
The ripple effects of Ubisoft’s recent cyberattack. (Source – Shutterstock)
Ubisoft faces the challenge of a recent cyberattack
- Ubisoft faced a recent cyberattack, leading to leaked internal system screenshots and security concerns.
- Ubisoft’s latest cyberbreach adds to its history of digital security struggles.
- Ubisoft unexpectedly revives servers for several games, temporarily enabling discontinued achievements.
Ubisoft, the French video game company celebrated for its array of popular titles such as Assassin’s Creed, FarCry, Tom Clancy’s Rainbow Six Siege, and the newly launched Avatar: Frontiers of Pandora, has recently found itself grappling with a cybersecurity dilemma.
There are reports that Ubisoft is investigating a cybersecurity breach involving an anonymous hacker who reportedly infiltrated key company channels like Microsoft Teams, Confluence, Atlas, and SharePoint. The intruder is said to have had access for 48 hours before being ousted from the system.
Investigating the recent cyberattack hitting Ubisoft
The gaming community, particularly the Gaming Leaks and Rumours subreddit, and a Bleeping Computer report, highlight that screenshots supposedly captured during the cyberattack on December 20th have been leaked online. Ubisoft has acknowledged this incident and is looking into this supposed data security breach.
Ubisoft’s official statement was concise: “We are aware of an alleged data security incident and are currently investigating. We don’t have more to share at this time.”
Vx-underground, via a tweet, shared information from an undisclosed source claiming responsibility for the breach on December 20th. This individual alleged their intention was to extract roughly 900GB of data after gaining entry to Ubisoft’s internal systems, including the SharePoint server, Microsoft Teams, Confluence, and MongoDB Atlas panel. They also purportedly provided screenshots showing access to some of these platforms.
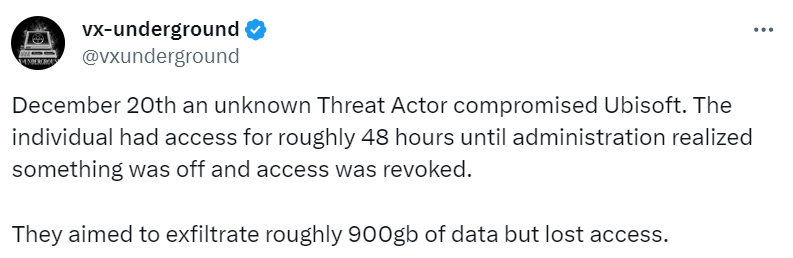
Vx-underground reports that an unidentified aggressor claimed to have infiltrated Ubisoft on December 20th. (Source – X).
In a separate but possibly related development, MongoDB Atlas reported a breach. However, there seems to be no direct connection between that incident and the one at Ubisoft.
In communication with vx-underground, the perpetrators revealed their failed attempt to steal data from Rainbow 6 Siege users. They were detected and subsequently lost access before they could complete their intended data theft.
Ubisoft is no stranger to cyberattacks. In 2020, the company fell victim to the Egregor ransomware gang, leaking portions of the Ubisoft game Watch Dogs‘ source code. Another breach occurred in 2022, disrupting the company’s games, systems, and services.
The Lapsus$ connection: past and present intrusions
In these previous instances, the cybercriminal groups responsible for the attacks were either known or strongly suspected. For instance, the 2022 breach was widely attributed to the Lapsus$ group.
Ubisoft has reported a temporary disruption to some of its games, systems, and services in light of the most recent incident. The company’s IT teams are currently probing the issue in collaboration with external experts. As a precautionary measure, Ubisoft initiated a reset of passwords across the company. The company also ensured that all games and services were functioning normally, and at the time of publishing, there was no indication that any players’ personal information had been compromised or exposed in the incident.
Lapsus$, a hacking group based in South America, indirectly hinted at its involvement in the recent cyberattack at Ubisoft on Telegram, accompanied by a smirking face emoji. However, it did not directly claim responsibility. The group later added in the same thread that its target was not Ubisoft as such, but the customer data it could harvest from the attack.
Previously, Lapsus$ made headlines for claiming responsibility for leaking Nvidia employee password hashes, leading to outages in Nvidia’s developer tools and email systems. The group even threatened to release confidential files related to Nvidia’s GPUs unless its demands for open sourcing the GPU drivers were met. It also confessed to breaching Samsung’s systems and leaking almost 200 GB of internal files online. Furthermore, Lapsus$ broadcasted on Telegram its intent to recruit insiders at potential targets, explicitly targeting significant software and gaming corporations.
Ubisoft’s server revival and future closures
In an unrelated turn of events, Ubisoft gamers were surprised to find that servers for games like Driver: San Francisco, Splinter Cell: Blacklist, Rayman Legends, and Assassin’s Creed III, which were officially shut down in October 2022, have mysteriously come back online. This unexpected development has allowed players to earn various online achievements previously considered discontinued.
TrueAchievements community members have noted that the servers for Driver: San Francisco and Splinter Cell: Blacklist are operational again. Additionally, there are reports that servers for Assassin’s Creed III and Rayman Legends on Xbox 360 are also back. Players can now unlock achievements linked to these games’ online features.
However, it is speculated that this server reactivation is an unintentional outcome from Ubisoft, and it’s likely that the servers will go offline again shortly. Gamers hoping to obtain achievements from these games are encouraged to seize this opportunity swiftly.
Looking ahead, next month is set to see the closure of servers for four Xbox games, including WWE 2K22, signaling the end of an era for these titles.
READ MORE
- Safer Automation: How Sophic and Firmus Succeeded in Malaysia with MDEC’s Support
- Privilege granted, not gained: Intelligent authorization for enhanced infrastructure productivity
- Low-Code produces the Proof-of-Possibilities
- New Wearables Enable Staff to Work Faster and Safer
- Experts weigh in on Oracle’s departure from adland




