Unprotected legacy systems are especially susceptible to attacks. Source: Shutterstock
Antique cyberattacks target unpatched legacy systems
THE IMPORTANCE of keeping all computers up-to-date with security patches was made apparent earlier this week after a series of Chinese websites were identified as being the targets for drive-by download campaigns which dropped a distributed denial of service (DDoS) bot called Avzhan, a malware which is around eight years old.
Malwarebytes Labs researchers pointed out that the exploits were not advanced.
The very existence of such campaigns these days points to the fact that there have to be enough genuine targets susceptible to such attacks remaining, despite the best efforts of cybersecurity teams across the globe.
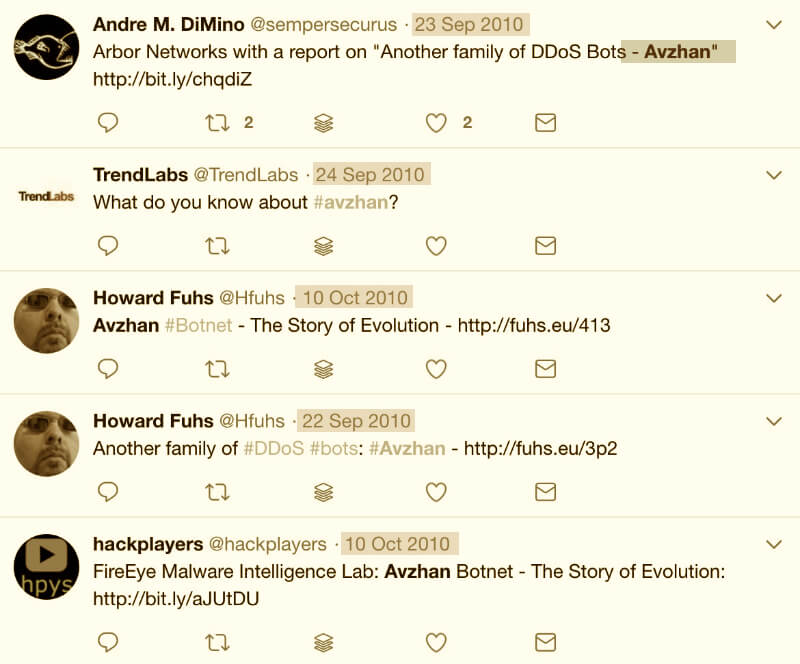
Tweets going back to 2010 reflect the malware’s age. Source: Twitter
The exploits include three which target specific vulnerabilities in Flash player, Internet Explorer and ActiveX, the latter affecting the C6 Messenger control. In this instance, the creator of the exploit used old code, simply changing the download URL to point to their own URL.
The Flash vulnerability dates from 2015 and the Internet Explorer exploit from 2016. Flash is not often seen on up-to-date websites and the platform is on the decline, partially at least as a result of Apple’s refusal to integrate compatibility the Macromedia-created system into iOS.
All the vulnerabilities as identified by Malwarebytes Labs drop the Avzhan DDoS bot which installs itself onto targeted machines as a Windows service. Researchers say that while Avzhan has been around for several years, its presentation has changed little over time, with better attempts to hide the code and configuration additions to the original.
Malwarebytes Labs researcher Jérôme Segura said:
Although we see the use of several exploits, we cannot call this an exploit kit – not even an amateur one. Indeed, the domain serving the exploits appears to be static and the URIs are always the same. Regardless, it does not prevent threat actors from arranging drive-by attacks by copying and pasting various pieces of code they can find here and there. While not very effective, they may still be able to compromise some legacy systems or machines that have not been patched.
READ MORE
- Strategies for Democratizing GenAI
- The criticality of endpoint management in cybersecurity and operations
- Ethical AI: The renewed importance of safeguarding data and customer privacy in Generative AI applications
- How Japan balances AI-driven opportunities with cybersecurity needs
- Deploying SASE: Benchmarking your approach