
The Android malware mining more than just gold from your account. (Source – Group-IB)
This GoldDigger can drain your bank account – No, it’s an Android malware not a person
- GoldDigger, a new Android malware, targets 50+ Vietnamese financial apps.
- With digital finance on the rise, the need for top-tier security is paramount.
- The Android malware exploits an accessibility aid to get all your details.
As digital banking, e-wallets, and cryptocurrency platforms increasingly become integral to modern finance, their ease and worldwide reach have been transformative. Yet, this digitization hasn’t been without its downsides. The allure of easy access has caught the eyes of cybercriminals, who quickly exploit and benefit from the unwary in this burgeoning digital domain.
Group-IB stumbled upon an Android Trojan which is interested in over 50 Vietnamese banking apps, e-wallets, and cryptocurrency wallets, its prime objective being unauthorized fund transfers. This Trojan, dubbed “GoldDigger” by Group-IB’s Threat Intelligence division experts, has left its digital footprints since at least June 2023.
This devious software represents a Vietnamese governmental entity and an energy firm. Its modus operandi involves leveraging the Android Accessibility service not to aid those with disabilities but to obtain personal data illicitly, siphon off banking details, intercept text messages, and conduct various unauthorized actions. The scale of the compromise, in terms of the number of affected devices and the financial implications, is still under wraps.
Upon detecting this threat, Group-IB quickly alerted its Threat Intelligence customers. Not stopping there, the Computer Emergency Response Team of Group-IB (CERT-GIB) took a proactive stance, notifying the official National CERT of Vietnam (VNCERT) and ramping up its public awareness campaign.
A crafty approach to digital deception
This Trojan first blipped on Group-IB’s radar in June 2023. The analysts from the Threat Intelligence section found a network of over ten counterfeit websites, masterfully mimicking Google Play Store pages and legitimate company sites. Some even went to the extent of adding user testimonials and the emblem of Vietnam to enhance their ruse.
These carefully crafted sites had a single-minded purpose: to hoodwink visitors into downloading the GoldDigger malware.
A naming clue was the Android activity tag “GoldActivity” in the application file. The exact mode of initial propagation eludes Group-IB, but there’s a high likelihood that the Trojan’s creators used direct messaging platforms or classic phishing tactics. Group-IB unearthed two distinct versions of GoldDigger, each masquerading as a Vietnamese government site or a local energy provider.
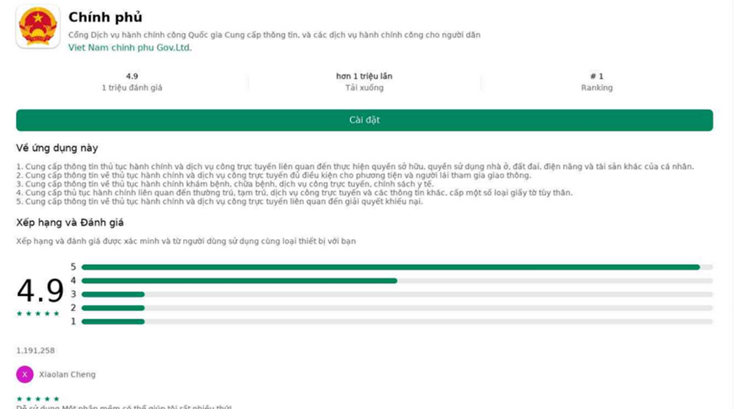
Counterfeit website propagating GoldDigger. (Source – Group-IB)
Upon activation, GoldDigger promptly seeks the user’s permission to access the Android Accessibility Service. This genuine service, which aims to help those with disabilities, becomes the Trojan’s tool for overseeing and tweaking device functionalities.
When users unintentionally provide Accessibility Service access to the Trojan, they inadvertently grant GoldDigger a golden ticket to obtain confidential data like passwords, read text messages, mimic user behaviors, and steal login details. GoldDigger remains vigilant, watching over 51 specific Vietnamese financial and e-wallet apps. Once it grabs user details, it promptly forwards the data to its command centers.
A robust password remains a critical shield against unauthorized account access. As cybercriminals deploy advanced brute force methods, it’s vital to use unpredictable combinations. A strong password acts as a secure vault door, protecting digital assets. Diversifying passwords for various applications ensures that a breach in one doesn’t compromise others. Modern password managers simplify handling strong passwords, and for added security, mix uppercase lowercase letters, numbers, and symbols. Avoid predictable passwords tied to personal data.
Multifactor authentication (MFA) provides another layer of defense. While two-factor authentication (2FA) usually requires a secondary verification like an SMS, MFA adds multiple layers, making unauthorized access harder. Beyond SMS-based 2FA, tools like Google Authenticator, Authy, or hardware tokens like YubiKey provide enhanced security.
Potential future targets for the Android malware
What sets GoldDigger apart is its utilization of Virbox Protector—a genuine software specializing in advanced data obfuscation and encryption. This is a clever move bythe malware developers, making it challenging for cybersecurity experts to decipher and understand their malevolent code, helping the malware evade standard fraud detection mechanisms. Yet, Group-IB’s Fraud Protection suite has the prowess to spot GoldDigger’s presence.
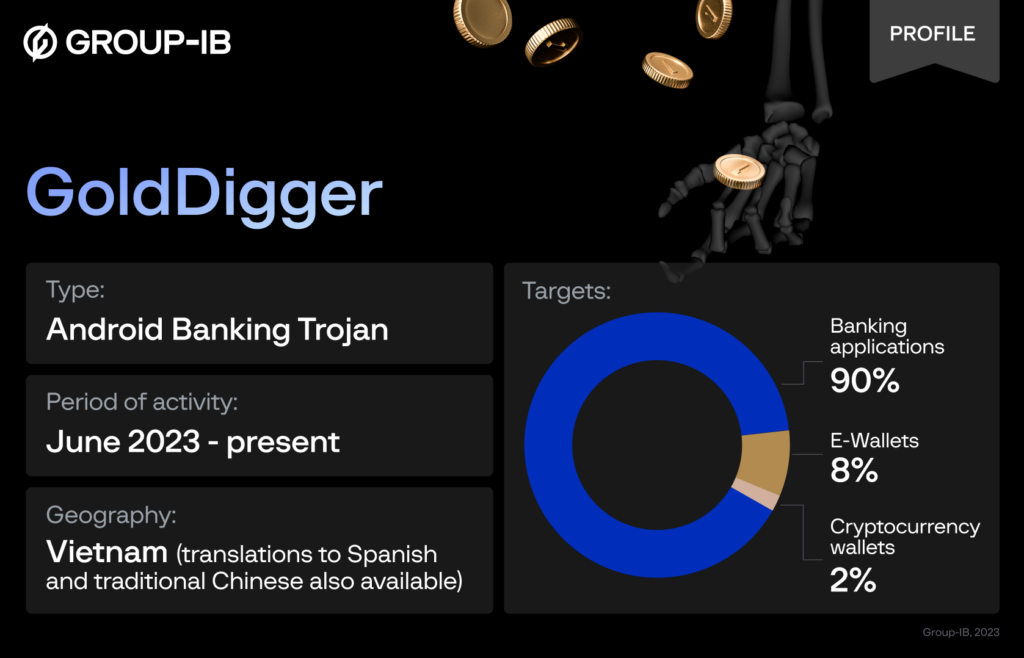
Deep dive into GoldDigger. (Source – Group-IB)
Anh Le, spearheading business development for Group-IB in Vietnam, highlighted that GoldDigger is currently centering its focus on Vietnamese targets. But there’s a twist: the malware has Spanish and traditional Chinese linguistic versions. This suggests that the perpetrators might be planning to cast their net wider, targeting Spanish and Chinese-speaking nations soon.
Nexus: Another player in the Android malware game
GoldDigger isn’t alone in the threat landscape. A report from TechRadar shed light on a “new” botnet named Nexus, which debuted on the underground markets recently. Interestingly, research from Cleafy indicates Nexus has been operational since June 2022, bearing a stark resemblance to another Android banking malware spotted in 2021. The allure of Nexus is its MaaS (Malware-as-a-Service) model, where affiliates can rent Nexus for a mere US$3,000 monthly—a bargain, given the potential returns.
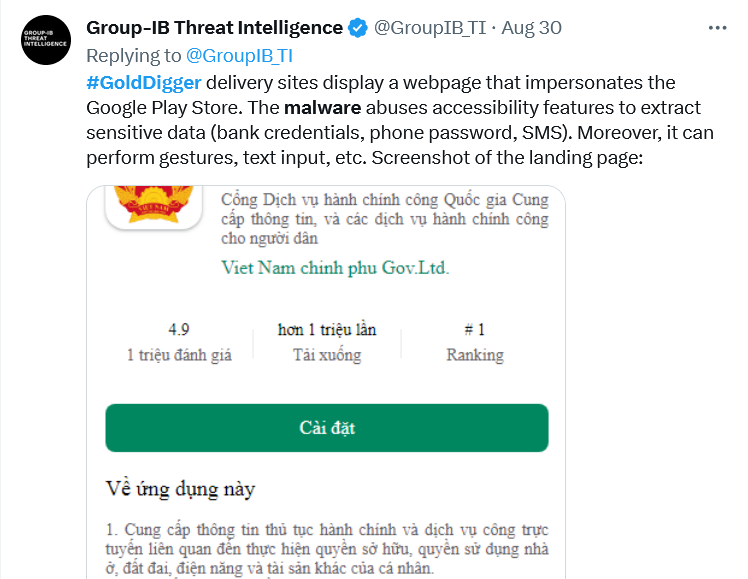
GoldDigger is particularly unscrupulous about getting your details.
Nexus can discreetly record user keystrokes, aiming to lift passwords from banking apps. Its real threat, however, is its ability to nullify even two-factor authentication systems by using accessibility features that expose SMS and Google Authenticator codes. Post-acquisition of these codes, Nexus can even turn off the SMS-based 2FA, making account recovery a Herculean task.
But how does Nexus infiltrate Android devices? Android Police reveals that Nexus disguises itself as a genuine app, bundling its Trojan component, and is available on dubious third-party Android app stores. The challenge is the lack of clarity on which apps are infected, making prevention a guessing game.

Third party app stores can be malicious if you’re not careful. (Source – Pexels)
The domino effect: from breach to economic fallout
Trust is a cornerstone in digital finance. A single security breach can shatter that trust, potentially leading to decreased user adoption and an exodus to plstforms perceived to be safer. Such shifts can significantly impact institutions’ revenue and market presence.
Beyond the immediate threat of stolen funds, cyberattacks can result in hefty regulatory fines, especially if negligence in cybersecurity protocols is evident. Institutions may also face legal challenges, compensation costs to affected users, and hefty resources to mend the breach.
Long-term impacts of significant breaches include potential partnership setbacks, plummeting stock prices, and heightened regulatory scrutiny. Institutions may then need to recalibrate their strategies, rebuild their reputation, and bolster their cybersecurity infrastructure.
As the digital finance realm continues its expansion, understanding these challenges and actively working towards mitigating them becomes not just advisable but imperative for both individuals and businesses.
“Based on our current detection, no apps containing this malware are found on Google Play. Users are protected by Google Play Protect, which can warn users or block apps known to exhibit malicious behavior on Android devices with Google Play Services,” a Google spokesperson emphasized.
READ MORE
- Safer Automation: How Sophic and Firmus Succeeded in Malaysia with MDEC’s Support
- Privilege granted, not gained: Intelligent authorization for enhanced infrastructure productivity
- Low-Code produces the Proof-of-Possibilities
- New Wearables Enable Staff to Work Faster and Safer
- Experts weigh in on Oracle’s departure from adland






