
The WPA2 protocol could pose a serious risk for users due to MtM attacks. Source: Shutterstock
A closer look at the WPA2 KRACK flaw explains why MtM attacks pose huge risk
RECENTLY, it was brought to light that millions of WiFi connected devices are at risk due to an inherent flaw in the WPA2 protocol. The vulnerability was recognized officially by the United States Homeland Security’s cyber-emergency unit, US-Cert, and more recently, the Singapore Computer Emergency Response Team.
The recently discovered WPA2 flaw gave rise to an exploit dubbed as KRACK, which exposes the vulnerabilities of WiFi connections. So far, billions of devices worldwide are at risk, with 11 million of these being found in Singapore, as noted in a report from The Straits Times.
Due to the cybersecurity flaw originating in a WiFi system’s standard protocol itself, it has been particularly difficult to pinpoint an effective solution against the KRACK vulnerability. Firms such as Microsoft and Apple have addressed this problem through the roll-out of dedicated software updates. Other premier tech companies such as Google are expected to follow suit.
According to Netmetix Managing Director Paul Blore, enterprises with an online presence face a bigger risk from the WPA2 flaw than consumers. In a statement to Tech Wire Asia, Blore stated that while the vulnerability could result in hackers being able to effectively decrypt standard WiFi encryption, the KRACK flaw in itself does not present a significant risk to users.

WiFi may hold unseen vulnerabilities for millions. Source: Shutterstock
The Netmetix MD also assured TWA that secure websites such a banking and online retail stores usually utilize an additional layer of encryption in their operations. Thus, while the WPA2 flaw exists, the added contingencies in these systems make them rather unaffected by the recently exposed WiFi vulnerability.
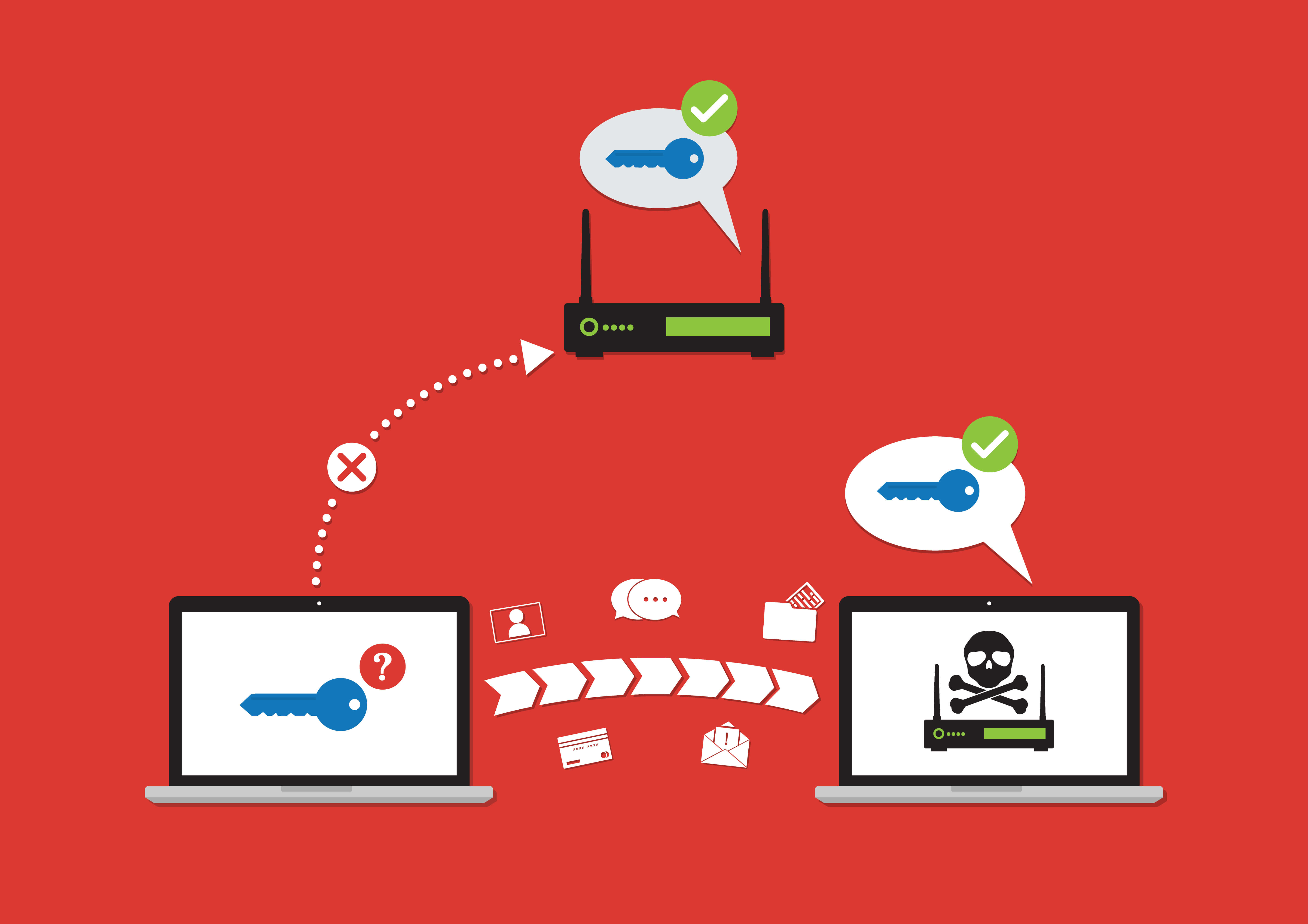
According to Blore, what really presents a huge danger to businesses and users alike are Man-in-the-Middle (MtM) attacks. MtM attacks happen when hackers, positioned in the vicinity of a compromised network, masquerade as legitimate access points. This practice enables hackers to eavesdrop on unsecured connections – the online equivalent of a drive-by attack.
“MtM attacks, whilst not generally directly aimed at businesses, are used to compromise credentials and thereby gain access to vital information from the unsuspecting user (victim). This, for example, could be used to capture company credit card information or network access credentials, which will affect the business.
“Many threats move laterally, so a piece of information is often gained by the hacker, then used in a different form. This compromised user could be an administrator for a company intranet system which would then be infiltrated,” said Blore in a statement to Tech Wire Asia.
“Likewise, personal information from this user could be used to gain access to their own online banking system.”
Source: Shutterstock
The Netmetix MD also took a particular interest in small businesses, many of whom are utilizing devices that are vulnerable to the recently discovered WPA2 flaw. According to Blore, businesses should start looking at IT and cybersecurity as a tactical overhead instead of a strategic decision. The executive further explained the importance of cybersecurity safeguards to small businesses.
“SMEs in particular, can often feel they are too (many) smaller fish to fry for hackers to target but fundamentally, if data is valuable to a business, then it’s going to be valuable to the hackers,” he said in a statement to TWA.
With billions of devices being vulnerable to attack, the Netmetix MD Blore provided five useful and practical tips that enterprises could employ to decrease the chances of their devices being compromised by the KRACK flaw, or MtM attacks for that matter.
- Where possible, use a wired connection to mitigate this attack completely.
- Educate users to the importance of HTTPS connection and how to spot fraudulent activity.
- Patch client devices to the latest firmware update that resolves the issue.
- Patch Wireless Access Points (WAP’s) to latest firmware update (Many vendors have not yet patched against this threat).
- Ensure all ant-virus/threat protection software is fully up to date, which could stop any hijack attempts if the WiFi security was compromised.
Overall, Blore asserted in his email interview with TWA that there is really no single way to make a business’ online presence fully safe. Rather, it is the utilization of multiple contingencies that can truly make a difference between safety and vulnerability.
“System security has to be approached in a blended or multi-layered format; there is no single, cost-effective solution that will ensure total protection. By implementing defense in depth with multiple layer security, you stand the best chance of protecting yourself,” Blore said.
READ MORE
- Strategies for Democratizing GenAI
- The criticality of endpoint management in cybersecurity and operations
- Ethical AI: The renewed importance of safeguarding data and customer privacy in Generative AI applications
- How Japan balances AI-driven opportunities with cybersecurity needs
- Deploying SASE: Benchmarking your approach






