacks and constant changes in the approach may suggest dissatisfaction with the outcomes.”
Later, Emotet began incorporating a lure into MS OneNote. Despite alerts about possible malicious content, many users still clicked on it.
Escalating the cyber warfare
Upon its revival, Emotet received several enhancements. Notable changes include a switch in its cryptographic scheme and the introduction of new obfuscations to safeguard their modules. Since their return, Emotet’s operators have heavily invested in strategies to evade detection and supervise their botnet, introducing and improving multiple new modules to maintain profitability.
Mealybug has not only enhanced the Emotet malware to a 64-bit architecture, but they’ve also added a number of obfuscations to safeguard their modules. Of these new features, control flow flattening is especially noteworthy due to its ability to significantly hinder the examination and detection of essential components within Emotet’s modules.
Watch this video on what happens when a user is being infected with Emotet:
Mealybug has also implemented and enhanced a number of randomization techniques. The most notable among these are the randomization of the order of structure members and the randomization of instructions used to calculate constants (with constants being masked).
A significant update in the last quarter of 2022 saw modules start to use timer queues. Combined with control flow flattening, this sophisticated obfuscation significantly complicates code analysis and the tracing of execution flow.
Emotet primarily spreads via spam emails and often deceives users through its effective email thread hijacking technique. Before the takedown, Emotet utilized modules, namely the Outlook Contact Stealer and Outlook Email Stealer, capable of extracting emails and contact details from Outlook. However, acknowledging that not everyone uses Outlook, post-takedown Emotet expanded its target to include the free alternative email application – Thunderbird.
Emotet has the capability to introduce a module known as the Thunderbird Email Stealer onto compromised computers. As implied by its name, this module is proficient at extracting emails. It sifts through Thunderbird files that house received messages, specifically those in MBOX format, and pilfers data from various fields. These fields encompass the sender, recipients, subject matter, date, and the content of the message. Subsequently, all purloined information is transmitted to a Command & Control (C&C) server for additional analysis and utilization.
It also introduced a Google Chrome Credit Card Stealer module to capture credit card information stored in the Google Chrome browser.

Emotet detections by ESET: Jan 2022 – Jun 2023 (Source – ESET)
As per ESET’s research, Emotet botnets have been dormant since the beginning of April 2023, possibly in search of a new effective attack vector. From January 2022 to the present, most attacks identified by ESET have primarily targeted Japan (43%), Italy (13%), Spain (5%), Mexico (5%), and South Africa (4%).
READ MORE
- Safer Automation: How Sophic and Firmus Succeeded in Malaysia with MDEC’s Support
- Privilege granted, not gained: Intelligent authorization for enhanced infrastructure productivity
- Low-Code produces the Proof-of-Possibilities
- New Wearables Enable Staff to Work Faster and Safer
- Experts weigh in on Oracle’s departure from adland


