The rise in DDoS attacks correlates with Russian companies increasingly moving into the APAC region. (Image – Shutterstock)
DDoS attacks are increasing in APAC
- APAC records a 26% increase in DDoS attacks in Q3, 2023.
- The rise in DDoS attacks correlates with Russian companies increasingly moving into the APAC region.
- Adopting automated DDoS protection services from trusted providers may solve the problem.
Recently, ChatGPT became one of the biggest victims of DDoS attacks when it suffered from a periodic outage. Reports showed that the outage was due to DDoS attacks targeting its API and ChatGPT services.
While a report by Bleeping Computer stated that the company didn’t immediately provide any details on the root cause of these incidents, OpenAI confirmed earlier today that they are linked to ongoing DDoS attacks. Anonymous Sudan claimed the attacks, saying that the reason behind them is the company’s “general bias towards Israel and against Palestine.”
The recent DDoS attack on ChatGPT has been claimed by Anonymous Sudan.
In fact, geopolitical issues are the cause of most cyberattacks around the world today. In Asia Pacific (APAC), DDoS attacks continue to be a major problem for organizations – despite companies boosting their cybersecurity, DDoS attacks in APAC have increased by 26% in the third quarter of 2023 compared to the same period last year.
According to a report by StormWall, the figure comes from analyzing attacks against the cybersecurity provider’s clients. The rise in DDoS attacks correlates with Russian companies increasingly moving into the APAC region. Due to economic sanctions in the US and EU, these companies are forging new partnerships in countries like China, Hong Kong, India, and North Korea—nations that have amicable relations with Russia.
This expansion is creating fresh targets in the region, catching the attention of both profit-driven cybercriminals and hacktivists. As a result, StormWall is seeing the introduction of new attack strategies and technologies.
Interestingly, e-commerce companies were hit the hardest, recording 37% of all DDoS attacks in Q3 2023 in the APAC region. Telecom and media sectors followed, accounting for 26% and 19% of total attacks, respectively. Geographically, Hong Kong faced the most incidents with 22%, followed by South Korea at 19% and India at 17%.
Singapore also recently experienced a major cybersecurity incident when a DDoS attack took out the websites of the country’s public healthcare institutions, causing an hour-long outage. While critical healthcare services were unaffected, services that required internet connectivity, including websites, emails and productivity tools for staff, were inaccessible during the disruption.
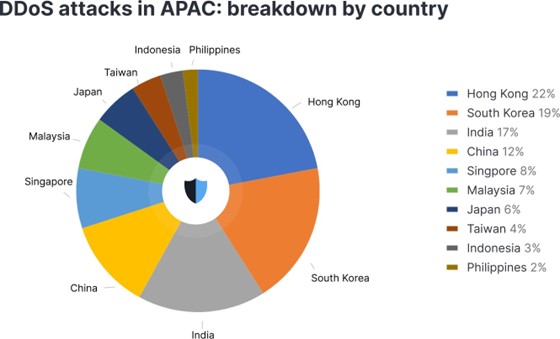
DDoS attacks in APAC. (Source – StormWall)
What is a DDoS attack?
A DDoS attack is a type of cyberattack that tries to make a website or online service unavailable by sending a lot of fake requests from many different sources. The goal is to overwhelm the target with so much traffic that it cannot handle legitimate requests from real users. A DDoS attack can cause slow performance, downtime, or even crash the target server altogether.
Some common types of DDoS attacks are:
- SYN flood: this attack sends a lot of requests to initiate a connection with the target server, but never completes the handshake. This leaves the server waiting for a response that never comes and eventually exhausts its resources
- UDP flood: this attack sends a large number of UDP packets (a type of data packet) to random ports on the target server. The server has to check if there is any application listening on those ports, and if not, send back an error message. This consumes a lot of bandwidth and processing power.
- HTTP flood: this attack sends a lot of HTTP requests (a type of web request) to the target server, often using a botnet (a network of compromised devices) to generate the requests. The server has to process each request, which can overload its CPU and memory.

Did you know that DDoS attacks can be purchased?
DDoS attacks in APAC
StormWall’s data revealed that most attacks were both short and intense. A notable 38% lasted only between 5 and 15 minutes. Short attacks are hard to detect without automated systems. When looking at bandwidth, 32% of attacks fell within the 1 to 10 Gbps range. The most intense attack clocked in at 1.3 Gbps, targeting a victim in Hong Kong.
While short attack durations might imply limited damage, it’s crucial to realize that the effects of DDoS attacks can linger. Restoring affected systems can be challenging and often takes much longer than the attack itself. Also, the short nature of the attack makes it harder for humans to react in time. This means resources without automated protection are at risk.
At the same time, the report also highlighted that TCP attacks were the most common, followed by UDP, ICMP, and DNS. DNS attacks have also increased noticeably compared to the same period in 2022.
DNS helps turn user-friendly domain names into IP addresses, which is crucial for the internet to work. DNS queries often look like regular traffic, and cyberattackers are aware of this weak spot. As such, there’s been a rise in DNS amplification attacks where small queries cause the DNS to send back a massive response, using up its resources.
Web application attacks have also seen a spike. DDoS attacks targeting web applications grew by 48% in Q3 2023 compared to the same time last year. Another increase is in the deployment of DDoS botnets that combine multiple malware variants, managed by a single C&C server.
StormWall is seeing the introduction of new attack strategies and technologies. (Source – Shutterstock).
Mixed botnets present a significant threat because of their large attack surface. A pattern emerged where one botnet component floods the network with excessive data, causing a volumetric attack. At the same time, another uses a state-exhaustion attack to deplete resources of specific services. A third segment targets specific applications with an application-layer attack, causing them to fail.
This layered strategy heightens the attack’s impact and often stumps defense tools, which don’t know how to respond to multiple attack vectors. Consequently, mixed botnets can lead to greater disruptions compared to single-vector botnets.
“In Q3 2023, adversaries honed in on quick, powerful attacks to dodge security measures. Contrary to the belief that DDoS attacks need to last long to be effective, short bursts aimed at vulnerable systems can do significant damage. The effort to restore affected infrastructure is costly in both time and money, which is why most attacks wrapped up in under 15 minutes,” commented Ramil Khantimirov, StormWall’s founder.
Given the speed and increase of DDoS attacks, organizations need to be well-prepared to deal with the problem. This includes adopting automated DDoS protection services from trusted providers. Automated DDoS protection services should feature smart traffic filtering, ensuring accurate detection and mitigation of multi-vector attacks without hindering legitimate user performance.
READ MORE
- Safer Automation: How Sophic and Firmus Succeeded in Malaysia with MDEC’s Support
- Privilege granted, not gained: Intelligent authorization for enhanced infrastructure productivity
- Low-Code produces the Proof-of-Possibilities
- New Wearables Enable Staff to Work Faster and Safer
- Experts weigh in on Oracle’s departure from adland