
(Source – Shutterstock)
Manufacturing and tech industries caught in the crosshairs of the evolving threat landscape
- Ransomware heavily targeted the technology sector in Q4 2022, and there are indications that it may target large IT providers in 2023.
- The use of new technologies, such as ChatGPT, may contribute to the further democratization of cybercrime, leading to the emergence of new threats.
In 2022, the global threat landscape was shaped by economic and political uncertainty due to Russia’s war on Ukraine, resulting in a volatile and fragmented environment. Towards the year’s end, ransomware attacks peaked, impacting several industries, including manufacturing, healthcare, technology, and telecommunications.
Kroll, a leading provider of global risk and financial advisory solutions, published its Q4 2022 Threat Landscape Report, which revealed that phishing and unauthorized access remained highly active threats throughout the year, with the latter rising from 18% to 25% of reported incidents.
Tech and manufacturing caught in the crosshairs in the threat landscape
Kroll’s Q4 2022 Threat Landscape Report reveals that professional services, healthcare, financial services, manufacturing, technology, and telecommunications were the top five impacted sectors in 2022. While professional services remained the most targeted sector, there was a slight decrease in attacks on this sector since 2021, with other sectors like manufacturing and technology and telecommunications seeing an increase in attacks.
Kroll has also observed many attacks on managed service providers (MSPs) in the technology industry, with threat actors using Google Ads to target IT administrators and MSPs with a legitimate software package that contained a Batloader installer.
The installer provided a backdoor with elevated privileges to the network, allowing the threat actor to extract data from several file servers and exfiltrate it to cloud data storage via Rclone. The execution of the Black Basta ransomware binary caused complications and likely disrupted the daily operations of the MSP, leading to increased pressure to pay the ransom.
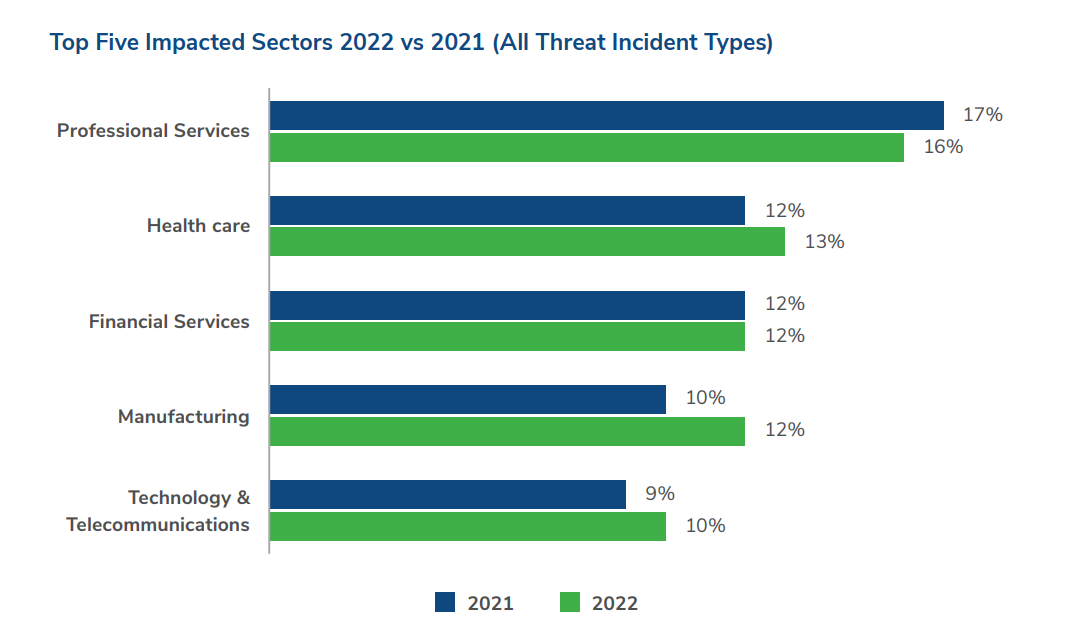
According to Kroll’s Q4 2022 Threat Landscape Report, the sectors most impacted by cyber threat incidents in 2022 include professional services, healthcare, and financial services.
Other key findings in the report include:
- Manufacturing experienced a 25% upsurge in ransomware incidents in Q4, as attackers sought to capitalize on the threat to business continuity.
- LockBit has overtaken Conti as the most common ransomware variant of 2022.
- Email compromise was the most common threat type in 2022 (similar to 2021), followed by ransomware and unauthorized access.
Kroll’s observations during Q4 of 2022 align with the year’s trend, where numerous familiar threats continue to evolve and change. This growth was evident in the prevalence of ransomware throughout the year, initially impacting healthcare in Q2, followed by education in Q3, before a significant increase in technology and manufacturing in Q4.
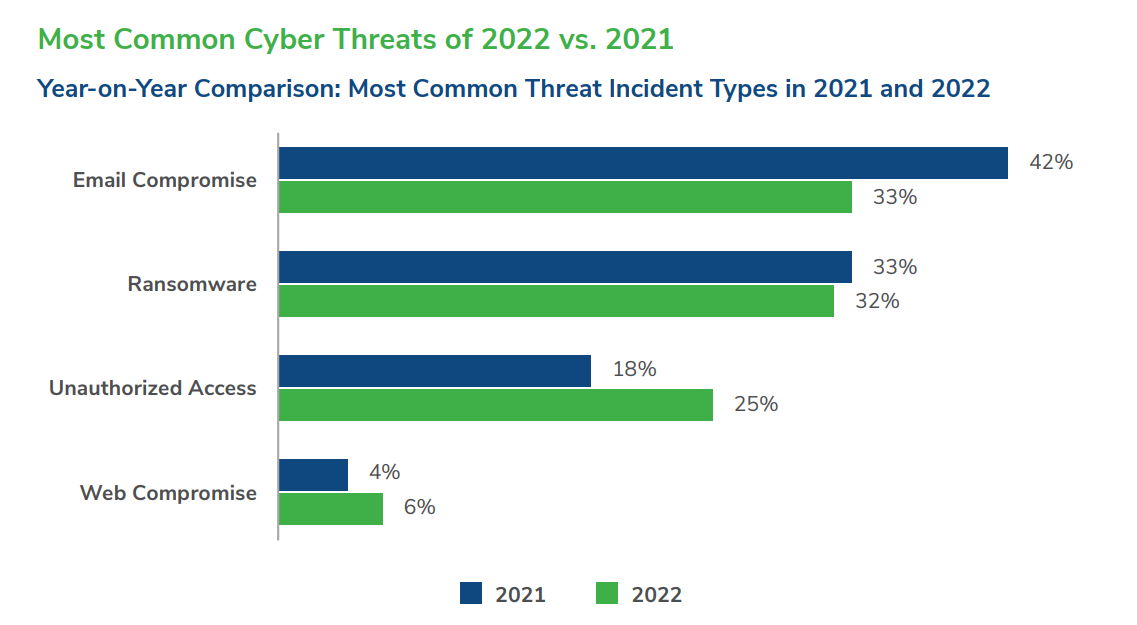
Kroll’s report also noted a large year-on-year increase in unauthorized access in 2022, and found that insider threat accounted for the majority of that activity.
The main narrative of 2022 has been cybercriminals’ ability to adapt quickly and regroup despite advancing security measures, law enforcement action, and geopolitical disturbances. The seamless transition from maldocs to container files in phishing attacks and the use of new access tactics, like Google Ads abuse, highlights the continual evolution of techniques organizations need to improve their defenses against new and emerging threats.
Organizations can achieve cyber resilience in the coming year by integrating real incident-based threat intelligence into their security response operations technology and teams.
Threats likely to evolve in form and focus
According to Kroll’s report, the factors that enabled cyber attackers to flourish in 2022, such as market volatility and geopolitical unrest, will likely persist in 2023. Furthermore, the increasing accessibility of cybercrime due to technological advancements, such as ChatGPT, could create new threats.
Paul Jackson, the Regional Managing Director of Asia Pacific Cyber Risk at Kroll, suggested that ransomware-as-a-service groups may seek to maximize their revenue streams in 2023, and thus ransomware actors may become more destructive, despite the decline in cryptocurrency value and average ransomware profits last year.
“Following on from the technology sector being a major target of ransomware in Q4 2022, large IT providers are likely to be a target in 2023, as threat actors attempt to use them to compromise end clients via supply chain attacks. An increase in attacks against operational technology (OT) environments is also highly probable, as is the use of techniques similar to those used in 2022,” he explained.
Therefore, he said that having a strong managed detection and response program will be critical in helping organizations respond effectively to the various threats that may emerge in 2023.
“Businesses can implement specific changes themselves, or with assistance from trusted retained cyber risk consultants,” he added. “These include enforcing multi-factor authentication, using remote desktop protocol (RDP), creating multiple backups and having effective access control.”
By taking proactive measures now, businesses can better equip themselves to handle the challenges ahead in 2023 and beyond.
READ MORE
- Ethical AI: The renewed importance of safeguarding data and customer privacy in Generative AI applications
- How Japan balances AI-driven opportunities with cybersecurity needs
- Deploying SASE: Benchmarking your approach
- Insurance everywhere all at once: the digital transformation of the APAC insurance industry
- Google parent Alphabet eyes HubSpot: A potential acquisition shaping the future of CRM


