
Source – Palo Alto Networks
From code to cloud: Achieving comprehensive application security in the cloud-native era
- Many organizations aim to improve cloud security by consolidating capabilities and addressing risks earlier in the development process.
- The growing use of pre-existing software in cloud application development increases the risk of vulnerabilities that could impact the entire application.
As cloud-native application development continues to evolve, organizations face increasing challenges in ensuring robust and effective application security in the cloud amid the constantly changing and hard-to-predict security landscape. The shift towards hybrid work has only hastened this transformation and further complicates infrastructure vulnerabilities.
In response, organizations’ cloud infrastructure is also changing accordingly. Furthermore, the cloud has disrupted the traditional lifecycle of applications, with DevOps delivering production code at a rapid pace, adding to the complexity of ensuring proper security measures are in place.
The state of cloud-native security
These challenges are highlighted in Palo Alto Networks’ 2023 State of Cloud-Native Security Report, which surveyed over 2,500 C-level executives worldwide on their cloud adoption strategies and the effectiveness of those strategies. With most organizations struggling to automate cloud security and mitigate risks, many seek to improve security earlier in the development process and consolidate security capabilities by working with fewer vendors.
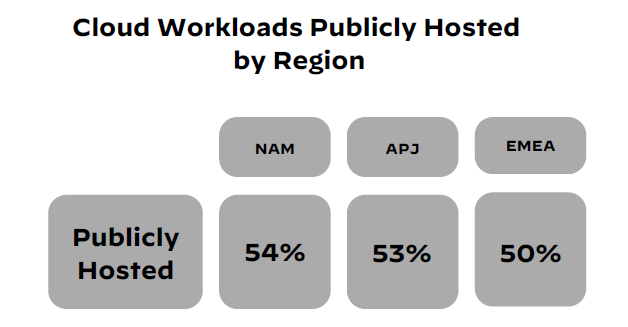
Cloud migration continues to expand, with more and more organizations opting for public hosting of their cloud workloads in 2023, just as they have done in previous years. The percentage of cloud workloads hosted on public clouds has risen by 8% in the last year, reaching 53%. The preferred application execution environments are platform as a service (PaaS) and serverless.
According to Palo Alto’s research, there are no significant differences in the percentage of cloud workloads hosted publicly among North America (NAM), Asia Pacific and Japan (APJ), and Europe, the Middle East, and Africa (EMEA) regions.
Source – Palo Alto Networks
Cloud migration does not always involve the development of cloud-native applications. The two most commonly utilized approaches for application deployment to the cloud are lift and shift and cloud-native, both preferred over rebuilding or refactoring, with a 10% preference margin.
For the first time, cloud-native deployment is leading the way in application development. The cloud deployment pattern varied across the three regions, with NAM having a greater proportion of cloud-native development compared to APJ and EMEA. APJ was almost equally split between the three approaches, while EMEA had the highest percentage of lift and shift among the regions.
Achieving comprehensive security for cloud-native applications
Firstly, managing security holistically across teams and breaking down silos is crucial to achieving comprehensive security. Collaboration and shared responsibility among development, operations, security teams, and all stakeholders involved in the application development lifecycle are essential, regardless of the quality of security tools. The trend today is shift-left security, which involves identifying and preventing vulnerabilities at the source before deployment, requiring aligned teams and security products that provide value to everyone involved.
Secondly, embedding the right cloud security solutions at every stage of the application development process, from code to runtime, is vital. According to its data, organizations are constantly adding new tools to their arsenal.
Thirdly, a significant issue is a lack of visibility into security vulnerabilities across cloud resources. To effectively manage vulnerabilities, cloud security solutions must be capable of detecting misconfigurations, vulnerabilities, and threats in real-time, rather than only scanning periodically. This allows organizations to respond quickly and effectively to breaches or vulnerabilities. Achieving this level of continuous monitoring requires security that matches the scale, speed, and agility of the cloud itself.
Integrating security professionals in DevOps teams for greater involvement
As the number of applications developed in the cloud using pre-existing software increases, there is a higher likelihood that a vulnerability in the development process may jeopardize the entire application in the future. To mitigate this risk, more companies are encouraging greater involvement between application developers, security tools, and teams. The report shows 81% of respondents have integrated security professionals within their DevOps teams to achieve this.
“With three out of four organizations deploying new or updated code to production weekly, and almost 40% committing new code daily, no one can afford to overlook the security of cloud workloads,” said Ankur Shah, senior vice president, Prisma Cloud, Palo Alto Networks. “As cloud adoption and expansion continues, organizations need to adopt a platform approach that secures applications from code to cloud across multicloud environments.”
READ MORE
- Ethical AI: The renewed importance of safeguarding data and customer privacy in Generative AI applications
- How Japan balances AI-driven opportunities with cybersecurity needs
- Deploying SASE: Benchmarking your approach
- Insurance everywhere all at once: the digital transformation of the APAC insurance industry
- Google parent Alphabet eyes HubSpot: A potential acquisition shaping the future of CRM


