
(Source – Shutterstock)
With great mobile device management system, comes great risks
- Two critical vulnerabilities in FileWave’s mobile device management (MDM) system have been found and publicly revealed by Team82.
- An attacker can remotely exploit the flaws, bypass authentication systems, and take complete control of the MDM platform and its controlled devices.
- Team82 found thousands of vulnerable internet-facing FileWave servers in numerous industries, such as government agencies, education, and large enterprises.
More and more employees insist on using mobile devices to do their tasks. A robust mobile device management (MDM) system should be implemented in light of the growing use of mobile devices in order to increase employee autonomy while protecting sensitive organizational data from security threats.
In contrast to the 5.7 million malicious installation packages found on mobile devices the year before, SecurityWeek reported that there were only about 3.5 million found in 2021. Although there was a significant drop, it’s worth noting that attacks on mobile devices were more advanced.
Just recently, the mdm system of FileWave has two major vulnerabilities, cve-2002-34907 and cve-2022-34906, which Claroty’s Team82 has just discovered and made public.
Cve-2022-34907, an authentication bypass flaw exists in FileWave mdm before version 14.6.3 and 14.7.x, prior to 14.7.2. This vulnerability shares characteristics with the one that was only recently discovered in the f5 big-ip waf. While Cve-2022-34906, a cryptographic key that is hard-coded, is present in FileWave mdm versions 14.6.3 and 14.7.x before 14.7.2.
An organization’s devices can be managed, monitored, and viewed by administrators using the multi-platform mobile device management system, FileWave mdm. Currently, FileWave mdm supports a wide range of devices, including smart devices like televisions, iOS and android smartphones, MacOS and Windows tablets, laptops, and workstations.
Understanding vulnerabilities in FileWave’s mobile device management system
Source – FileWave
The quick response time by FileWave was one of Team82’s research’s fruitful achievements. Following their notification, FileWave promptly created and deployed fixes for these issues and actively engaged with its customers. This demonstrates the improvement in vendors’ response times to security vulnerabilities, which significantly lowers the attack surface.
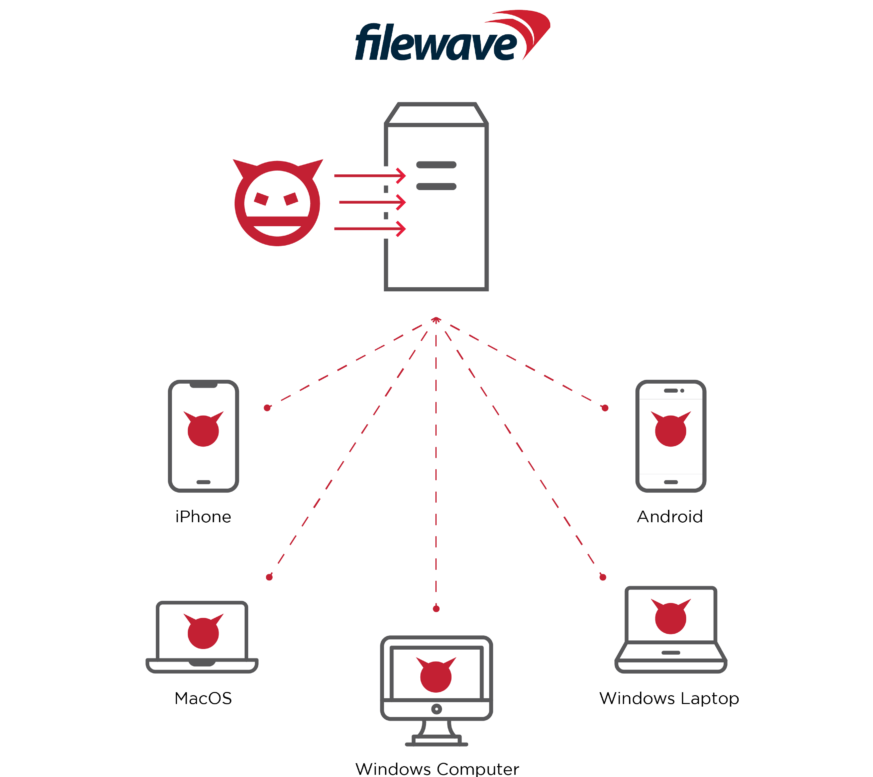
According to Team82, if the mdm is compromised, an attacker will be in a strong position to take control of all managed devices and exfiltrate sensitive information like device’s serial numbers, user’s email addresses and full names, addresses, geo-location coordinates, ip addresses, device pin codes, and much more. Additionally, attackers might exploit genuine mdm features to install malicious packages or executables. They could even use remote control protocols to directly access the device.
Team82 was able to create an exploit that gets around the platform’s authentication process and gives them access as super_user, the platform’s most privileged user, thanks to a critical vulnerability they discovered during their research that affects the authentication process of the FileWave mdm product suite.
They were also able to fully manage any mdm instance that was connected to the internet by taking use of this authentication bypass vulnerability. More than 1,100 of these instances, each holding an unlimited number of managed devices, were found during their research.
If used maliciously, this exploit might give remote attackers quick access to all instances of the FileWave mdm managed by the internet, enabling attackers to manipulate all managed devices, obtaining access to users’ private home networks, businesses’ internal networks, and much more.
During their investigation, Team82 discovered that the vulnerabilities are allegedly remotely exploitable, allowing an attacker to get beyond authentication controls and take complete control of the mdm platform and its managed devices.
In the course of their investigation, Team82 also discovered hundreds of exposed internet-facing FileWave servers across many different sectors, including huge corporations, government organisations, and educational institutions.
Users are recommended to install the most recent update from FileWave since it addresses these issues. To go into greater depth about these vulnerabilities, Team82 has published a comprehensive study.
Managing mobile devices may be a little overwhelming, no matter how necessary. With hundreds of people, it’s easy to lose sight of all the necessary tasks and the numerous devices that must be used. Therefore, it’s crucial for businesses to maintain their strict mobile device management best practises in order to safeguard corporate data. It should apply to all mobile and Wi-Fi-connected devices that employees use.
READ MORE
- Strategies for Democratizing GenAI
- The criticality of endpoint management in cybersecurity and operations
- Ethical AI: The renewed importance of safeguarding data and customer privacy in Generative AI applications
- How Japan balances AI-driven opportunities with cybersecurity needs
- Deploying SASE: Benchmarking your approach


