
Dark Pink: The cyber tune you never wanted to hear
- Group-IB has dissected Dark Pink’s attacks on eight entities across APAC and Europe.
- Group-IB revealed five more Dark Pink victims, suggesting a broader reach.
It seems like Blackpink’s lyrics, “It’s not a comeback since we’ve never left,” are ringing true; they’re always in your area. This time around, they’ve finally decided to shut it down by targeting government agencies and organizations. Wait, it’s actually not the K-pop sensation, Blackpink, at all. Instead, it’s the Advanced Persistent Threat (APT) group, Dark Pink, causing all the disruption.
Rest assured, the popular K-pop group has nothing to do with this. Group-IB recently unveiled that the malicious activities of Dark Pink have affected 13 organizations across nine countries.
In January 2023, Group-IB’s Threat Intelligence unit provided an in-depth breakdown of Dark Pink’s operations, tracing the group’s attacks on seven organizations in the Asia-Pacific (APAC) region, and one in Europe.
How APT Dark Group strikes
What’s unique about Dark Pink? They’ve adopted tactics, techniques, and procedures rarely seen before in known APT groups. They employ a distinctive toolkit, including TelePowerBot, KamiKakaBot, and information stealers Cucky and Ctealer, with the intent to swipe confidential documents from government and military organizations’ networks.
The group has demonstrated an ability to infect even USB devices connected to compromised computers and gain access to messengers on infected machines. Here are some key findings from the report:
- Dark Pink carried out seven successful attacks on prominent targets between June and December 2022.
- The group’s initial activity, linked to a GitHub account used by the threat actors, was recorded in mid-2021, and the first attack attributed to Dark Pink took place in June 2022. Their activity peaked in the last quarter of 2022 with four confirmed attacks.
- Victims of Dark Pink can be found in five countries within the Asia-Pacific region (Vietnam, Malaysia, Indonesia, Cambodia, Philippines) as well as one European nation (Bosnia and Herzegovina).
- The victims included military bodies, government and development agencies, religious organizations, and non-profit organizations.
According to Group-IB analysts, the group was first linked to an attack on a religious entity in Vietnam in June 2022. However, evidence points to an earlier start, as a GitHub account associated with the threat actors indicated activity as far back as mid-2021.
Expanding reach: The APT’s international intrusion
After the June 2022 attack, Dark Pink seemingly went dormant, as Group-IB analysts detected no further malevolent activity. Yet, as summer concluded, the APT group sprung into action. A Vietnamese non-profit organization was targeted in August 2022 in an attack mirrored the earlier June incident. From then on, Group-IB could link the group to a sequence of attacks – one in September, two in October (with one being unsuccessful), two in November, and one in December. The most recent discovery by Group-IB was an intrusion by Dark Pink into an Indonesian governmental organization on December 8, 2022.
Recently, Group-IB experts discovered five new victims of Dark Pink, and the group’s reach is broader than initially thought. Organizations in Brunei, Thailand, and Belgium have all been targeted by the group. The group’s activity has persisted, with recent attacks on a government ministry in Brunei in January and a government agency in Indonesia in April 2023. Moreover, three other attacks from 2022 have been attributed to the group.
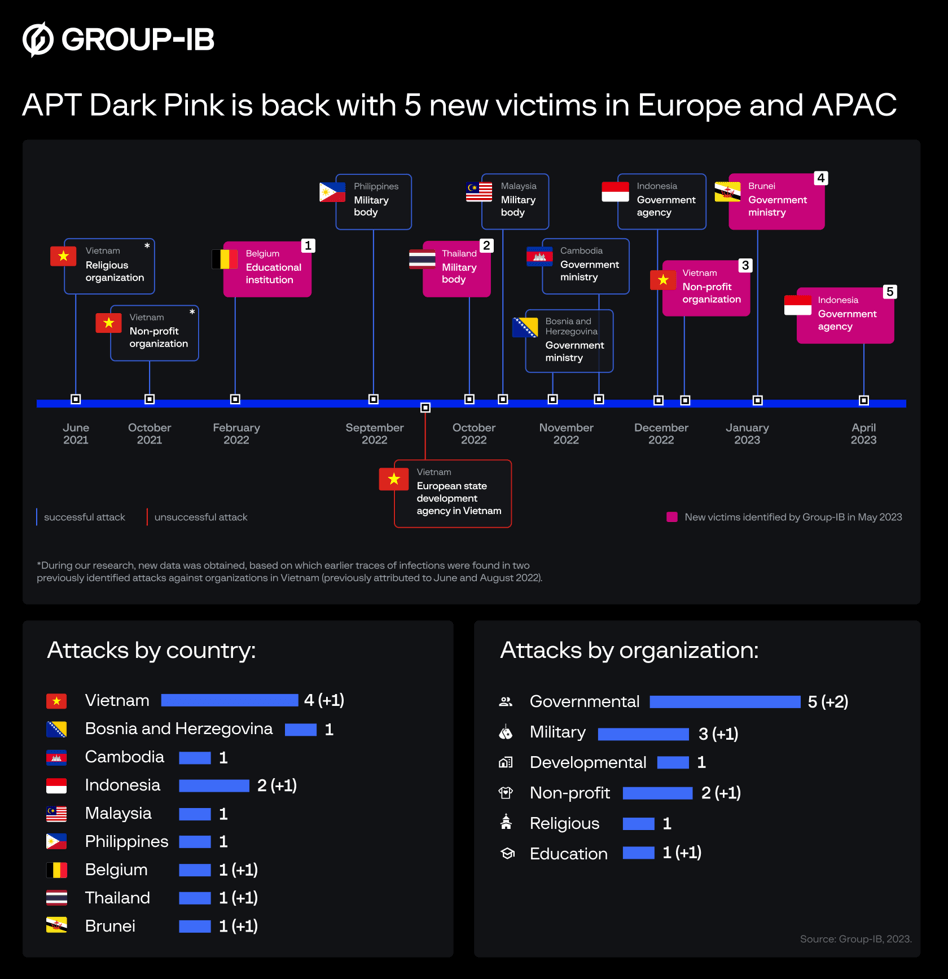
Dark Pink APT victim overview (Source – Group IB)
Dark Pink primarily infiltrates systems via spear-phishing emails, using a custom toolkit to extract files and messenger data from infected devices and networks. Recent updates to these tools have seen the group evade cybersecurity defense mechanisms more effectively. As an example, the custom KamiKakaBot module that interprets and performs commands from the threat actors through Telegram has been divided into two segments: one with the function of managing the device, and the other dedicated to pilfering confidential data.
Unmasking Dark Pink: The role of Group-IB’s Threat Intelligence
Group-IB’s Threat Intelligence unit located a new GitHub account created by Dark Pink shortly after the first public disclosure about the APT group. Group-IB noted 12 commits to the new account between January 9 and April 11, 2023.
Dark Pink has also begun extracting stolen data via an HTTP protocol using the Webhook service and utilized MS Excel add-in functionalities to ensure the persistence of TelePowerBot, a simpler version of KamiKakaBot written in PowerShell. Following Group-IB’s zero-tolerance policy towards cybercrime, all potential and confirmed victims of Dark Pink have been proactively alerted.
Andrey Polovinkin, a Malware Analyst at Group-IB, warns that the group shows no signs of slowing down. “Dark Pink’s resilience and ability to continually adapt their custom tools to evade detection is typical of APT groups. The affected targets’ profile emphasizes Dark Pink’s substantial threat to both public and private sectors. Group-IB will continue monitoring all Dark Pink activity and ensure confirmed and potential victims are promptly informed,” Polovinkin further explained.
With the persistent threat posed by groups like Dark Pink, the importance of robust cybersecurity systems and threat intelligence cannot be overstated. The battle against cybercrime is ongoing, and organizations must remain vigilant, adapt to the evolving landscape, and strengthen their security measures to thwart such attacks.
READ MORE
- Strategies for Democratizing GenAI
- The criticality of endpoint management in cybersecurity and operations
- Ethical AI: The renewed importance of safeguarding data and customer privacy in Generative AI applications
- How Japan balances AI-driven opportunities with cybersecurity needs
- Deploying SASE: Benchmarking your approach


