
Cybersecurity intelligence: Not as simple as gather and react
BIG data has become an empowering force for organizations both large and small. Big data has the potential to drive commercial interests when used internally as a proprietary source of information, and to change people’s lives and society for the better when made publicly available.
Threat intelligence in cybersecurity is a manifestation of big data, but its use is complicated by the volume and variety of data.
“86 percent of companies surveyed in the US and UK stated that threat intelligence
was “valuable to our security mission.”
– Ponemon Institute, September 2017
Any data for security analysis needs to undergo several specific processes before it can be operationalized, including normalizing data and removing false positives.
Normalizing data involves the deduplication of data and reconciliation of disparate formats such as .csv, JSON, PDFs, emails, and more. This disparity in formats is tied directly to the abundance of threat intelligence sources, which can include open source, commercial, and dedicated information sharing groups.
Removal of false positives is a more complicated process. False positives are data that are initially flagged as malicious but in reality, are benign.
This can occur frequently as additional data sources are incorporated into an organization’s security infrastructure and require a significant amount of analysts’ time and resources to identify.

Machine learning algorithms help to remediate this issue by applying complex mathematical analysis to determine the veracity of any malicious or benign verdicts.
Business software vendors are fond of showcasing their products’ ability to produce “real-time” data. What this actually means is the information is presented quickly enough to make no difference to end-users.
However, for CISOs, real-time information really does need to be real-time. This usually means that significant resources need to be deployed to process the mass of big data which today forms threat intelligence data.
Once normalized and curated, threat data can then be integrated with a variety of security solutions such as next-generation firewalls, web application firewalls, intrusion detection systems, endpoint protection systems, and network traffic examination systems (such as distributed data center micro-segmentation systems).
Despite the resources and effort required to operationalize threat intelligence data, organizations will still frequently invest in threat intelligence to protect their brand and customers.
A recent survey by the Ponemon Institute has shown that enterprises increasingly value threat intelligence. Of the 628 individuals surveyed in the US and UK, 86 percent stated threat intelligence was “valuable to [their] security mission,” up from 77 percent the previous year.
Similar numbers valued threat intelligence as “essential to a strong security posture.” Over half of the respondents also said they actively used threat intelligence (63 percent) and said it is a key factor in driving security operation center (SOC) decisions.
However, only 27 percent gave their organizations high marks for effectively using threat intelligence. What then, are the barriers and pain points for the average enterprise chief security officer which have created such a low opinion of performance?
One of the main reasons for slow adoption appears to be a lack of expertise in the use of threat intelligence. But that’s not always rectifiable with training, or by employing a significant number of specialists. Instead, threat intelligence is considered to be too voluminous and complex to be actionable.
One company offering a range of solutions to aid and manage threat intelligence processing and activity is Anomali.
The California-headquartered company offers various free data source feeds via its STAXX product. Any STIX/TAXII feed can be used, and the Anomali team also curates its own collection of feeds in the form of its Limo service.
Paid-for tiers begin with ThreatStream®, which effectively aggregates a variety of threat intelligence data sources (premium, ISAC/ISAO, FOSS, etc.) and is capable of intelligently identifying potential actors, and/or campaigns, and adding TTP (tactics, techniques and procedures) data to any threat it unearths.
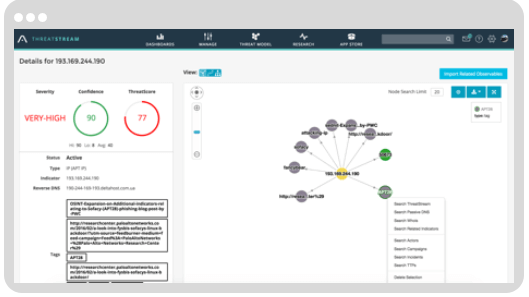
Anomali
ThreatStream® integrates with SIEM, firewalls, intrusion detection systems, endpoint protection systems and indeed, any system with a sensible API.
By consolidating information, rationalizing it and deploying it intelligently, security operation centers get viable information on which they can act — or have the data automatically instruct the rest of their security stack.
Anomali Enterprise™ adds to this set of tools by matching IOCs against unlimited volumes of logs and automatically creating alerts and feeding indicator matches to SIEMs and other systems.
Anomali users can extend their intelligence-gathering capabilities with Trusted Circles, allowing seamless participation between carefully-chosen companies keen to share data.
Find a representative in your area to learn how Anomali can bring positive results to your cybersecurity efforts, talk to a threat intelligence expert today.
READ MORE
- Strategies for Democratizing GenAI
- The criticality of endpoint management in cybersecurity and operations
- Ethical AI: The renewed importance of safeguarding data and customer privacy in Generative AI applications
- How Japan balances AI-driven opportunities with cybersecurity needs
- Deploying SASE: Benchmarking your approach
