
Hope for the ‘p4ssword’-style password users: multi-factor authentication platforms
Most data breaches that take place in organizations across the world are caused by the activities of the people who work in them.
Rather than the stock photography image of a figure (invariably hooded) hunched over a laptop being the main threat to businesses, the image should be one of your average Joe (or Josephine) tapping in a password.
Why? Because it’s users that use the same, usually insecure password for multiple apps in and out of the workplace that cause the majority of problems.
Companies have realized that cybersecurity now needs to spread itself outside the workplace – in network terms, outside the firewall. Solutions ensure that users get access to all the services that they use in their working lives via a single set of log-in credentials, backed by secure two- (or multi-) factor authentication.
That’s important for several reasons. The first one is that there’s a blurring of the lines between home and work. People like to work at home on their personal laptop, and during their daily commutes on whatever device happens to be at hand, usually the smartphone. On the same platform that’s used to watch a movie or update social circles, there’s a way to access the most sensitive data their employer owns.
And since most companies use around a dozen services and apps to function, it’s little wonder that Josephine (or Joe) tends to use one password, for work apps, social media, streaming services, email, file sharing, and so forth.
Once a password is compromised on a platform (an example grasped from thin air might be a website for a dog-walking service) those credentials can quickly end up on the open market.

Hackers know that people tend to use the same password and/or email address for lots of different services. So, it’s probably worth trying the dog-walker’s account credentials with popular services, like Google Docs, Dropbox, Xero or QuickBooks. In that simple step, an organization’s entire intellectual property can be exposed, as can bank accounts, file shares, online services, social media accounts, and administrative backends to websites.
The unsurprising truth is that learning to hack one’s way around a firewall is difficult. But buying up a few thousand user credentials and testing them against a few services isn’t difficult, nor complicated. Arguably, companies are at threat from skilled groups working hard to circumvent the very latest in cyber protections, and they need to take steps to prevent this from happening, proactively. However, a more potent threat can be alleviated quickly and easily by instigating a more robust password policy for staff.
That’s all well and good, of course, but calls for everyone to use better and more unique passwords are hardly uncommon. And yet the situation remains. So what’s to be done, if your staff use the same log-in credentials for their off-duty canine activities as they do to unlock your company’s accounts packages?
The most effective way is to ensure that MFA or 2FA is in place: multi-factor authentication, or two-factor authentication, respectively. Under such a system, users enter their details as usual but then need to take additional steps. These can take several forms, ranging from a fingerprint check to a face print (using tech like that found on the iPhone X), via an SMS message, or use of an app on the user’s mobile.
While it’s difficult to generalize, MFA (or 2FA) relies on two or more of the following:
+Something the user knows (password, PIN, answers to questions)
+Something the user possesses (email account, smartphone [app or SMS], a code-generating device like hardware key)
+Something inherent to the user (fingerprint, face scan, voice recognition)
As with all matters cybersecurity, the art of achieving increased security in this way is a balancing act between convenience and safety, and not every solution is fitting for every setting. Putting users through a veritable assault course of authentication may well increase the organization’s security but will quickly develop a discouraged workforce.

In this article, we feature two suppliers of workplace-oriented authentication platforms whom we consider to offer something unique to businesses and organizations of any size. It’s never too early to adopt the type of measures described below, as the benefits do not just pertain to cybersecurity.
The business that deploys such solutions can make significant savings, in password management costs (creating, resetting and managing passwords), HR (assigning new staff privileges according to status), access control to buildings and facilities, IP protection (shutting down all access to systems quickly if employees/ex-employees develop a malicious streak), and overall data governance.
On the latter issue, operations managers and compliance officers know that a great deal of legislative oversight consists of the ability to prove that systems are in place to protect personal and company data. 2FA or MFA mean that a great deal of compliance is achieved almost as a peripheral gain from installing a platform that was primarily considered because of cybersecurity concerns.
OKTA
Okta’s platform is cloud-based, which has a significant advantage in that it’s the conduit through which access is granted to employees, wherever they are, on whichever device they’re working, and whether or not they’re protected by network-centric protection, like firewalls and old-school multi-factor authentication systems. That in itself neatly reflects today’s employee working habits, which includes at home, en route, in coffee shops or airport lounges.
From the point of view of even the lowliest helpdesk operator, having one log-in to multiple apps is a revolutionary time saver. Instead of resetting passwords for multiple apps whenever they’re forgotten, or an employee leaves the business, one simple entry updates everything.
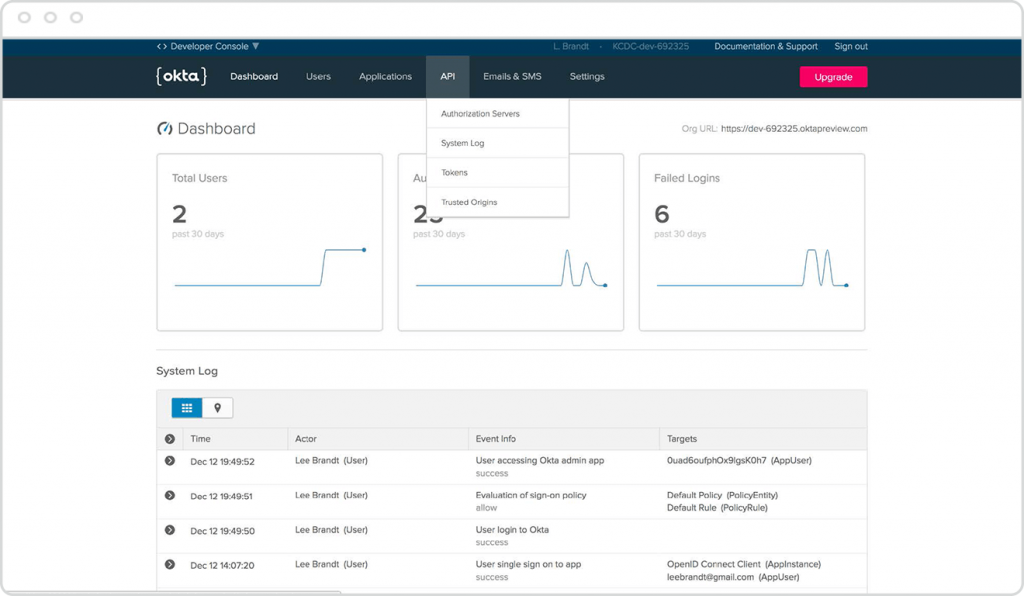
Source: Okta
Okta’s rule-based privilege structure allows preset access to sets of apps and services, at specific levels. When new interns arrive, or temporary contractors need access to particular systems, they can be assigned secure logins in seconds, which are only viable with an additional layer of authentication.
Privilege models can be changed across the board, or individually, depending on status or need. Moreover, closing off access in seconds to all sensitive systems is just a matter of a few clicks.
Of course, the most secure passwords may get shared around “off the record.” Here, Okta’s multi-factor authentication systems come into play. Staff at any level verify their identity directly, with an SMS to their phone, or being confirmed by their mobile (which could be facial recognition, a fingerprint, PIN or passcode).
There’s lots more to Okta – read more about the offerings in specific detail here.
IBM
As you might expect from such a large company, IBM has a broad range of identity management solutions. Its catchall phrase is IAM (Identity and Access Management), which being a solidly business-focused concern, IBM points at regulatory compliance as a critical underpinning of all its IAM offerings.
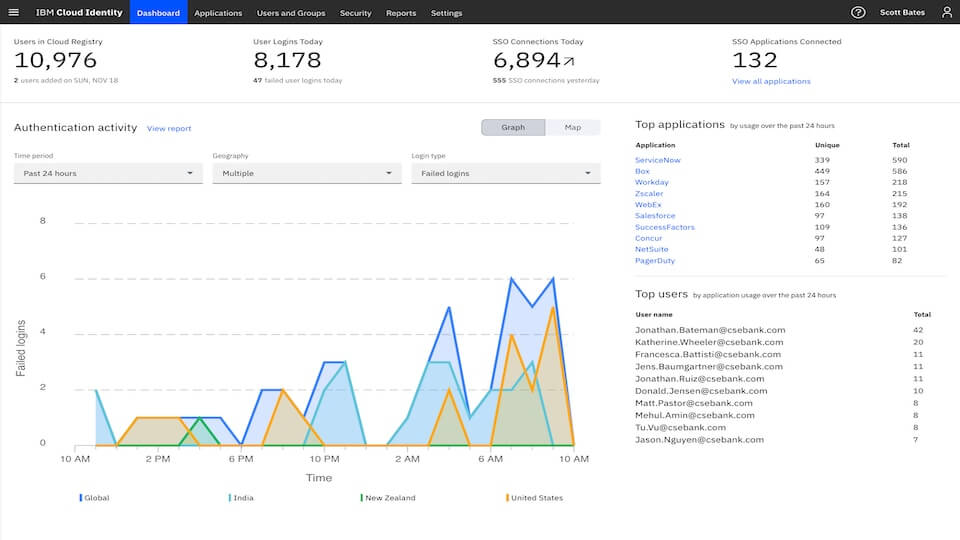
Source: IBM
The company offers single sign-on, so one set of credentials grants rights to multiple systems and platforms. IBM Verify, for instance (part of IBM Security Access Manager), adds authentication via users’ mobiles. The technology can protect your IBM Cloud identities, as well as providing access to everyday office applications like databases, file stores and Office 365. IBM platforms only flag anomalies when risks are detected, meaning that users are less troubled by password management – an important component of identity management’s acceptance right across the workforce.
IBM Security Secret Server controls which applications can run on endpoints (both handhelds and desktops) and servers to prevent malicious apps from penetrating the environment. This type of platform from IBM reflects the overall shift in cybersecurity circles away from protecting the network, to safeguard the individual (or, in some instances, protecting systems from the individual).
There’s even the use of IBM’s AI (artificial intelligence) platform, Watson, in the guise of IBM MaaS360 with Watson™, with which the core learns about users’ daily behavior to better identify anomalies, and thereby proactively protect the enterprise.
*Some of the companies featured on this editorial are commercial partners of Tech Wire Asia
READ MORE
- Strategies for Democratizing GenAI
- The criticality of endpoint management in cybersecurity and operations
- Ethical AI: The renewed importance of safeguarding data and customer privacy in Generative AI applications
- How Japan balances AI-driven opportunities with cybersecurity needs
- Deploying SASE: Benchmarking your approach
