
Boeing is assessing claims of a data breach by LockBit ransomware group. (Photo by Geoffroy VAN DER HASSELT / AFP)
LockBit ransomware strikes again!
- Boeing is assessing a suspected cybersecurity incident involving the LockBit ransomware group.
- LockBit is a Russian-linked cybersecurity gang that continues to be a global menace.
- LockBit plans to release Boeing data if it is not contacted by the aircraft manufacturer.
The LockBit ransomware group is probably one of the most well-organized cybercrime organizations in the world. Not only has the ransomware group continued to successfully infiltrate organizations, it has a very disciplined approach to make sure it gets what it wants.
According to the Cybersecurity and Infrastructure Security Agency (CISA), Lockbit was the most deployed ransomware variant in 2022 and continues to be prolific in 2023. Their targets normally involved organizations across critical infrastructure structures. This includes financial services, food and agriculture, education, energy, government and emergency services, healthcare, manufacturing, and transportation.
Also known for its Ransomware-as-a-Service model, LockBit ransomware attacks vary significantly in observed tactics, techniques, and procedures (TTPs). This variance in observed ransomware TTPs presents a significant challenge for organizations working to maintain network security and protect against a ransomware threat.
In Australia, LockBit made up 18% of the total reported ransomware incidents from April 2022 to March 2023. This figure includes all variants of LockBit ransomware, not solely LockBit 3.0. In 2022, LockBit was also responsible for 22% of attributed ransomware incidents in Canada, while CERT New Zealand received 15 reports of LockBit ransomware, representing 23% of 2022 ransomware reports.
According to the FBI, there have been around 1,700 LockBit incidents in the US. When it comes to ransomware payment, approximately US$91 million in ransom has been paid in the US since LockBit activity was first observed in the country on January 5, 2020.

The LockBit ransomware continues to evolve into stronger variants. (Image generated by AI)
The LockBit ransomware variants
The LockBit ransomware was first identified in September 2019. However, over the past few years, the ransomware has continued to evolve into newer and more menacing versions.
Here’s a look at the different variants of the LockBit Ransomware, as highlighted by the intelligence platform, Flashpoint.
- LockBit – The first variant that succeeded the original .abcd extension used by the ransomware group gained notoriety for its ability to deploy its encryption process in under five minutes.
- LockBit 2.0 – LockBit 2.0 evolved from the original LockBit variant by improving its ability to decode strings and codes faster to avoid detection. Once the variant has established administrative privileges, the encryption process begins.
- LockBit 3.0 – launched in late June 2022, LockBit 3.0 continued the trend of increasing encryption speed to avoid security detections. The malware uses anti-analysis techniques, password-only execution, and command line augmentation. LockBit 3.0 also introduces the first recorded ransomware bug bounty program, calling for users and security researchers to report any bugs to the ransomware group in exchange for financial reward.
- LockBit Green – the latest variant was revealed by VX-Underground and appears to be a standard ransomware variant targeting Windows environments.
- Lockbit for Mac – In May 2023, Flashpoint discovered that LockBit had begun developing a macOS version of LockBit ransomware – however, it could not be easily executed on the devices.
The LockBit ransomware group claims to have data from Boeing.
Boeing is the latest target of LockBit ransomware
Boeing is the latest target LockBit claims to have compromised. VX-Underground reported that LockBit has claimed to have a huge amount of sensitive data from the aircraft manufacturer.
Bloomberg reported that the ransomware group also posted a countdown clock for Boeing and claimed it held a “tremendous amount” of sensitive material that it was prepared to publish. The group has given Boeing the deadline of November 2nd by which to contact it.
A Boeing spokesperson said the company is assessing the claim. Apart from manufacturing commercial jets, the American multinational aircraft company also designs, manufactures, and sells rotorcraft, rockets, satellites, telecommunications equipment, and missiles worldwide. The company also provides leasing and product support services. It has yet to be confirmed which area in particular – if any – has been compromised by the ransomware group.
About a year ago, a Boeing subsidiary that distributes airspace safety notices to pilots also experienced a cybersecurity incident. Jeppesen, which provides electronic notices to air mission bulletins and applications for in-flight management tasks, experienced a technical issue which was a cyber-incident.
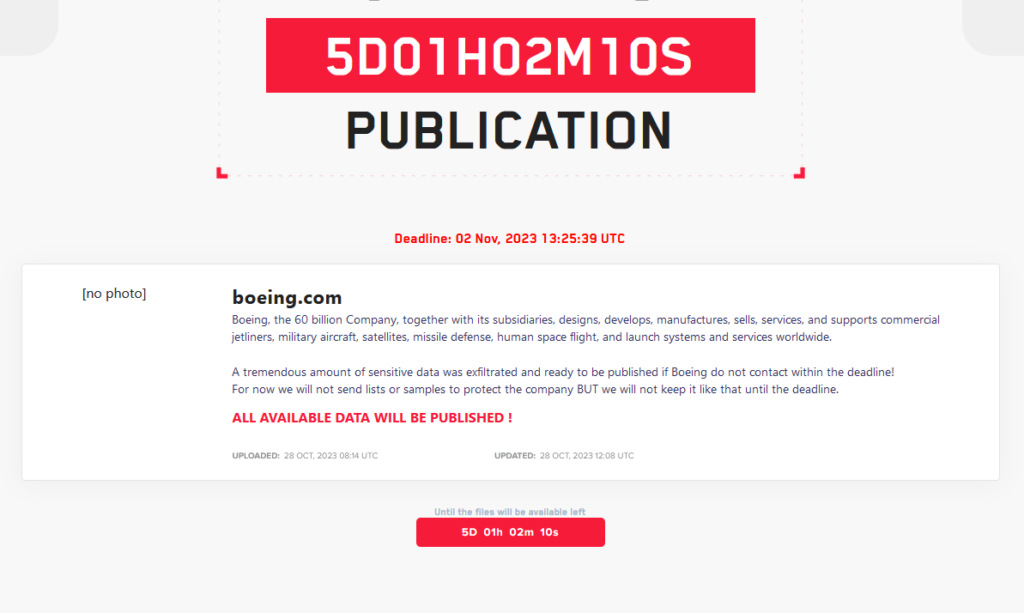
A screenshot of the note from LockBit ransomware. (Source – VX-Underground)
Ransomware in aviation
A few months earlier, another aircraft manufacturer, Airbus, also experienced a cybersecurity incident. Airbus, a European aerospace giant, has been investigating a cybersecurity incident following reports that a hacker posted information on 3,200 of the company’s vendors to the dark web.
A report from cybercrime intelligence company Hudson Rock stated that a threat actor using the moniker “USDoD” posted on BreachForums that they obtained access to an Airbus web portal after compromising the account of a Turkish airline employee. The hacker claimed to have details on thousands of Airbus vendors, including names, addresses, phone numbers and emails.
Meanwhile, airline companies also continue to be targeted by cybercriminals all over the world. From American Airlines to Cathay Pacific, millions of accounts continue to be compromised by cybercriminals. While most of the cyberattacks have been focused on stealing customer data, some have also caused more serious problems.
Airline companies continue to build on their cybersecurity, but most cyberattacks occur due to cybercriminals having access to employee credentials. While it is unsure if the Boeing hack was also caused by this intrusion method, the clock is now ticking for the aircraft giant to address the issue.
Most law enforcement and cybersecurity companies do not recommend paying a ransom as there is no guarantee that the cybercriminals will keep to their word. But LockBit is a well-organized cybercrime group, so it will be interesting to see how Boeing deals with the situation.
READ MORE
- Safer Automation: How Sophic and Firmus Succeeded in Malaysia with MDEC’s Support
- Privilege granted, not gained: Intelligent authorization for enhanced infrastructure productivity
- Low-Code produces the Proof-of-Possibilities
- New Wearables Enable Staff to Work Faster and Safer
- Experts weigh in on Oracle’s departure from adland






