
Classiscam has been leveraging Telegram bots to assist with the creation of ready-to-use phishing pages. (Source – Shutterstock)
Telegram bots enabling scam-as-a-service
- Classiscam has been leveraging Telegram bots to help create ready-to-use phishing pages.
- Telegram bots can be easily set up by any user to deliver numerous automated task results.
- Australian brands mostly targeted by Classiscam in APAC.
Social media is increasingly becoming a haven for scammers. The amount of information on these platforms that is easily accessible to them makes the entire scamming process a lot faster and less hard work than it used to be. Scammers are able to pick their targets through public social media accounts and customize a scam to target them.
More often than not, scammers successfully ensnare their victims. Despite enforcement agencies clamping down on scamming activities, new ones pop up instantly and continue to target the vulnerable. The victims, who are normally those who are not very experienced in using digital platforms and services, are easily targeted by the scammers.
According to a report by Group-IB, scam-as-a-service operations are continuing to gain traction globally. One operator that has been successfully pursuing its campaign in 2023 is Classiscam. Classiscam is an automated scam-as-a-service designed to steal money and payment data.
The report indicates that Classiscam has been using Telegram bots to assist in creating ready-to-use phishing pages. The pages are reported impersonating companies in a range of industries, including online marketplaces, classified sites, and logistics operators.
Apart from stealing money and payment data, the phishing pages have also been stealing bank login credentials from unsuspecting internet users. Group-IB’s findings indicate that a total of 251 unique brands from 79 countries were featured on Classiscam phishing pages from H1 2021 to H1 2023.
In addition, the phishing templates created for each brand can be localized to different countries by editing the language and currency featured on the scam pages. As a result, one particular logistics brand was impersonated by “Classiscammers” targeting users in as many as 31 countries.
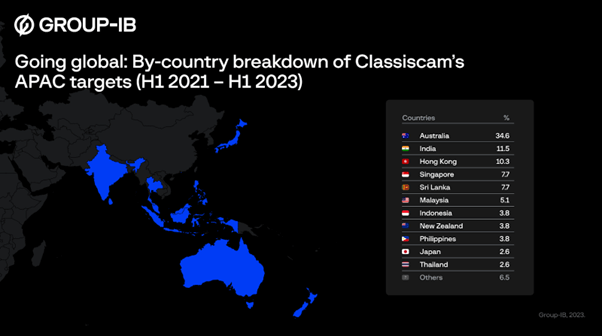
By-country breakdown of brands targeted in APAC Classiscam campaigns H1 2021 – H1 2023 (Source – Group-IB)
The rise of Telegram bots
Telegram bots are small, automated back-end programs that can be embedded in Telegram chats or channels, allowing any user to communicate and perform a function. The bots can be easily created and manipulated according to their users’ demands.
Telegram bots can be easily set up by users to perform a variety of automated tasks. This is why scammers are finding them increasingly reliable to run their scamming activities, especially in setting up scam pages.
Many Telegram bots can be integrated into Telegram channels for various use cases. For scamming-as-a-service, the scammers would most likely be using a bot that is automated to generate phishing sites by harnessing data from websites. Some bots can be used to prepare email templates and even prompt users for details.
An article on Bleeping Computer notes that Telegram has an advantage in the realm of scams due to its many features commonly found in modern social media applications, such as emojis, direct private chats, and a mobile application. The level of technical proficiency needed to find cybercrime channels and successfully make purchases is even lower than Tor, creating a democratization of cybercrime data.
Many channels offer free ‘samples’ of credentials, stealer logs, and data from breaches. These samples provide an easy way for users to ‘validate’ the effectiveness of a vendor’s offerings.
“Phishing kits of Telegram are readily available and often come with tutorials that make them easy to use for non-technical users. The kits are also sold at affordable prices, making them accessible to many cybercriminals. The rise of these kits on Telegram has made it easier for cybercriminals to launch attacks against businesses of all sizes,” explained Laone Moalosi, CTO and Co-founder at Cybertec Solutions in a LinkedIn post.
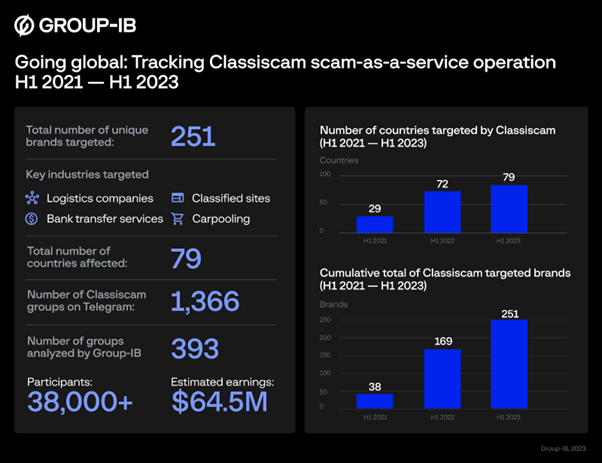
Classiscam overview, H1 2021 – H1 2023 (image – Group-IB)
Classiscam in APAC
Classiscam originally appeared in Russia, where the scheme was tried and tested before being launched across the globe. The scam-as-a-service affiliate program surged in popularity in the spring of 2020 with the emergence of COVID-19 and the subsequent uptick in remote working and online shopping.
In Asia Pacific, the brands targeted by Classiscam were mostly in Australia. Success there was followed by Classiscam operations in India, Hong Kong, Singapore, Sri Lanka and Malaysia. Since the second half of 2019, when the Group-IB Computer Emergency Response Team (CERT-GIB), in cooperation with the company’s Digital Risk Protection unit, first identified Classiscam’s operations, 1,366 separate groups leveraging this scheme have been discovered on Telegram.
Group-IB experts examined Telegram channels containing information pertaining to 393 Classiscam groups with more than 38,000 members that operated between H1 2020 and H1 2023. During this period, these groups made combined estimated earnings of US$64.5 million.
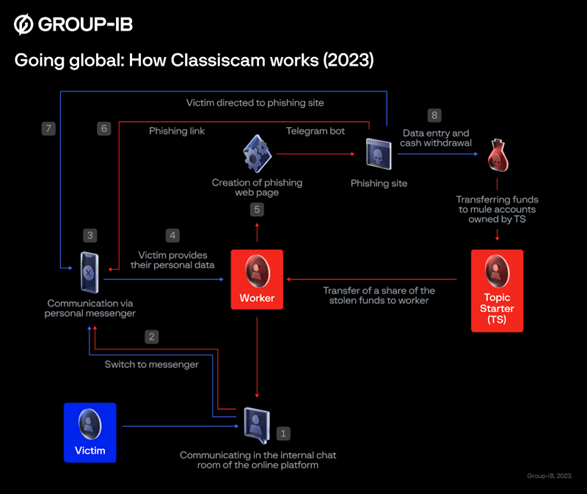
Classiscam scam-as-a-service scheme. (Source – Group-IB)
At the same time, Group-IB researchers have seen roles within scam groups become more specialized within an expanded hierarchy. Classiscam phishing pages can now include a balance check, which the scammers use to assess how much they can charge to a victim’s card, and fake bank login pages that they use to harvest users’ credentials.
Group-IB experts found 35 such scam groups that distributed links to phishing pages that included fake login forms for banking services. In total, Classiscam scammers created resources emulating the login pages of 63 banks in 14 countries. Among the targeted banks were some based in Belgium, Canada, the Czech Republic, France, Germany, Poland, Singapore, and Spain.
“Classiscam shows no sign of slowing down and the ranks of the Classiscammers are continuing to swell. Over the past year, we have seen scam groups adopt a new, expanded hierarchy, and roles within organizations are becoming increasingly specialized. Classiscam will likely remain one of the major global scam operations throughout 2023 due to the scheme’s full automation and low technical barrier of entry,” said Afiq Sasman, Head of Group-IB’s Computer Emergency Response Team in the Asia Pacific.
As always, users need to be vigilant when using social media and always be aware of any potential scams that can be targeting them. Social media and online hygiene should be prioritized while any suspicious sites and links should be avoided.
READ MORE
- Safer Automation: How Sophic and Firmus Succeeded in Malaysia with MDEC’s Support
- Privilege granted, not gained: Intelligent authorization for enhanced infrastructure productivity
- Low-Code produces the Proof-of-Possibilities
- New Wearables Enable Staff to Work Faster and Safer
- Experts weigh in on Oracle’s departure from adland




