
SideCopy has been using a vulnerability in WinRAR to deploy various RATs. (Generated with AI)
Watch out for RATs targeting your computers – Not a rodent, but a security vulnerability
- SideCopy, linked to Pakistan, exploits a WinRAR security vulnerability.
- SideCopy’s use of RATs and phishing underscores the increasing complexity of cyberattacks.
- Don’t let RATs steal your private data.
Recent cyberattacks on Indian government institutions have uncovered the operations of a Pakistani-linked cyberthreat organization, SideCopy, using a particular security vulnerability.
Active since 2019, this group primarily targets Indian and Afghan institutions and is considered an offshoot of the Transparent Tribe, also known as APT36, highlighting its affiliations and range of operations.
The Hacker News has revealed that SideCopy has been using a vulnerability in WinRAR to deploy various remote access trojans (RATs) like AllaKore RAT, Ares RAT, and DRat. Beyond this, SideCopy employs phishing and exploits other vulnerabilities to spread malware. SEQRITE, an enterprise security company, detailed this campaign as multi-dimensional, notably targeting Linux systems with a customized Ares RAT, indicating the campaign’s adaptability and strategic targeting.
What are RATs, actually?
To comprehend the seriousness of RATs, knowing what they do is essential. A RAT allows a cyberattacker to control an infected device completely. This access lets the attacker retrieve sensitive data, such as user credentials, passwords, and financial information. RATs can track online activities, collect browsing histories, emails, and chat records, and even take control of webcams for intrusive surveillance.
Earlier in May, SideCopy was associated with a phishing operation using lures related to India’s Defence Research and Development Organization (DRDO) to spread malware designed to steal information. Following this, the group has been involved in other phishing attacks against the Indian defense sector, using ZIP file attachments to distribute Action RAT and a new .NET-based trojan capable of executing 18 distinct commands.
The decision of SideCopy to concentrate on Linux systems is strategic. It likely stems from India’s migration from Microsoft Windows to a Linux-based operating system, Maya OS, within its government and defense realms. This strategic transition highlights SideCopy’s capacity to adapt and target systems based on their significance and widespread use.
SideCopy is known to use similar TTPs
Adapting to a security vulnerability like phishing
SEQRITE has uncovered two new phishing strategies employed by SideCopy, targeting both Linux and Windows systems. The first involves a Golang-based ELF binary that facilitates the Linux version of Ares RAT, capable of numerous functions, including file enumeration and screenshot capturing.
The second strategy exploits a vulnerability in WinRAR to activate malicious code, leading to the introduction of AllaKore RAT, Ares RAT, and new trojans named DRat and Key RAT, with DRat able to process up to 13 commands from its control server.
Sathwik Ram Prakki, a researcher at SEQRITE, notes that SideCopy is continually expanding its range of tools, including exploiting zero-day vulnerabilities. The group consistently targets Indian defense agencies with various RATs. Additionally, APT36 regularly enhances its Linux tools and shares its Linux-based strategies with SideCopy to deploy an open-source Python RAT known as Ares.
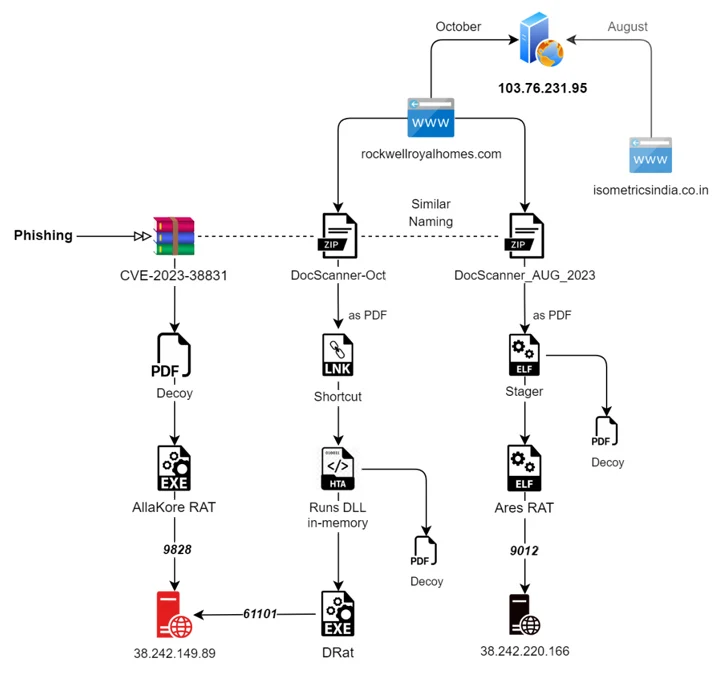
Two different attack chains. (Source – The Hacker News)
The deployment of RATs is not new; there have been notable instances in the past, such as the infamous Back Orifice rootkit. This well-known RAT was developed by the hacker group Cult of the Dead Cow (cDc) to expose the security vulnerabilities in Microsoft’s Windows 9X operating systems. The name “Back Orifice” cleverly mimics Microsoft’s BackOffice Server software, highlighting its capability to control multiple systems simultaneously.
Back Orifice is a software tool designed for administering systems remotely. It enables remote control of a computer. The software was first introduced at DEF CON 6 on August 1, 1998, and was developed by Sir Dystic of the cDc group.
Despite its intended legitimate uses, Back Orifice is often utilized for nefarious purposes due to its robust features. It was quickly labeled as malware by the antivirus industry and added to its lists of quarantined software. There are two known successors to Back Orifice: Back Orifice 2000, released in 1999, and Deep Back Orifice, created by the French Canadian hacker group QHA.
How to identify a RAT?
Identifying a RAT infection can be challenging. By nature, RATs are designed to be stealthy, often using random file names or paths to evade detection and hide their presence on a system.
Typically, a RAT virus is not visible in the list of active programs or tasks, and its behavior can mimic that of legitimate software. Furthermore, RAT spyware is designed to use computer resources to avoid triggering performance-related warnings efficiently. Hackers using RATs often avoid overt actions like deleting files or moving the cursor, which could alert the user to their presence.
The recent cyberattacks on Indian government institutions highlight the evolving landscape of cybersecurity threats, particularly from groups like SideCopy. This organization’s sophisticated use of RATs underscores the increasing complexity and adaptability of cyberthreats, extending beyond traditional Windows environments to target Linux systems, reflecting a strategic shift in response to global technological trends.
As cyberthreats evolve, understanding and anticipating the strategies of groups like SideCopy becomes crucial for safeguarding sensitive information and national security interests.
READ MORE
- Safer Automation: How Sophic and Firmus Succeeded in Malaysia with MDEC’s Support
- Privilege granted, not gained: Intelligent authorization for enhanced infrastructure productivity
- Low-Code produces the Proof-of-Possibilities
- New Wearables Enable Staff to Work Faster and Safer
- Experts weigh in on Oracle’s departure from adland




