
Insider threats always lurking in the shadows. (Source – Shutterstock)
How financial services can ward off insider threats
In the intricate and sophisticated world of financial services, the threat landscape is complex and continuously evolving. While external threats often garner the most attention, there is often an equally pressing concern lurking in the shadows: insider threats.
These threats originate from individuals within the organization – employees, contractors, or even partners entrusted with access to sensitive information. From unintentional data leaks to malicious acts aimed at personal gain or causing harm to the firm, insider threats can wreak significant havoc on financial service firms.
The costly impact of insider threats
According to Proofpoint’s 2023 Voice of the CISO report, 82% of CISOs globally believe that departing employees have contributed to data loss incidents. This statistic highlights the potential risks posed by insiders who have access to sensitive information and may exploit it upon leaving the organization.
The 2022 Ponemon Cost of Insider Threats Report revealed that the annual cost of insider threats for financial services is 38% higher than the average, at US$21.3 million compared to US$15.4 million. The potential losses involving corporate information and client funds contribute to this increased financial impact.
The annual growth of insider threats for financial services is higher at 54%, surpassing the average growth rate of 44% across industries. This trend may be attributable to the inherent accessibility internal employees have to financial information related to client funds and pre-trade market data.
These findings underscore the critical nature of insider threats within financial services firms. The potential loss of sensitive corporate information and client funds can result in severe consequences, leading to substantial financial implications for these organizations.

John Checco, the Resident CISO at Proofpoint,
To gain a better understanding of the complexities of insider threats in the financial services sector, we have insights shared by John Checco, the Resident CISO at Proofpoint, who spoke to Tech Wire Asia regarding this pressing issue.
John Checco offered enlightening insights on why insider threats constitute a significant obstacle in this sector. He mentioned that financial firms responsible for managing money on behalf of clients present unique opportunities for insiders. This dual vulnerability—either pilfering organizational data or misappropriating client funds—necessitates robust safeguards.
Additionally, Checco touched upon how the data generated by financial firms play a critical role in both global and local economies. This makes these firms a prime target for threat actors seeking to manipulate market data for their unfair advantage, underscoring the need to ensure the integrity of financial data to maintain market stability.
Furthermore, he underscored the importance of an integrated approach to security within large financial firms. Despite having distinct teams handling various security tasks, treating these areas as separate entities can create vulnerabilities. To counter insider threats effectively, a holistic approach that covers areas like financial fraud, cybercrime, data loss prevention (DLP), insider threat management (ITM), and email security is crucial.
Inside the mind of insider threats
In an interview with Checco, he identified three types of insider threats that financial services companies should be aware of: careless activity, malicious behavior, and compromised accounts.
Checco explained, “Careless users, despite having good intentions, can inadvertently compromise sensitive information. 58% of insider-related incidents are attributed to careless activities including system misconfiguration, mistyped recipients, mistaken file attachments, or just simple over-sharing.”
On the other hand, malicious users are motivated by personal gain or a sense of entitlement. Checco mentioned how an account lead changing employers might wrongfully believe that their contact list belongs to them when it belongs to their former employer. Similarly, a software engineer may reproduce a patented process they invented outside of the company, despite the patent being owned by the company. Malicious intent accounts for 25% of insider-related incidents, where insiders purposefully exploit their access for personal benefit or to harm the organization.
Checco says compromised users involve account takeovers, often achieved through phishing, social engineering, or telephone-oriented attack delivery (TOAD). “While the originator of an account takeover (ATO) may be an external threat actor, some organizations consider them insider threats due to the inherent accessibility of the compromised accounts to company information. 17% of insider-related incidents are traced back to ATO,” Checco added.
Adopting a people-centric approach to cybersecurity
Recognizing the escalating dangers of insider threats, Checco advocates a modern, people-centric approach to information protection. What does that entail, and why is it important?
Checco emphasized that as technology security has matured, the technological barrier to entry has become increasingly complex, prompting threat actors to target people instead. This shift is why people-centric risks have consistently remained the most significant ones reported yearly since 2012.
“A modern and people-centric approach in cybersecurity recognizes the human factor and the limitations of technology alone in fully protecting an organization,” he added. “With people-centric security, organizations will have complete visibility and context into how insiders are interacting with corporate data and assets.”
Moreover, equipped with this knowledge, organizations can deploy strategies and tactics that disrupt different stages of the cyber-attack chain, thereby blocking cyber criminals. By initially focusing on people, organizations can minimize human factor risks and implement targeted measures to break the attack chain. Ultimately, Checco believes that this approach creates a more resilient security framework that aligns with the evolving threat landscape and the role humans play in it.
To get started with implementing a people-centric approach, financial institutions can manage their workforce using a multi-pronged approach to cybersecurity.
Checco emphasizes layered defense tactics, which include security awareness training, reducing opportunities for email-based compromise, limiting access to minimum viable operations, ensuring safe browsing on the internet, mitigating data movement across sensitivity borders, and using next-generation artificial intelligence (AI) and machine learning (ML) to identify risky work activities.
Applying a people-centric approach
Checco stated how these strategies have made a significant difference. He shared that the security team at an undisclosed financial trading firm was asked to perform a security assessment on a new pre-trade compliance tool.
“During the course of the assessment, we identified a potential population of employees with access to pre-trade market data – development teams using copies of production market data in their testing. To determine the extent of this risk, a smoke test was conducted, using tagged data, on a sample development team. The test revealed instances of front-running by some members of the team,” said Checco.
The challenges in this instance included the untenable cost of creating and maintaining a fully robust set of test data for development. Additionally, monitoring abnormal trade activity among developers proved to be incredibly complex.
Checco added that the solution to address this insider threat was a people-centric approach – the firm required all developers to enroll in the pre-trade compliance solution. This approach acknowledged that technology alone was insufficient in managing the risks posed by insider activity. Instead, it focused on the people involved, ensuring adherence to compliance standards.
Four actionable steps to bolster security posture
When asked about actionable steps that financial services companies can immediately take to improve their security posture against insider threats, Checco highlighted four steps that companies can take:
- Trigger a “Violation of Violations”: Aggregate logs from disparate security sources and correlate them based on common attributes such as user, IP, or department, to name a few. Alerts should be triggered when multiple minor rule violations occur quickly from the same source, which indicates a high probability of an internal threat actor.
- Reflect on the security program: Identify areas along the cyber-attack chain that require more attention and where the organization’s mitigations, response, and recovery measures may be lacking. Focus on improving existing security controls rather than chasing new solutions. Build the security program to deliver capabilities rather than relying on specific solutions, allowing for easier adaptation and replacement as needed.
- Build contextual incident narratives: Identify users’ activities, access patterns, and intents (including potentially compromised users or departing employees). Enhance triggered events by integrating data from various sources into a Security Information and Event Management (SIEM) system and utilize artificial intelligence (AI) and expert interpretation to derive context around incidents. Then, construct comprehensive security incident narratives by incorporating multiple viewpoints and evidence.
- Proactively build internal relationships: Establish and nurture internal relationships with business stakeholders, legal counsel, and relevant board members. Collaborate on developing and refining ITM/DLP policies, controls, reporting mechanisms, and conduct tabletop exercises. Look for protection synergies through cross-functional collaboration, such as integrating event data from different security tools or forging relationships between operational teams to enhance incident response playbooks. Maintain regular informal touchpoints with these stakeholders to foster ongoing collaboration and information sharing.
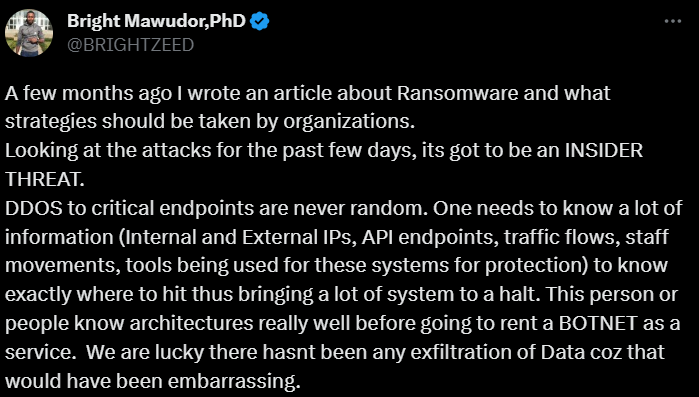
A Twitter user, @BRIGHTZEED, talking about the insider threats being the cause of most attacks. (Source – Twitter)
Insider threats will remain a pervasive issue in the financial sector, but by deploying comprehensive strategies that incorporate technological advancements, enhanced security measures, and fostering a strong culture of security awareness, financial services companies can mitigate these threats effectively.
As John Checco rightly said, “Security is not a destination, but a journey.” It’s a journey that every financial institution must undertake to protect not only their bottom line but also the critical role they play in the global economy.
READ MORE
- Strategies for Democratizing GenAI
- The criticality of endpoint management in cybersecurity and operations
- Ethical AI: The renewed importance of safeguarding data and customer privacy in Generative AI applications
- How Japan balances AI-driven opportunities with cybersecurity needs
- Deploying SASE: Benchmarking your approach


