
Here’s what we know about the Razer “data breach” so far
- Razer faces a potential data breach with its digital currency, Razer Gold, under scrutiny.
- The breach highlights the increasing cybersecurity threats in the gaming industry.
- The situation underscores the predicament of companies dealing with ransom demands from hackers.
Razer, a company that has previously grappled with data breaches, is currently under scrutiny for another possible breach. This time, the threat involves its Razer Gold digital currency. This situation echoes an incident from 2020, where a security oversight resulted in the unintentional disclosure of personal details, including addresses and phone numbers, from over 100,000 accounts.
The information of this potential breach initially surfaced through a Twitter user, @FalconFeedsio. According to the tweet, a hacker using a hacker forum alleges possessing Razer’s database, source code, encryption key, and more. The same gaming firm suffered a data leak back in 2020. However, the credibility of this recent claim is yet to be substantiated.
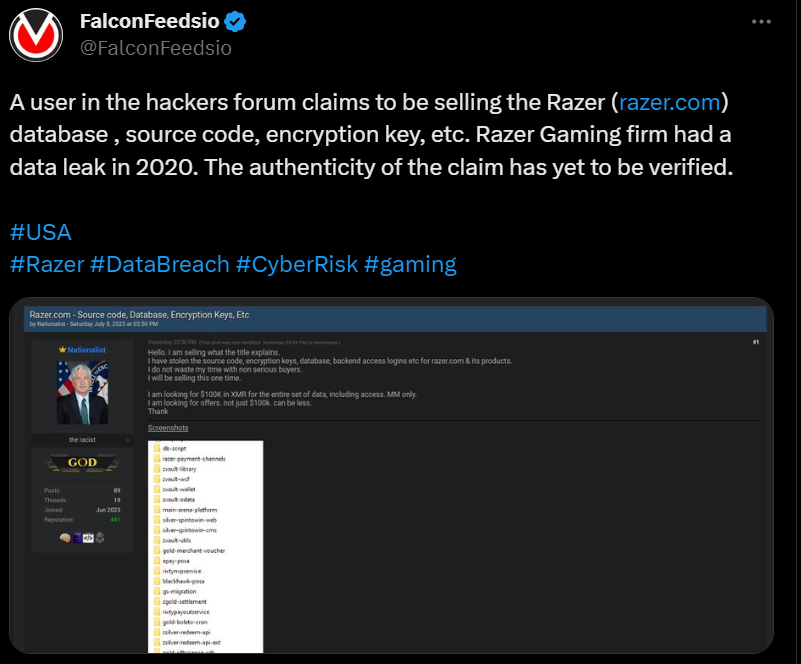
Potential data breach? A Twitter user, @FalconFeedsio, highlighted that a user in the hackers forum claims to be selling the Razer database. (Source – Twitter)
Interestingly, the alleged hacker seeks payment in the form of Monero, a type of cryptocurrency renowned for providing absolute anonymity for its users. The asking price is a staggering US$100,000 for the complete package. Unlike most mainstream cryptocurrencies, Monero’s transactions can’t be tracked or verified due to its advanced privacy technologies.
Razer has acknowledged the problem and promptly issued a statement: “We were alerted to a potential hack on July 9, 2023 impacting Razer Gold. Upon learning about the breach, the team immediately conducted a thorough review of all Razer’s websites and have taken all necessary steps to secure our platforms. Razer is still in the midst of investigations, and we remain committed to ensuring the digital safety and security of all our customers. Once investigations have concluded, Razer anticipates that we will report this matter to the relevant authorities.”
Razer Gold serves as a universal virtual credit system for gamers worldwide, facilitating purchases in more than 42,000 games and entertainment platforms, including popular titles like Clash of Clans, Genshin Impact, and on platforms like the Nintendo eShop. Users of Razer Gold accumulate rewards in the form of Razer Silver, which can then be used to acquire or avail discounts on Razer products. However, the specifics of the impact of this potential breach on Razer Gold – whether it affects their website or the digital wallets – remain uncertain.
The current breach, if confirmed, has some similarities with and stark differences to the previous one. During the prior incident, a server misconfiguration exposed the personal and shipping details of nearly 100,000 global Razer customers. Following this breach, Razer took its IT vendor Capgemini to court. The lawsuit stemmed from an incident where a former Capgemini employee inadvertently altered a line of code, leading to a security compromise.
Consequently, data within the system was exposed to the public between June 18, 2020, and September 10, 2020. Razer secured a compensation amount of US$6.5 million from the High Court on December 9, 2022, for the mishap. However, Capgemini’s legal representatives lodged an appeal for nominal damages instead, arguing that despite being alerted to the breach five times by a cybersecurity consultant, Razer failed to act.
What the experts think about the ‘data breach’
Tech Wire Asia approached Phillip Ivancic, the APAC Head of Solutions Strategy at Synopsys Software Integrity Group, for his insights on the situation. Ivancic underscored an area of vulnerability often neglected: the crucial importance of safeguarding software development environments, mainly where source code resides.
Ivancic referred to this environment as a CI/CD (Continuous Integration / Continuous Development) pipeline. He explained, “This is where developers are always adding to and enhancing software and its underlying source code.”
The value of source code to potential attackers, Ivancic believes, is twofold:
- Intellectual property theft: The source code unveils the mechanics of a company’s products and the business processes underpinning the organization. If this information falls into the wrong hands, it could be of tremendous commercial value to attackers.
- Vulnerability Exploitation: Source code, once obtained, can be scrutinized offline to identify weaknesses and plan future attacks. Having the blueprint, attackers can gain a deep understanding of any inherent vulnerabilities, equipping them with the knowledge to design malicious exploits tailored to these software weaknesses.
“To effectively protect a CI/CD pipeline companies need to have an effective strategy and framework focused on CI/CD pipelines and security controls. Furthermore, companies should engage in sophisticated attack simulations (often referred to a Red Team exercise) to ensure the security controls on their software development pipelines are effective against a cunning adversary,” he concluded.
Here’s an explanation on how CI/CD pipeline works:
Satnam Narang, a senior staff research engineer at Tenable, also chimed in with his views on the situation. He pointed out that the recent purported attack on Razer highlights the critical role of data security. Threat actors gain unauthorized entry to sensitive data through several avenues, from exploiting weaknesses and utilizing social engineering tactics like spearphishing to misconfiguring cloud storage, targeting third-party associates, and launching supply chain assaults.
All organizations are susceptible to such threats, but leading companies like Razer are often in the crosshairs of cybercriminals.
“Though the investigation into the alleged breach is ongoing, we see that stolen data remains a lucrative business opportunity for all types of attackers,” he emphasized. “In ransomware, we see the theft of and threat to publish stolen, sensitive data, lead to ransom demands that range in the tens of thousands to the millions.”
Narang further indicated that in some situations akin to this one, the sellers adopt a modus operandi reminiscent of typical criminals peddling stolen jewelry from their coat pockets. These cyber miscreants aim for the most profitable deal. Yet, they are open to negotiating the price, prioritizing swift transactions, as possession of such stolen data often attracts the attention of law enforcement.
What does this mean for the gaming industry?
The recent security breach involving Razer Gold, a considerable one, sends ripples across the gaming industry. It doesn’t merely emphasize the business risks involved; it points out a grave threat to the industry’s consumer trust and overall stability.
Firstly, incidents like this bring to the forefront the intensifying cybersecurity challenges that gaming companies grapple with in the digital age. As the gaming industry swells and leans more heavily on digital currencies and online platforms for transactions, it inevitably becomes a larger target for cyber threats.
Cybercriminals see the gaming world as a potential goldmine, given how gamers regularly spend on character enhancements, tools, and aesthetic changes – microtransactions that, in aggregate, generate billions of dollars. A study by The Business Research Company anticipates the online microtransaction market to reach a staggering US$106.02 billion by 2026, representing an 11.9% CAGR. Furthermore, gaming communities are recognized for their philanthropy, with Twitch alone seeing charitable donations amounting to US$145 million between 2011 and 2019, which included an impressive US$42 million in 2019 alone.

What impact will a data breach cause to gamers? (Source – Shutterstock)
To threat actors, the gaming universe is laden with appealing targets. Hacking into user accounts could give them access to in-game currencies, assets, account information, or even entire gaming accounts. These loots can then be traded in the shadowy corners of the dark web. If they can breach the walls of a gaming company, they could snatch the source code, unravel game cheats, or even employ classic ransomware strategies to encrypt files and expose extracted data.
The second fallout of a breach like Razer’s could trigger a significant shift in the gaming industry’s approach to cybersecurity. It may call for a reevaluation and potential overhaul of current security practices, pressuring gaming companies to pour more resources into heightened security measures. These can range from stronger encryption to regular security audits and comprehensive employee training to bolster safeguarding sensitive data. The focus on the security of CI/CD pipelines, as highlighted by Ivancic, should be heightened in these efforts.
Furthermore, this breach may ignite discussions surrounding the security and practicality of employing digital currencies within gaming ecosystems. While digital currencies cater to users with a fluid and often rewarding transaction experience, they also introduce substantial security risks. This occurrence might stir a deeper delve into the advantages and disadvantages of digital currencies in gaming, prompting the industry to explore more secure ways of handling these platforms.
The use of online game currency could also act as a conduit for money laundering schemes. Malicious entities could open a game account, build a profile, and then use stolen funds or hacked credit card numbers to buy as much in-game currency and accessories as possible. The next step would be to sell their account to an innocent buyer, completing the money laundering cycle.
To pay or not to pay the ransom?
The potential breach at Razer has brought to the forefront a pivotal dilemma: should a company yield to the demands of a cyber attacker for a ransom or not? Companies grappling with this predicament often find themselves in a seemingly impossible situation with apparently no beneficial outcome, irrespective of their decision.
On one hand, the temptation to meet the ransom demands is substantial, as it offers the potential to regain access to the compromised systems and possibly stave off the exposure of sensitive data. However, paying the ransom could stimulate analogous attacks in the future, and there’s no certainty that the perpetrator will uphold their end of the bargain. It is crucial to remember that such attackers operate beyond societal laws and norms, making their assurances unreliable.
Alternatively, the decision to decline the ransom could potentially lead to the exposure of sensitive data, with repercussions including damage to the company’s reputation, loss of consumer trust, penalties from regulatory bodies, and more. Furthermore, the recovery costs following a cyberattack often surpass the original ransom amount.

Paying the ransom in the event of a data breach should never be an option. (Source – Shutterstock)
An integral component in this decision matrix is the nature of the compromised data. If the data is highly sensitive, like proprietary source code or client information, the company may feel an increased pressure to pay the ransom to inhibit its disclosure. However, such payment doesn’t guarantee that the data hasn’t been duplicated or that it won’t be maliciously exploited in the future.
In Australia, the stance on ransom payments is quite clear. The Australian Cyber Security Center (ACSC) strongly discourages companies from capitulating to such demands as they might sometimes be considered illegal. Under the Criminal Code Act 1995 and the Anti-Money Laundering and Counter-Terrorism Financing Act 2006, it’s deemed a grave offense to support or finance criminal activities. Therefore, paying a ransom could be construed as illegal and is advised against.
The most effective strategy for any company is to invest in preventative measures and establish robust cybersecurity protocols. This includes continuous monitoring, regular audits of systems, training of employees, and creating robust incident response plans. Coupled with cyber insurance, these measures can aid in reducing the chances of a breach and mitigate potential damages in the event of an attack.
READ MORE
- Building trust in the data economy: Enerlyf and Affinidi redefine CX, privacy and energy efficiency
- The threat of fraud networks in the APAC: KYC and beyond
- Next-gen CX is based on customer communication management systems.
- Enhancing Business Agility with SASE: Insights for CIOs in APAC
- 3 Steps to Successfully Automate Copilot for Microsoft 365 Implementation


