Two sides of the story on the Microsoft outage incident. (Source – Shutterstock)
Who caused Microsoft’s outage?
- Anonymous Sudan or Storm-1359 targeted Microsoft with a disruptive DDoS attack.
- Speculation about the operation having Russian ties.
For several weeks now, cybercriminals have been highly active, orchestrating attacks against some of the world’s largest organizations. Recently, Microsoft was at the receiving end of a Distributed Denial-of-Service (DDoS) attack by Storm-1359, also known as Anonymous Sudan, that resulted in service disruptions.
As early as June, a surge of complaints on Twitter indicated that up to 18,000 users couldn’t access Outlook due to what eventually came to light as a DDoS attack. Microsoft confirmed the incident in a blog post and provided technical details and suggestions to prevent such attacks.
These recent cyberattacks presumably hinged on using several virtual private servers (VPS), combined with hired cloud infrastructures, open proxies, and DDoS tools. Interestingly, the DDoS operation specifically targeted the seventh layer of network architecture, instead of the third or fourth.
Details on DDoS traffic attacks
Microsoft’s analysis shows that Storm-1359, a group with access to various botnets and tools, conducts DDoS attacks from cloud services and open proxies. They primarily aim to create disturbances and garner attention.
Storm-1359 utilizes several Layer 7 DDoS traffic attacks:
- HTTP(S) flood attack: overwhelms system resources with a flood of SSL/TLS handshakes and HTTP(S) requests, depleting backend computing resources.
- Cache bypass: overloads origin servers by generating queries against URLs, forcing all requests to the origin rather than using cached contents.
- Slowloris: maintains an open server connection by slowly downloading requested resources, keeping the requested item in memory.
Though it’s unclear from the blog post if Microsoft regained control or ended the attack, updates from the Microsoft 365 Status Twitter account suggest they had control over the situation by the morning after the disruption on June 5th.
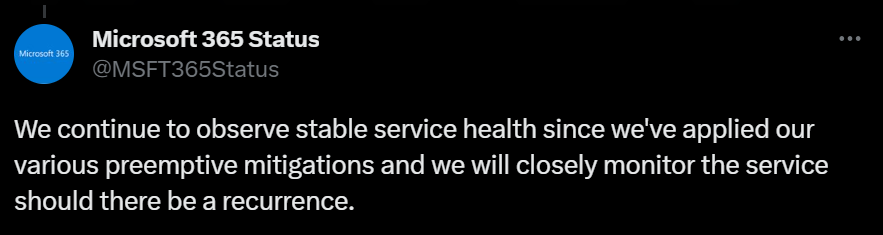
Microsoft gives updates on the outage incident. (Source – Microsoft 365 Status Twitter)
To counteract these attacks, Microsoft has enhanced its Layer 7 defenses, adjusting the Azure Web Application Firewall (WAF) to protect customers from similar DDoS incursions better. Even though these defensive measures are generally successful at reducing most service interruptions, Microsoft continues to evaluate the efficiency of its protection systems, using acquired insights to refine and enhance their effectiveness.
Who is Anonymous Sudan?
Anonymous Sudan emerged in January 2023, warning that they would instigate attacks against any nation that opposes Sudan. Since that declaration, they have trained their sights on various global organizations and governmental bodies, crippling them with DDoS attacks or releasing stolen data.
The group began striking at large organizations in May, imposing a ransom to end the attacks. The first strike targeted Scandinavian Airlines (SAS), with the threat actors demanding US$3,500 to halt the DDoS onslaught.
Subsequently, the group shifted its focus to the websites of American corporations, such as Tinder and Lyft, and an array of hospitals scattered across the USA.
In June, Microsoft fell into the crosshairs of Anonymous Sudan, as they launched DDoS assaults on web-accessible portals for Outlook, Azure, and OneDrive, raising their ransom demand to a staggering US$1 million.
The group taunted, “You have failed to repel the attack which has continued for hours, so how about you pay us 1,000,000 USD and we teach your cyber-security experts how to repel the attack and we stop the attack from our end? 1 million USD is peanuts for a company like you.”
During the DDoS offensive against Outlook, the group claimed their actions were in response to the USA’s meddling in Sudanese politics. Anonymous Sudan pronounced, “This is a continuous campaign against US/American companies & infrastructure because of the statement of the US Secretary of State saying there is a possibility of American invasion of Sudan.”
Expert viewpoint: DDoS attacks are not hacks
Tech Wire Asia sought input from Sergey Shykevich, Group Manager at Check Point Research, regarding this incident. Shykevich emphasized that this event should not be labeled as a hack since it does not involve any actual breach.
Shykevich explained that DDoS attacks see cybercriminals flooding a website with communication requests, which can collapse the website when executed at the right scale. “So all the attacks involved here are on the websites of these platforms, which were simply unreachable for a certain amount of time from minutes to about 20-30 min or so,” he stated.
Shykevich further illuminated that while DDoS attacks are significant in user accessibility (as they prevent users from accessing a website), they are not particularly sophisticated. Consequently, anyone who can gain access to the necessary tools, such as bot farms that allow many requests to a single website, can execute these attacks. He mentioned that this particular group is infamous for using potent DDoS tools, and maintaining strong connections to Russian hacking groups, who currently utilize such means in their operations.
Shykevich conveyed that it is indeed possible to thwart DDoS attacks. It boils down to resource allocation and risk management. The more effort and resources invested in monitoring the incoming requests to the website, and the greater the capacity to handle a larger volume of simultaneous requests, the less likely it is for overwhelming requests to crash the website.
What these cybercriminals undertake is a careful analysis of the bandwidth or capacity of their target websites by sending a specific volume of simultaneous requests, and they keep escalating this volume until they witness the site buckling under pressure.
“As most companies can bounce back from this crash, many prefer to invest elsewhere and suffer for a certain amount of time when the website is down. The website will then return when the traffic to the website is more moderate,” he emphasized.
Could Anonymous Sudan be a Russian decoy?
Just when it seemed like everything was back to normal, an unexpected development arose. The Guardian has reported that some cybersecurity researchers are speculating this might be a decoy operation, suggesting the group could have connections to Russia instead.
In a recent report, cybersecurity firm CyberCX argued that the group is unlikely to be a genuine hacktivist organization, pointing to a probable link to the Russian state after examining the group’s activities.
According to CyberCX, most hacktivist groups plan their operations in a somewhat public manner online, but Anonymous Sudan had only disclosed their targets at the time of the attacks, suggesting a highly confidential operation.
The firm also highlighted that the group’s use of paid infrastructure for the attacks—steering an enormous volume of traffic towards a service to crash it—would have cost tens of thousands of dollars, making it improbable for a loosely associated group to afford.
CyberCX further stated that Anonymous Sudan has publicly aligned itself with pro-Russian threat actors and is part of the pro-Russia hacking group, Killnet.
Alastair MacGibbon, CyberCX’s chief strategy officer, shared with Guardian Australia that Anonymous Sudan’s generally low-level targets and its presentation as an Islamic group suggest a Russian-backed organization could be attempting to stir societal divisions and destabilize the west.
MacGibbon pointed out that this behavior reflects the Russian government’s tendencies to cause societal discord, highlighting that the issue doesn’t matter to them. Their objective is simply to exploit whatever can cause harm to their targets, which in this case is the west.
He also noted an emerging pattern of cyberattacks from Russian-linked hacker groups targeting Australia. He referred to the Optus and Medibank attacks from the previous year as “less monetizable forms of attack,” where the groups threatened to leak data online instead of engaging in ransomware attacks.
“There has to be a link to other forms of monetization, potentially a state or some form of direction coming from the state that says ‘go and cause fear, uncertainty and doubt,” he said.
This is not the first time for Microsoft
This is not the first instance of Microsoft making news for cybersecurity-related issues. In October 2022, they were in the spotlight when a data leak, dubbed the ‘BlueBleed’ data leak, exposed over 548,000 users.
Security firm SOCRadar discovered more than 2.4 terabytes of exposed data due to a misconfigured Microsoft endpoint. According to SOCRadar, this exposed data involved over 65,000 companies and 548,000 users, encompassing customer emails, project details, and signed documents.
Microsoft confirmed the data leak through a blog post. They stated that they had secured the endpoint and notified the affected accounts, assuring that while the data had been exposed, there was no evidence of actual compromise of customer accounts.
In another incident, Microsoft was breached by the Lapsus$ Group in March 2022. The hacker group Lapsus$ released a screenshot on their Telegram channel implying that they had infiltrated Microsoft. The screenshot from within Azure DevOps—a collaborative software developed by Microsoft—suggested that the breach had impacted Bing, Cortana, and other projects.
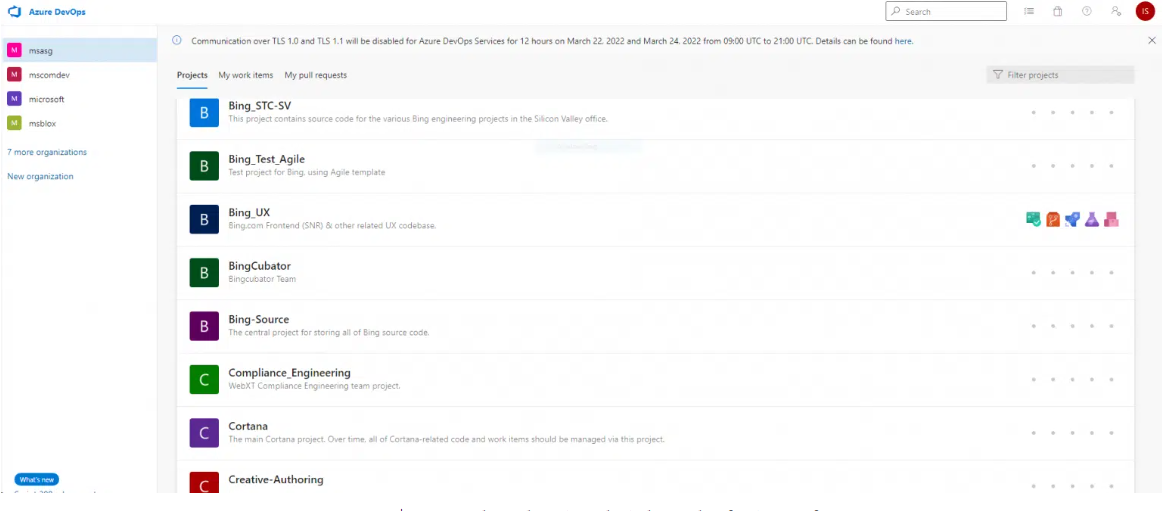
Lapsus screenshot showing their breach of Microsoft. (Source – Vice News)
On March 22, Microsoft released a statement acknowledging the attack. They emphasized that no customer data had been compromised; according to Microsoft, only a single account was hijacked, and the company’s security team successfully thwarted the attack before Lapsus$ could delve further into their organization.
In an extensive blog post, Microsoft’s security team characterized Lapsus$ as “a large-scale social engineering and extortion campaign against multiple organizations with some seeing evidence of destructive elements.” They elaborated on the group’s tactics, indicating that Microsoft had been closely observing Lapsus$ prior to the breach.
Meanwhile, Lapsus$ has consistently claimed their motivations are purely monetary, stating, “Remember: The only goal is money, our reasons are not political.” They are known to exploit insider threats and recently published a notice encouraging tech workers to compromise their employers.
READ MORE
- 3 Steps to Successfully Automate Copilot for Microsoft 365 Implementation
- Trustworthy AI – the Promise of Enterprise-Friendly Generative Machine Learning with Dell and NVIDIA
- Strategies for Democratizing GenAI
- The criticality of endpoint management in cybersecurity and operations
- Ethical AI: The renewed importance of safeguarding data and customer privacy in Generative AI applications