North Korea’s US$3 billion crypto theft (Generated with AI)
Cyber-heist mastery: how North Korea stole over US$3 billion in cryptocurrency
- Since 2017, North Korea’s cyber-heist operations have netted over US$3 billion in cryptocurrency.
- North Korea’s crypto market attacks aim to support its economy under sanctions.
- North Korea’s hackers mastering crypto-theft pose a growing global security threat.
Since 2017, North Korea has dramatically escalated its focus on the cryptocurrency industry, pilfering over US$3 billion in digital currency. This shift came after their successful breaches of financial institutions through the SWIFT network attracted intense scrutiny from global authorities, leading to strengthened cyberdefenses in the financial sector. As the cryptocurrency market surged in 2017, North Korean hackers pivoted to this burgeoning sector, initially targeting South Korean markets before expanding globally.
In 2022 alone, North Korean cyber-actors are believed to have stolen around US$1.7 billion in cryptocurrencies, a staggering sum representing about 5% of North Korea’s GDP or 45% of its military expenditure. This figure is nearly tenfold the value of North Korea’s exports in 2021, as per the Observatory of Economic Complexity.
Decoding North Korea’s cyber-heist strategies
The methods North Korean cybercriminals employ in targeting cryptocurrency and laundering the proceeds are similar to those of typical cybercrime groups, involving cryptocurrency mixers and fiat conversions. However, state backing significantly amplifies the scale and effectiveness of their operations, with about 44% of the stolen cryptocurrency in 2022 traced back to these actors.
Insikt Group’s latest report, Crypto Country: North Korea’s Targeting of Cryptocurrency, highlights the steady increase in cyberattacks against the cryptocurrency industry since 2017, attributed to North Korean hackers.
Despite North Korea’s notable isolation, often called the “Hermit Kingdom,” its elite and specialized computer scientists have privileged access to cutting-edge resources, technologies, and information. This access not only equips them with the necessary skills for sophisticated cyberattacks on the cryptocurrency industry but has also led to significant breaches, as evidenced by the incident with JumpCloud. On July 12, 2023, this American software company announced a breach by a North Korean state-sponsored entity, later linked by Mandiant to UNC4899 or “TraderTraitor,” a group known for targeting cryptocurrency.
The US Federal Bureau of Investigation (FBI) disclosed on August 22, 2023, that North Korean operatives were behind major thefts involving Atomic Wallet, Alphapo, and CoinsPaid, resulting in a loss of US$197 million in cryptocurrencies. These thefts have been pivotal in sustaining the North Korean regime, particularly in financing up to half of its ballistic missile program.
By 2018, North Korea was estimated to be responsible for around 50% of the total cryptocurrency stolen worldwide. In recent years, attention has been focused on the regime’s substantial cryptocurrency heists, a continuation of its long history of funding through illicit activities.
The dark art of laundering stolen crypto
The laundering of stolen cryptocurrency involves several steps. Initially, the funds enter the financial system, a stage known as “placement.” The money is then “layered” through various transactions to obfuscate its origins. Finally, during the “integration” phase, the funds reappear in the legitimate financial system.
North Korean hackers, much like independent cybercriminals, use cryptocurrency mixers to hide their illicitly obtained funds. They also exchange stolen cryptocurrency for clean assets through legitimate trading platforms.
In 2021, the Insikt Group reported tutorials for basic money laundering techniques on forums like Nulled Forum. Both state-backed and independent criminals often employ money mules, sometimes unwittingly, in these operations.
The targets of North Korean cyberattacks are diverse, ranging from individual users to venture capital firms and emerging technologies. This widespread targeting endangers anyone in the cryptocurrency industry and lets the North Korean regime maintain operations under international sanctions.
The regime heavily relies on cryptocurrency theft as a revenue source, particularly for its military and weapons programs. Although the direct contribution of stolen funds to missile launches is uncertain, there has been a notable increase in cryptocurrency thefts and missile launches in recent years.
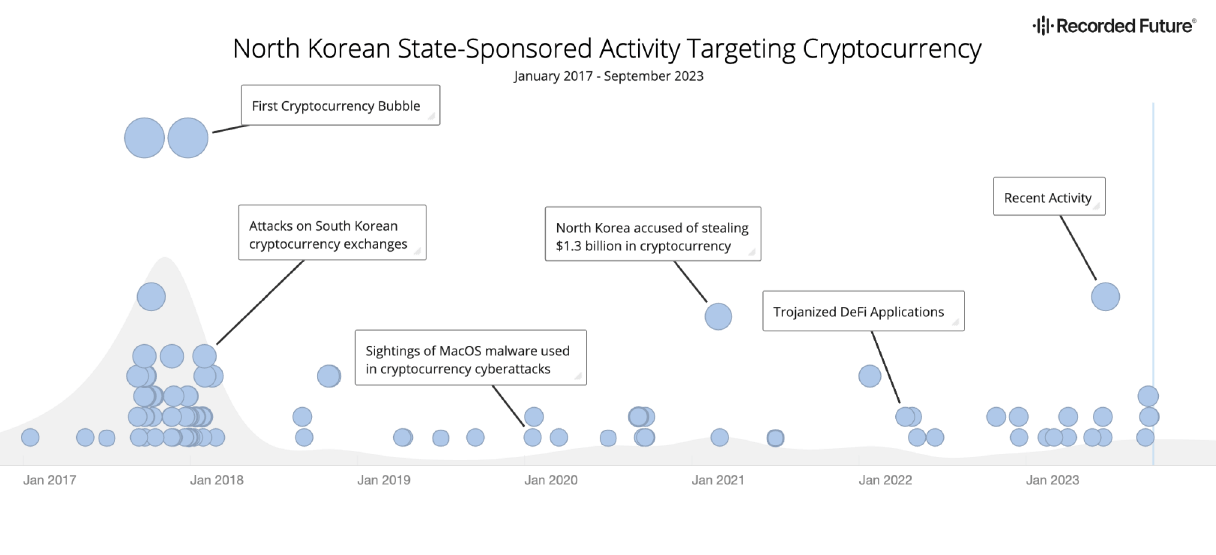
North Korean state-sponsored activity targeting the cryptocurrency industry (Source: Recorded Future Intelligence
Cloud).
North Korea’s illicit financial networks
Without stricter regulations and enhanced cybersecurity measures for cryptocurrency firms, North Korea will likely continue targeting this sector for revenue.
North Korea’s history of illicit activities has led to the developing of sophisticated asset-laundering networks and methods. In 2020, leaked documents from the US Financial Crimes Enforcement Network revealed significant laundering activities supporting the regime. These operations often involve individuals linked to North Korea’s Reconnaissance General Bureau (RGB).
One particularly detailed instance of such operations was the 2016 Bangladesh Bank heist. North Korean hackers transferred the stolen funds to four accounts in the Philippines, converting US$61 million into pesos for use at the Solaire Resort casino.

North Korea-linked hacker organization Lazarus Group has stolen US$3 billion in cryptocurrency. (Source – X).
The US State Department in 2017 identified the Philippines as a central hub for money laundering. In the Bangladesh Bank case, the stolen funds were used for gambling at the casino, making the proceeds untraceable. The primary gamblers, Ding and Gao, escaped to Macau after their operation. Macau’s history includes various North Korean activities, such as being the training ground for the spy responsible for the 1987 Korean Air flight bombing, a center for laundering counterfeit US currency, and the residence of Kim Jong Un’s exiled half-brother before his assassination in 2017.
North Korea’s cyber-heist fallout
Reflecting on North Korea’s significant advancements in cybercriminal operations against the cryptocurrency industry, it is crucial to assess the broader impact on the country. Estimates suggest that up to 50% of North Korea’s ballistic missile program could be financed through these illicit gains.
In the context of its economy, which was roughly US$33.5 billion in GDP in 2019 and has faced contraction for three consecutive years, according to the Bank of Korea, the scale of these operations becomes even more apparent. In 2022, the value of stolen cryptocurrency by North Korean actors was about 5% of the nation’s economy, not accounting for other illicit activities or illegal employment in the IT sector.
North Korea’s aggressive foray into cryptocurrency theft since 2017 highlights a sophisticated and evolving cyber warfare strategy. This situation calls for a concerted international response, including stringent cybersecurity measures and regulatory frameworks, to mitigate the risks of such state-sponsored cybercriminal activities. Without these, North Korea will likely continue to exploit the vulnerabilities of the cryptocurrency sector, posing a persistent and evolving threat to global financial security.
READ MORE
- Safer Automation: How Sophic and Firmus Succeeded in Malaysia with MDEC’s Support
- Privilege granted, not gained: Intelligent authorization for enhanced infrastructure productivity
- Low-Code produces the Proof-of-Possibilities
- New Wearables Enable Staff to Work Faster and Safer
- Experts weigh in on Oracle’s departure from adland