
MongoDB database hit by cyberattack exposing customer data (Source – Shutterstock).
The database provider MongoDB security breach exposes customer contact information
- MongoDB database breach exposes customer data – Atlas service remains secure.
- MongoDB responds to security breach, acknowledges customer data accessed.
- MongoDB incident highlights tech industry’s cybersecurity challenges.
MongoDB, a database software company, recently issued a warning about a breach in its corporate systems, leading to the exposure of customer data. This cybersecurity incident marks a significant event for the company, known for its extensive reach in the database software market and its substantial revenue of US$1.2 billion this year.
MongoDB database breach: unveiling the incident
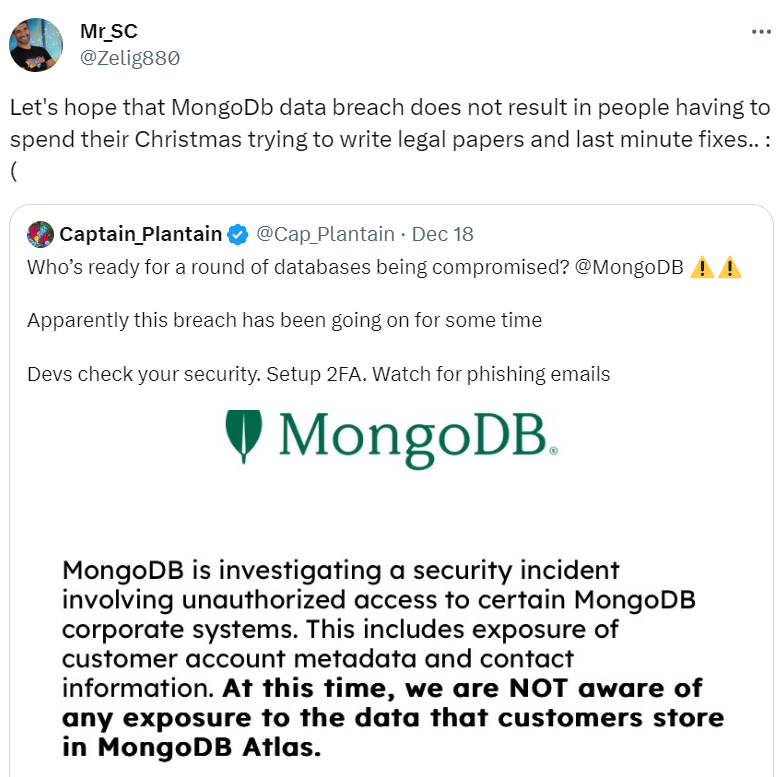
The breach was first detected on the evening of December 13, 2023 (US Eastern Standard Time), when MongoDB identified suspicious activity within its corporate systems. The company promptly initiated its incident response process. However, it is believed that the unauthorized access had been ongoing for some time before its discovery.
In a notice posted on December 16 on its alert page, MongoDB confirmed the security incident involved unauthorized access, resulting in the exposure of customer account metadata and contact information. Despite this, MongoDB assured customers there was no evidence of exposure to the data stored in MongoDB Atlas, its flagship database service.
As a precaution, MongoDB recommends customers remain alert to potential social engineering and phishing attacks. The company advises activating phishing-resistant multi-factor authentication (MFA) and the regular rotation of MongoDB Atlas passwords. MongoDB emphasizes that it has not found any security vulnerabilities in its products as a result of this incident.
Importantly, MongoDB says that access to MongoDB Atlas clusters is authenticated through a system separate from the compromised corporate systems. As of December 17, no evidence suggests any unauthorized access to MongoDB Atlas clusters or compromise of the Atlas cluster authentication system.
The breach resulted in unauthorized access to some corporate systems containing customer names, phone numbers, email addresses, and other account metadata. Notably, system logs for one customer were accessed, and MongoDB has notified the affected customer. There is no indication that other customers’ system logs have been accessed.
MongoDB database vulnerability leads to customer data leak. (Source – X).
Past incidents
The database provider company has faced multiple cybersecurity incidents, not just this recent one. In July 2020, a significant event unfolded when a hacker placed ransom notes on 22,900 MongoDB databases that were exposed online without password protection. At the time it was claimed that this figure represented nearly half (47%) of all misconfigured self-hosted MongoDB databases that had been left accessible online.
In this incident, the hacker employed an automated script to identify and exploit misconfigured MongoDB databases. The script erased the database contents and replaced them with a ransom note demanding 0.015 bitcoin (approximately US$140).
The cybercriminal set a tight deadline, giving companies two days to comply with the payment demands. Failure to pay would result in the leaking of their data and a report to the victim’s local General Data Protection Regulation (GDPR) enforcement authority, exposing them to potential legal issues.
These specific ransomware attacks, identified by the ransom note titled “READ_ME_TO_RECOVER_YOUR_DATA,” were first detected in April 2020. The attacker repeatedly accessed the same databases, leaving multiple copies of the ransom note over several days.
Such MongoDB wiping and ransom attacks are not a recent phenomenon. These incidents are part of a larger trend that began in December 2016. At that time, hackers discovered they could profit significantly by erasing MongoDB servers and demanding ransoms, exploiting the desperation of server owners to recover their data.
In a series of attacks, over 28,000 servers were held for ransom in January 2017, followed by another 26,000 in September 2017, and 3,000 more in February 2019.
This specific MongoDB incident occurred during a year marked by several high-profile data breaches. For example, in November 2020, Samsung reported a significant breach spanning a year, from July 1, 2019, to June 30, 2020. This breach resulted in unauthorized access to customer data from its UK store, but it wasn’t discovered until November 13.
Samsung assured that no financial data or customer passwords were compromised, though contact information was accessed. In response, the company reported the breach to the Information Commissioner’s Office and notified the affected customers, taking steps to resolve the situation.
Ongoing investigation and updates
MongoDB continues to investigate the breach and will provide updates on the MongoDB Alerts web page, which is used for communicating about outages and other incidents. The company remains committed to transparency and the security of its systems and customer data.
This incident serves as a reminder of the ever-present cyberthreats facing technology companies. It underscores the importance of robust security measures and constant vigilance in an increasingly interconnected digital world. Customers of MongoDB and similar services are urged to follow the recommended security practices and stay informed about the latest updates regarding this breach.
READ MORE
- Safer Automation: How Sophic and Firmus Succeeded in Malaysia with MDEC’s Support
- Privilege granted, not gained: Intelligent authorization for enhanced infrastructure productivity
- Low-Code produces the Proof-of-Possibilities
- New Wearables Enable Staff to Work Faster and Safer
- Experts weigh in on Oracle’s departure from adland




