
The immeasurable cost of data breach
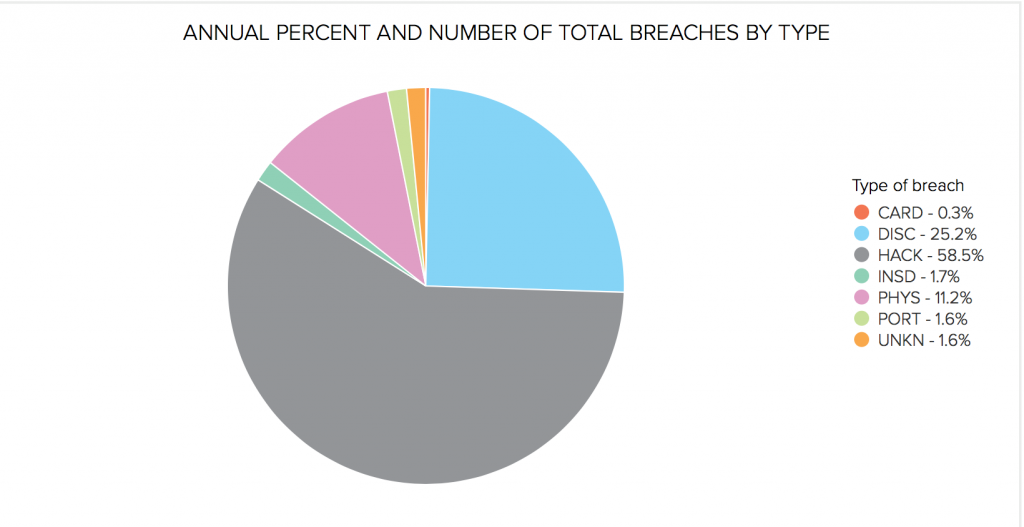
Because data is effectively the new currency of commerce, cybersecurity breaches which involve data exfiltration, or cyber attacks which prevent access to data for normal working, cost enterprises trillions of dollars each year – see the chart below, which shows 58.5 percent of data breaches in 2017 were down to hackers.
The veracity and variety of cybersecurity attacks have a range of effects, but the cumulative total can usually be added up in real dollar value, even though the purpose of the cyber attack might not necessarily be economic.
Think hacking, and most people have in mind a process by which person or persons unknown gain access to a private network, and locate files or resources which are removed for commercial gain. In this sense, the cybersecurity breach literally removes money from an organization. However, this type of attack is one of many.
Whatever the attack trajectory, companies will always have to spend time and resources on recovery, not least from the time lost when rolling back systems but also time for amelioration; often with legacy systems having to be patched or updated at times outside any planned schedules — usually, therefore, coming with a significant financial overhead.
In addition to direct monetary losses, today’s social media-oriented world will always very quickly disseminate bad news. The public relations losses, therefore, to a company can be significant. The traditional press still carries considerable weight, but Twitter-carried news spreads quickly, and years of market credibility can evaporate in hours.
Additionally, any data exfiltrated effectively becomes public property, and therefore open to being misconstrued. Any activities undertaken by an organization which can be misinterpreted almost definitely will be, usually to the detriment of the malware victim.
The result of all this is, of course, loss of customers, partners, and suppliers, each of which literally takes their business elsewhere.
In the aftermath of a data breach or incident, there may also be formal legal ramifications. Disgruntled customers or partners have the wherewithal to take action in the courts against organizations whose actions failed to prevent cyber security incidents.
Additionally, enterprises can suddenly figure largely on government radar. Necessary compliance with local, national, or transnational regulations is pretty much ubiquitous today. Divergence from governance stricture can bring down the wrath of massive legislatures on even the smallest organization.

What to do?
Under the last American administration, NIST’s publication of the Cybersecurity Framework (CSF) aimed to set out the steps organizations should take to protect themselves from cyber threats. Although the document was aimed at American governmental institutions, its underlying message can be applied right across any business, from start-up to multinational giant.
The document itself is long and complicated, and articles like this cannot hope to cover all the ground therein. Instead, there are a few choice take-homes which we at Tech Wire Asia feel would be immediately useful and actionable.
Identify
Undertaking risk assessments, or security audits, is clearly imperative. What will become apparent in organizations of any age is that there will almost definitely exist applications and systems which are security risks, yet (and this is the million-dollar issue) remain mission critical in the enterprise.
Application deployment may have taken place many years ago, on what are now considered to be legacy systems. However, plenty of processes and day-to-day work could hang off these systems. They may no longer be supported, run on old operating systems, be reliant on irreplaceable hardware, or insist on network protocols which are outmoded due to inherent security issues.

The EternalBlue exploit (behind WannaCry, Petya, and NotPetya, for instance) is one such. Relying on SMB v.1 (itself deprecated) being used on systems not patched for one reason or another, this ransomware devastated vast swathes of networks across the globe.
Protection
Access to and from controlled networks has always been protected by various types of gatekeeper. From early stateful firewalls up to today’s ML-driven (machine learning) packet inspection and intrusion detection/protection systems (IDS/IPS), examination of the flow of data is one way to protect a network.
However, as new technologies emerge, gateway-based protection systems are not sufficient as of themselves. Enterprise is pushing more of its applications and functions to the cloud, and so gateway firewalls need to be joined by critically-reliable web application firewalls (WAFs) – among other devices and techniques – which may or may not be under the control of the commissioning enterprise. A public cloud’s protection is effectively provided with a service, but isn’t configurable, in many instances.
Another critical security flaw can be found in organizations’ bring your own device policies (BYOD). By allowing workers and visitors access to company networks on their mobile devices, a whole new attack vector is opened up to malware.

It’s vital, therefore, to employ some kind of endpoint protection solution. Any solution needs to cover all devices joining the network from desk to datacenter, ranging from Linux-powered smartwatches to high-end laptops brought into the workplace and attached to local Wi-Fi networks.
Detect
IP protocols follow set guidelines. From the early days of Gopher, email and FTP, the way network services communicate and operate can comply – however loosely – with standards. Even proprietary systems communicate via well-documented means (albeit with some initial friction), and so anomalous network behavior can usually be pinpointed.
As new technologies come online, the cybersecurity community at large should be regarded as a source of updates for how new technologies communicate. Theoretically, therefore, from a single instance of an Android malware to a compromised Active Directory server, any network behavior out of the ordinary should be capturable.
Respond and recovery
Isolation of affected nodes within a network should be prioritized. This leaves security teams enough time to mitigate infected devices or routines.
The enterprise’s systems and routines, however, need to include isolation routines being practiced, as part of overall cyber protection: what actually physically happens in the case of a malicious event? Who does what? Where do autonomous systems step in, or when do they refer to their human bosses?

Mitigation measures – the next step – usually involve some kind of disaster recovery (DR) or roll-back. Similarly, DR procedures need to be practiced regularly. How quickly can a server be recovered? What about an entire VM blade rack?
Education
Keeping users up to speed with cybersecurity issues should not be unique to CISO’s departments. Every end user across the enterprise needs to be aware of the potential risks of their activities, not only to themselves but the employer.
Even the most battle-hardened cybersecurity professional will freely admit to, on occasion, reaching for the mouse to click a link in a suspect email (before realizing the error of their ways, of course).
In short, human beings are usually the weakest link in any organization, so primary cybersecurity hygiene practice needs to be taught right across the enterprise. For many, this activity is as important as any technologically-based security solution.
Here at Tech Wire Asia, we feel that Trend Micro is currently leading the way with its approach to cybersecurity issues.

One of the first to deploy patented machine-learning technologies in its cybersecurity solutions, the company has an enviable reputation in the marketplace for a range of defensive measures. Trend Micro (with 6,000+ employees in over 50 countries) is particularly noted for its rapid response to zero-day exploits, invoking defensive responses many hours if not days before new attack types become public knowledge.
The company’s Smart Protection Network™ is the descendent of its cloud-based defensive data gathering network launched back in 2008 – a revolutionary move ten years ago! Combined with the XGen™ Security technology that powers all its products, Trend Micro cyber-protection now covers over half a million businesses all over the world.
The statistics showing the scope of new dangers’ emergence is alarming – over a quarter of a million new & unique threats are identified daily by Trend Micro. Proactive blocking and predictive analysis of those new attack methods mean that businesses can continue to function, knowing that as dangers emerge, they are quickly dealt with by world-class experts.
Readers with a head for figures or an eye for an infographic will find this depiction informative, and security experts can learn more about what goes beyond next-gen IPS systems, or in this blog post. Alternatively, you can read more about Trend Micro’s security infrastructure provision here.
READ MORE
- Strategies for Democratizing GenAI
- The criticality of endpoint management in cybersecurity and operations
- Ethical AI: The renewed importance of safeguarding data and customer privacy in Generative AI applications
- How Japan balances AI-driven opportunities with cybersecurity needs
- Deploying SASE: Benchmarking your approach
