
Cybercriminals have been using PDFs to release malware into organizations.
Malware in PDFs – the next big risk for businesses
|
Getting your Trinity Audio player ready... |
When it comes to malware, businesses are normally infected through phishing emails or spam. In most cases, the malware infects a device after its user opens a link or downloads a file containing malware.
Cybercriminals rely on this malicious software to exploit devices, services or networks. Malware is typically used to extract data that can be leveraged for financial gain. Over the years, some of the biggest malware included the Petya ransomware, Mirai botnet and Emotet Trojan – all of which wreaked havoc on organizations.
As malware infiltrates organizations mostly through emails, research by Palo Alto Networks indicates that 66% of malware is delivered through PDFs as malicious email attachments. PDFs have been around for some time and according to Duff Johnson, executive director of the PDF Association, trillions of PDF files now exist in the world and billions more are created daily.
PDF files are commonly used in a business environment, and victims are less likely to be wary of an expected file type, compared to an unexpected file type like EXE. They could also simply be unaware that a PDF could be used for nefarious purposes. Viruses, Trojans, and malware have many ways of hiding inside a PDF and often show up in email downloads or attachments like eBooks and other documents. They usually come from unknown or unfamiliar senders.
The Unit 42 Network Threat Trends Research Report, is backed by telemetry from Palo Alto Networks Next-Generation Firewall, Cortex Data Lake, Advanced URL Filtering and Advanced WildFire. The research also stated that the average number of malware attacks experienced per organization in the manufacturing, utilities, and energy industry increased by 238% (between 2021 and 2022).
“Most people are aware of warnings against clicking strange links in emails, so PDF phishing schemes could fly under their radar better than a text-based email with just a plain link,” states Palo Alto Networks. Scammers are exceptionally skilled with social engineering tactics, as phishing emails are usually designed to manipulate a reader’s emotions or tap into their unconscious biases.
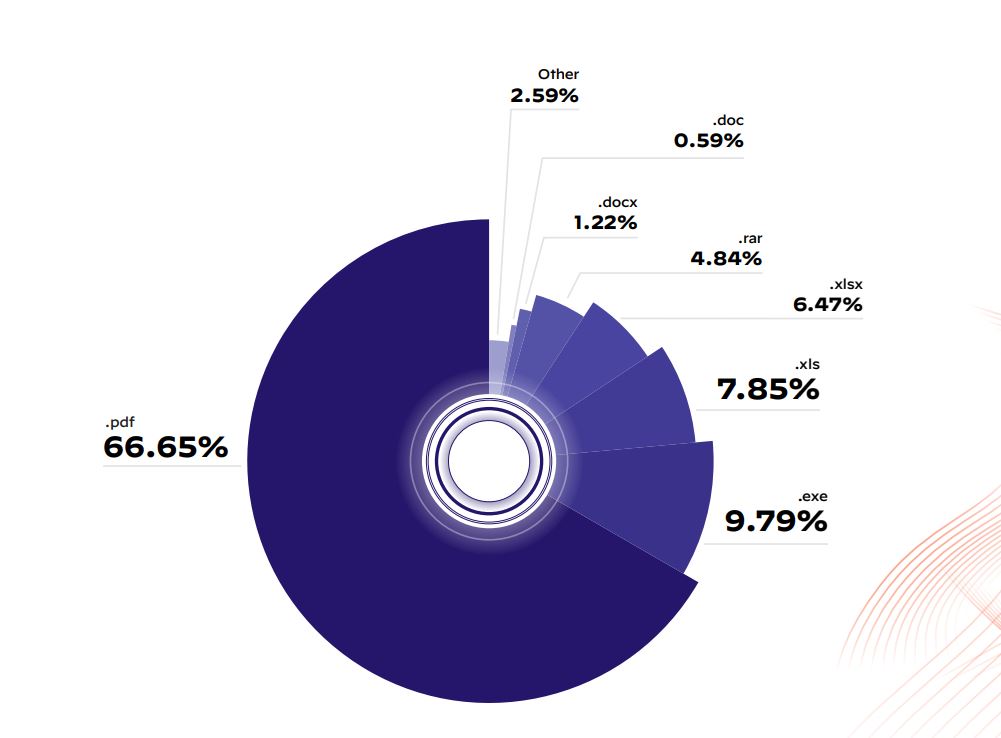
66% of malware are delivered through PDFs. (Source – Palo Alto Networks)
Some popular PDF phishing schemes include naming conventions expected in a business context, such as “invoice_AUG_4601582.pdf” or “Updated Salary Evaluation”, which could lure unsuspecting targets into opening these attachments. They might contain a URL link to click or a button that sends victims to a website with a malicious purpose.
In fact, malware in PDFs are becoming such a menacing problem that NASA’s Jet Propulsion Laboratory (JPL) has created the world’s largest open-source archive of PDFs, containing eight million individual files. These will be used by research groups developing tools to detect malware embedded in the file type’s code.
The corpus is one of several tools JPL has created with the PDF Association to help improve online security. Scientists across the world can use the resource to identify privacy vulnerabilities in software or anticipate future cyber threats.
Malware is just one part of the problem
As technology continues to develop, scammers are always looking for new ways to exploit cracks within an interconnected network. “With a cunning blend of evasion tools and camouflage methods, the bad actors have weaponized the threats,” says Steven Scheurmann, Regional Vice President, ASEAN at Palo Alto Networks.
The report also highlighted several other findings. This includes a 55% increase in vulnerability exploitation attempts per customer when compared to 2021. ChatGPT-related threats have also increased with Unit 42 reporting a 910% increase in monthly registrations for domains — both benign and malicious – from November 2022 to April 2023. These domains attempt to mimic the AI chatbot that has made headlines across the globe.
With an estimated 90% of public cloud instances run on Linux, attackers are seeking new opportunities in cloud workloads and Internet of Things (IoT) devices running on Unix-like operating systems. The most common types of threats against Linux systems are: botnets (47%), coinminers (21%) and backdoors (11%).
At the same time, cryptominer traffic doubled in 2022, with 45% of sampled organizations having a signature trigger history that contains cryptominer-related traffic. Threat actors are using SSL-encrypted traffic to blend in with benign network traffic.
Findings from the report also stated that to avoid detection, threat actors use newly registered domains (NRDs) for phishing, social engineering, and spreading malware. Threat actors are more likely to target people visiting adult websites (20.2%) and financial services (13.9%) sites with NRDs.

Viruses, Trojans, and malware have many ways of hiding inside a PDF. (Source – Shutterstock)
Dealing with malware in PDFs
When it comes to PDFs, no one knows them better than the godfather of PDFs, Adobe. Having developed PDFs more than three decades ago, the company continues to innovate tools for PDFs and is aware of the growing risks of malware in PDFs.
While there are many proactive ways to protect against hacking, Adobe suggests the following three steps to defend against malware in PDFs. They include:
- Recognizing phishing attempts
- Using a trusted PDF reader
- Running regular virus scans
Palo Alto Networks also suggests that in addition to traditional detection approaches, like signature-based detection and malicious URL labeling, machine learning models can protect against rapidly changing PDF phishing campaigns.
For example, Advanced WildFire, a cloud-based malware prevention service, is natively integrated into all Palo Alto Networks products and blocks activity associated with known and unknown malware variants as well as other file-based threats. Advanced Threat Prevention leverages the firewall’s visibility to inspect all traffic and automatically prevent known exploits, malware and spyware regardless of port, protocol or SSL encryption.
READ MORE
- Safer Automation: How Sophic and Firmus Succeeded in Malaysia with MDEC’s Support
- Privilege granted, not gained: Intelligent authorization for enhanced infrastructure productivity
- Low-Code produces the Proof-of-Possibilities
- New Wearables Enable Staff to Work Faster and Safer
- Experts weigh in on Oracle’s departure from adland


