
Asia Pacific needs to get serious about fixing its cybersecurity issues. Source: Shutterstock
Weak business and technology security could cripple Asia Pacific
ASIA PACIFIC has been named as the worst region to be in for cyberattacks due to a largely outdated legacy systems in place in most corporations, as well as poor computing habits among its Internet users, said a cybersecurity firm.
The region has become a hotbed for cybercriminal activity, said cybersecurity solutions firm Trend Micro, at an event in Manila. The director of Trendlabs research at Trend Micro, Myla Pilao, said that the Asia Pacific alone accounted for 35.7 percent of all malware detections globally, and as such is in pole position for system vulnerability. In second position is Europe, the Middle East and Africa (also known as the EMEA region) which collectively make up 25.24 percent; Latin America makes up 22.66 percent of all detections, while North America accounts for only 15.71 percent.
Pilao indicated that the main targets of these attacks are banks and healthcare enterprises. In banking, Trend Micro said that there were 118,193 pieces of malware detected and blocked, and the majority of these threats take place during online payment processes.
According to the company’s “2017 Midyear Security Roundup: The Cost of Compromise” report, which was showcased at the event, though 2017 was characterized by huge cybersecurity scandals, ranging from the far-reaching impacts of the WannaCry and NotPetya events, the biggest contributor to system vulnerability remains in the hands of enterprises themselves who have not yet moved to upgrade their systems and security.
Source: Trend Micro
“To be sure, some companies may have any number of reasons — ranging from financial considerations to implementation challenges — for leaving vulnerabilities unpatched, highly sensitive data unencrypted, or critical personnel uninitiated in the intricacies of social engineering,” the report said.
“But these are compromises that lead to structural weaknesses, ones that threat actors are only too ready and willing to exploit. The consequences of enterprises’ failure to secure their systems are far-reaching.
“As security risks continue to evolve and expand to encompass threats as novel as industrial robots gone haywire and as unpredictable as cyberpropaganda campaigns, the necessity of proper and effective cybersecurity, especially among enterprises, cannot be overstated.”
Enterprises compromise, vulnerabilites spread
Old system vulnerabilities that were just never addressed effectively by corporations has led to increased vulnerabilities in enterprises, especially those with particularly outdated legacy systems. Trend Micro said that they found 382 new vulnerabilities in the first half of 2017, with huge numbers coming from some of the biggest brands out there: Apple, Google, and Microsoft. The most notorious vulnerabilities could be traced back to unpatched Microsoft products which were exploited by the EternalBlue WannaCry ransomware, which caused havoc around the world back in May this year.
Trend Micro said that while enterprises can be forgiven some vulnerabilities due to the complexities of patch management, “securing systems from vulnerabilities is necessary.”

Business email is a frequent culprit when it comes to systems security. Source: Shutterstock
“Cybercriminals take advantage of unpatched and otherwise vulnerable systems to drop their payloads. Leaving systems unprotected can result in network intrusions, opening the door to further attacks like data breaches and ransomware infections,” the report said.
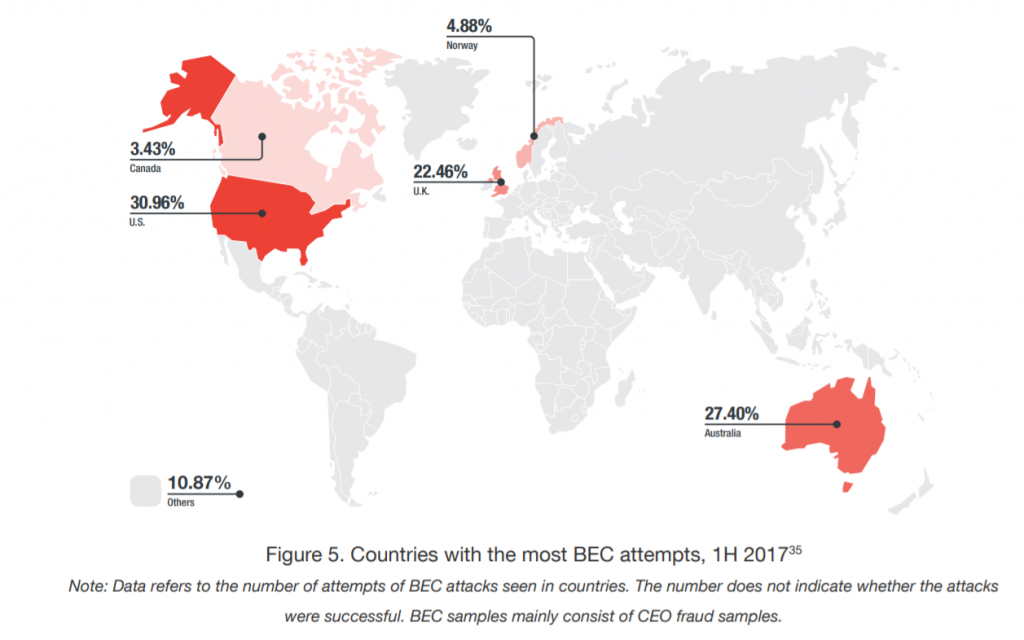
Perhaps where security systems really slipped up this year was in the category of business emails. Trend Micro reported the US Federal Bureau of Investigation (FBI) numbers indicated that business email scams have cost the world as much as US$5.3 billion in the four years since 2013.
The emails of C-suite executives are frequently targeted, but what was really interesting is cybercriminals’ reliance on old phishing and hacking techniques. For instance, a recurring technique is the use of the “supplier swindler scheme” wherein criminals pretend to be an ancillary business engaging with their target – malware is then attached to email communication.
The widespread of such hacking techniques makes it more important than ever for enterprises to really hone in plugging the gaps in their email infrastructure, which really makes up the basis for the majority of sensitive in-house communication. Trend Micro advised programs that would train personnel in key departments – such as finance or human resources – in techniques for spotting business email scams.
Threat of the Internet of Things (IoT)
As our society adopts more connected devices, the increased interactivity between the web and everyday objects could pose a significant threat to our information safety. Trend Micro’s report noted that in April, they had detected the Persirai botnet that had been targeting Internet of Things (IoT) connected cameras; as many as 120,000 Internet Protocol (IP) cameras have been exposed to the malware.
Cameras merely make up one part of the entire IoT ecosystem; today, we live in an ecosystem where everything from the temperature in our homes, to the music playing via wireless speakers. The interconnectivity of all these devices, which are constantly exchanging information and tapping into our sensitive data, could be a prime target for identity thefts and hackers.

Pepper and NAO are among the robots that have serious vulnerabilities that can be exploited by hackers. Source: AP
Trend Micro said that a previous report found that as many as 83,000 industrial routers and 28 exposed industrial robots were exposed and vulnerable through various search engines. The easy access of these internal systems could make being around industrial robots extremely dangerous as hackers can access them remotely. This was also clearly exemplified by a research project undertaken by IOActive who found that Softbank’s popular Pepper robots could be hacked and controlled via an unsecured vulnerability.
The issue becomes increasingly alarming when you consider the fact that the International Federation of Robots forecasted as many as 1.3 million industrial robots in factories by 2018. Billions of dollars will be poured into various industries over time to boost automation in these industries, but those efforts could be undermined if hackers are able to compromise these systems and make them unsafe or damaged.
“These attacks can lead to unusable or unsafe products, which in turn can result in the factories having to recall their products and pay for damages,” the report said.
“In order to keep industrial robots secure, operators, robot vendors, software developers, network defenders, and cybersecurity standards makers should make attacks on industrial robots expensive to the point of being impractical.
“Physical safety protocols and solutions to mitigate vulnerabilities must also be in place. For their part, program designers must enforce stringent software engineering practices to improve code robustness, harden underlying platforms, and implement strong authentication measures.”
READ MORE
- Strategies for Democratizing GenAI
- The criticality of endpoint management in cybersecurity and operations
- Ethical AI: The renewed importance of safeguarding data and customer privacy in Generative AI applications
- How Japan balances AI-driven opportunities with cybersecurity needs
- Deploying SASE: Benchmarking your approach








