
The motive behind a series of malware attacks (“ONI”) on Japanese businesses is unclear. Source: Shutterstock
Mysterious 鬼 (“devil”) malware’s motives unknown
A mysterious cyber attack has been hitting Japanese businesses’ computers, the motives of which are unclear. While monetary gain seems, on the surface, to be the underlying reason for the spread of infection, it appears to be only an afterthought or a cover for the unknown culprits.
The tale begins some months ago when a ransomware called ONI (鬼 which can be translated as “devil”) began to spread through Japanese companies. Initially, it was not known how the malware was being spread.
However, latest findings by cybersecurity company Cybereason have shown that it was propogated by means of a compromised Word document inside a .zip file. On opening the document after decompression, a script fired up (written in Microsoft’s proprietary VBScript) which downloaded a variation on Ammyy Admin — a genuine remote administration application — which was a remote access trojan (RAT).
This particular RAT has been found in the wild since as far back as December 2016 and its targets have been entirely commercial organizations.
The malware then spent between three and nine months on the network, during which time it traversed across the company’s network and attempted to gain control of key machines such as domain controllers (DCs) and Active Directory (AD) servers.
This is where the tale starts to get more interesting.
The movement across the companies’ networks was, it is postulated, enabled using the exploit known as EternalBlue, which emanated originally from America’s National Security Agency (NSA). EternalBlue’s activities can be prevented by means of the application of a security update from Microsoft, but this had not been applied on the affected machines, which all still had SMB version 1 enabled (a network protocol mostly used by Windows machines).
During the time of the malware’s presence on infected machines, its activities were not detected, nor are they known now. Infection only became apparent at the end of the attack phase, when hundreds of machines all encrypted themselves at the same time — both the ONI-infected systems and DC & AD servers.
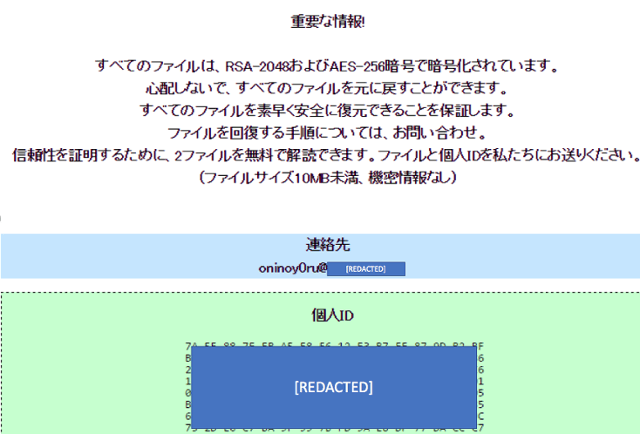
The demand for money produced by ONI; possibly bogus. Source: Cybereason
The malware used to compromise these more important systems was a different version of ONI, which is being termed MBR-ONI, as this particular nastiness both encrypts the actual file system (in addition to individual files) and replaces & scrambles the master boot record. The MBR is the piece of code on IBM-PC compatible machines that usually launches the operating system at boot.
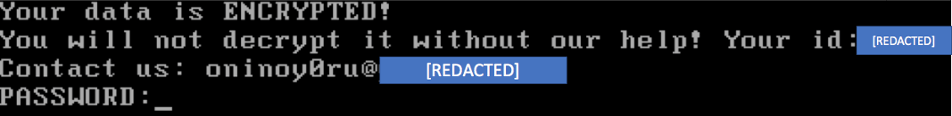
A compromised master boot record screen, quoting the same email address as the ONI malware’s message. Source: Cybereason.
At the end of the attack period, the compromised domain controller would push a batch script to all infected machines, which would wipe the Windows event logs on each; this is being seen as an attempt to cover the traces of any illicit activity and hides the attackers’ motives. Then the ONI malware was executed, which encrypted machines’ files, right across the network.
On the AD and DC, MBR-ONI was also executed, with the deeper level encryption taking place, as described.
It seems that another legitimate product’s code was used by MBR-ONI. DiskCryptor is an open-source encryption tool which is freely available. This, alongside the malware attack’s use of Ammyy Admin shows the blurred lines between causality and effect, analogous to the issue of gun ownership: is it guns, or guns’ users that cause the damage?
Cybereason’s researchers say they are skeptical that the attacks were meant for monetary gain, although the attack code in both instances (ONI and MBR-ONI) did show messages to users, a message which will be familiar to an unfortunate number of us these days: pay up or else.
However, the controllers and servers infected with MBR-ONI could not have been differentiated one from another by the attackers, so decrypting them (after payment, theoretically) seems not to have been in the plan.
The attack seemed, therefore, to be deliberately confusing: was it ransomware for monetary gain, or a so-called “wiper”, which merely encrypts data for maximum damage to its targets? If it was a wiper attack, why pause for months before invoking the malicious code?
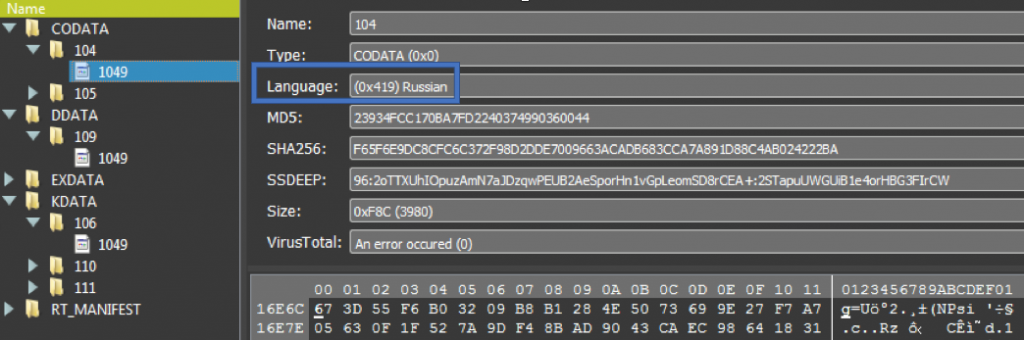
References to Russian language as found in the ONI malware. Source: Cybereason.
A clue — or a red herring — may have been found in the guts of ONI, where there were traces of the Russian language. This could mean that either the “ransomware”‘s author(s) were Russian, or the attacks were carried out by Russians, or, none of the above…
What happened during the unusually long gestation period between infection and encryption, no-one really knows. And as to the motives of the attackers, we will have to wait and see.
READ MORE
- Spectre & Meltdown highlight tech industry’s disparities
- You don’t have to be a cybersecurity expert to protect your small business
- Are the latest cyber threat reports an ignorable sales pitch?
- How US$1000 (or nothing) buys malware access to your network
- Bangladesh and Pakistan are the most vulnerable to cyberattacks in Asia




